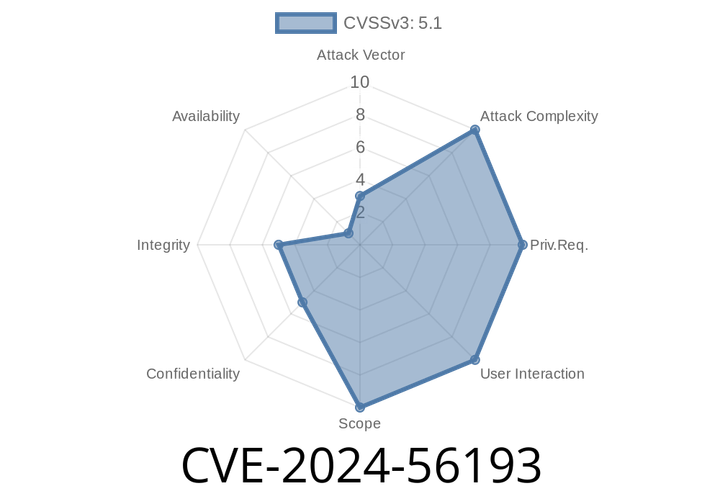
CVE-2024-56193 - Bluetooth Adapter Info Leak via Permissions Bypass
CVE-2024-56193 is a newly disclosed vulnerability affecting certain Android devices, allowing a malicious local app to read sensitive details about the device’s Bluetooth adapter
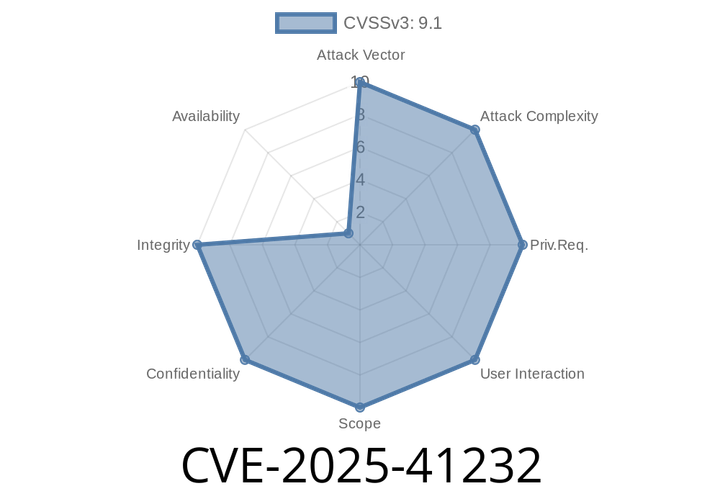
CVE-2025-41232 - Spring Security Authorization Bypass via Private Method Annotations – Explained and Exploited
A critical vulnerability was assigned as CVE-2025-41232, affecting Java applications using Spring Security's method-level security in a particular configuration. In this post, we’
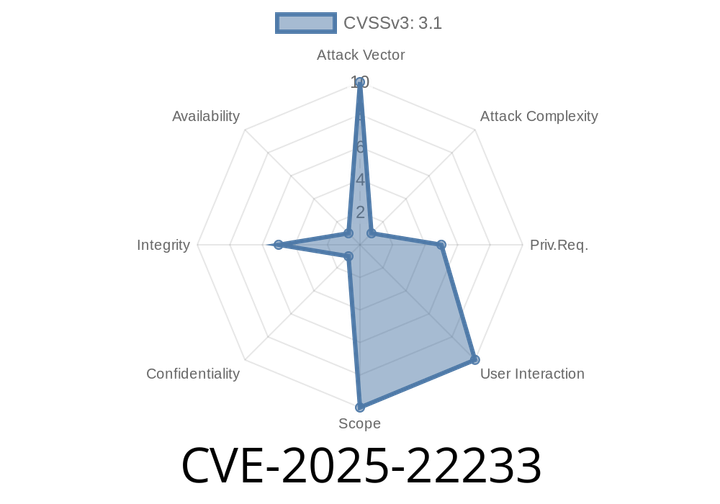
CVE-2025-22233 - Bypassing disallowedFields Checks in Spring Framework Data Binding
A new vulnerability, CVE-2025-22233, has been discovered in the Spring Framework. This issue is a follow-up to CVE-2024-38820, which tried to make sure both parameter
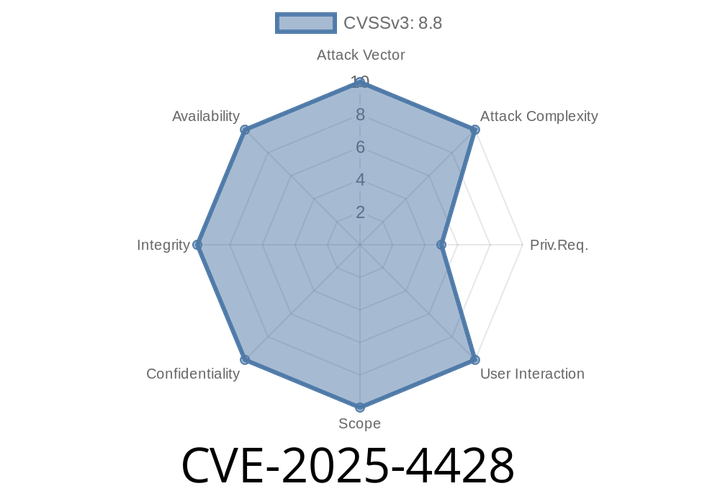
CVE-2025-4428 - Remote Code Execution in Ivanti Endpoint Manager Mobile (EPMM) API – Full Exploit Details and Analysis
Published: June 2024 <br>Author: Infosec Explainers
Overview
A new critical vulnerability CVE-2025-4428 has been discovered in Ivanti Endpoint Manager Mobile (EPMM) versions
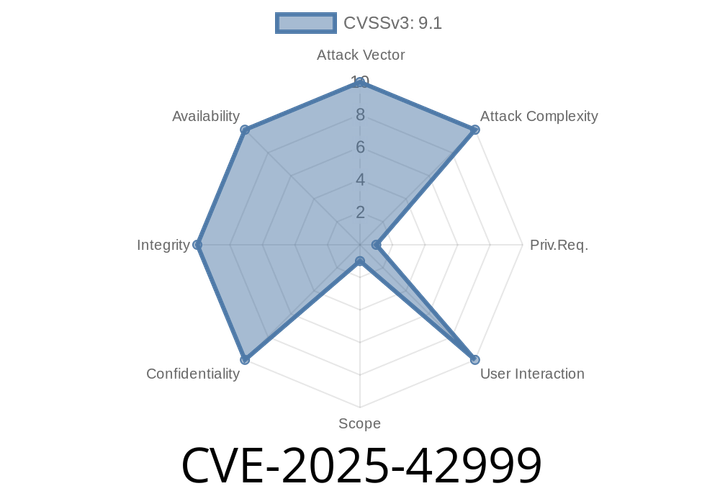
CVE-2025-42999 - SAP NetWeaver Visual Composer Metadata Uploader – Untrusted Deserialization Vulnerability Explained
CVE-2025-42999 is a newly discovered vulnerability in SAP NetWeaver Visual Composer (VC). This vulnerability lets a user with upload permissions—sometimes even an internal or
Episode
00:00:00
00:00:00