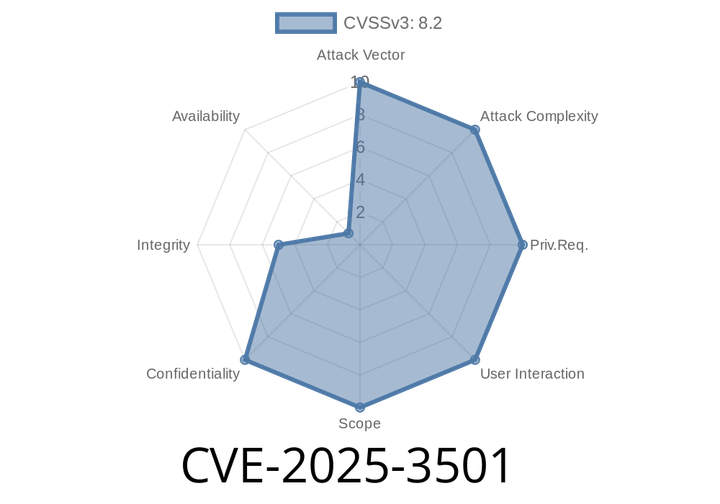
CVE-2025-3501 - How a Misconfigured Policy in Keycloak Skips Trust Store Verification (Full Analysis & Exploit Demo)
Keycloak is a widely used open-source identity and access management solution. It helps secure apps by handling login, SSO, role-based access controls, and more. In
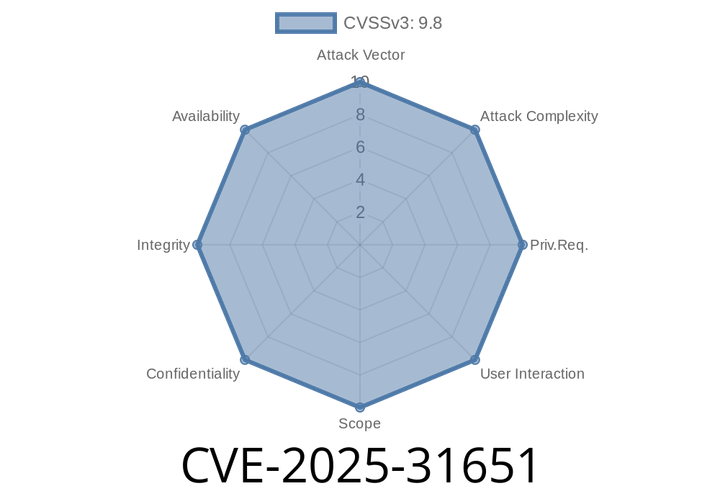
CVE-2025-31651 - Exploiting Rewrite Rule Bypass in Apache Tomcat — Details, Demo, and Defense
Apache Tomcat is one of the world’s most popular Java web servers. This spring, security researchers found a serious flaw — CVE-2025-31651 — that affects how
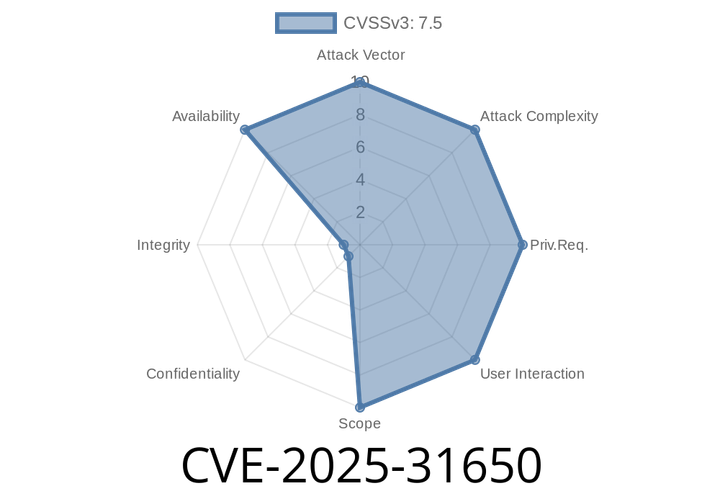
CVE-2025-31650 - Memory Leak and Denial of Service in Apache Tomcat via Broken HTTP Priority Headers
A newly disclosed vulnerability with the identifier CVE-2025-31650 has been discovered in Apache Tomcat, one of the most widely used Java web servers in the
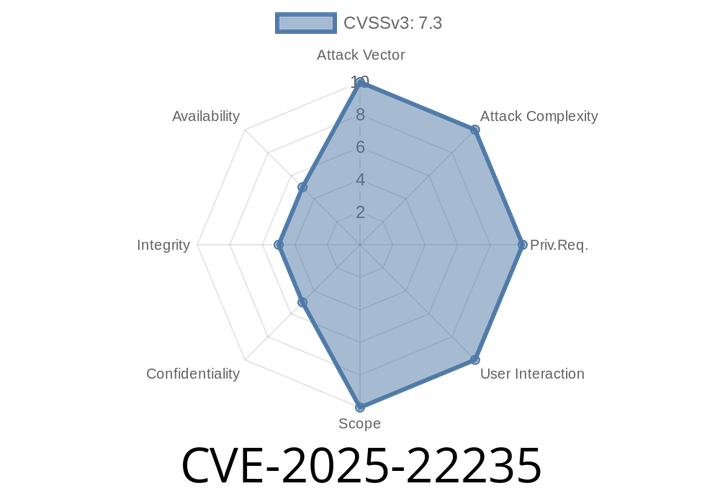
CVE-2025-22235 - Security Bypass in Spring Security EndpointRequest.to() When Endpoint is Disabled or Not Exposed
In early 2025, a new vulnerability was assigned as CVE-2025-22235, affecting applications that rely on Spring Security to protect application endpoints. This particular weakness is
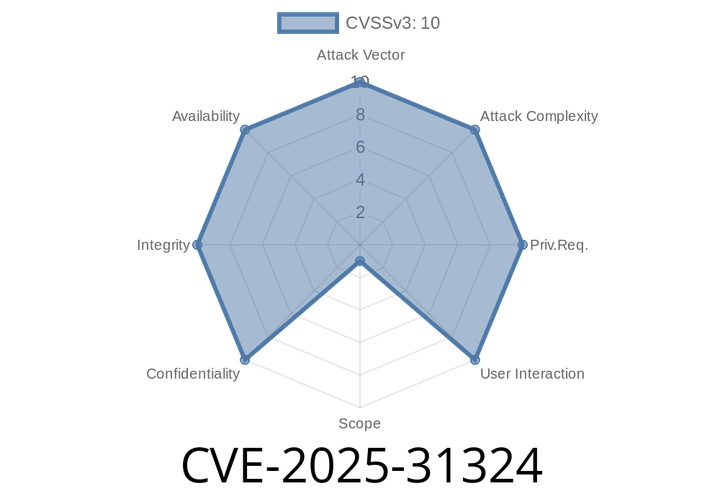
CVE-2025-31324 - SAP NetWeaver Visual Composer Metadata Uploader Unauthenticated File Upload – Deep Dive and Exploit
Summary:
A new vulnerability, CVE-2025-31324, has been identified in SAP NetWeaver Visual Composer. This flaw allows anyone—without any login or authentication—to upload files,
Episode
00:00:00
00:00:00