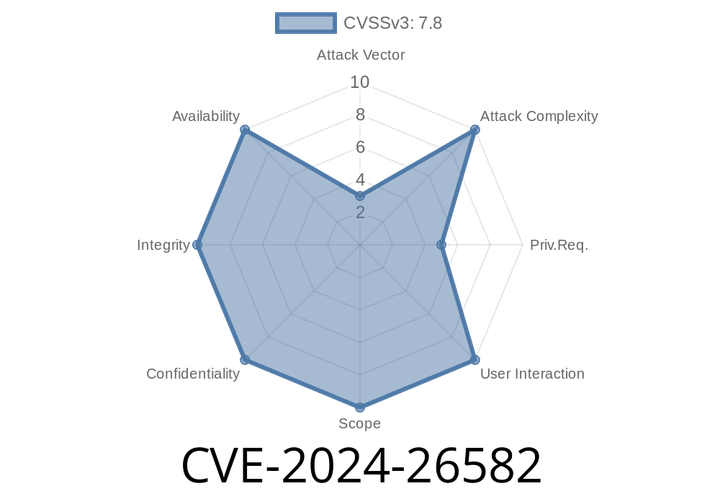
CVE-2024-26582 - Linux Kernel net/tls Use-After-Free Vulnerability Explained & Exploit Example
Published: June 2024
Status: Patched
Severity: Moderate-to-High
Affected Component: Linux Kernel net/tls module
What is CVE-2024-26582?
CVE-2024-26582 is a use-after-free vulnerability that was recently
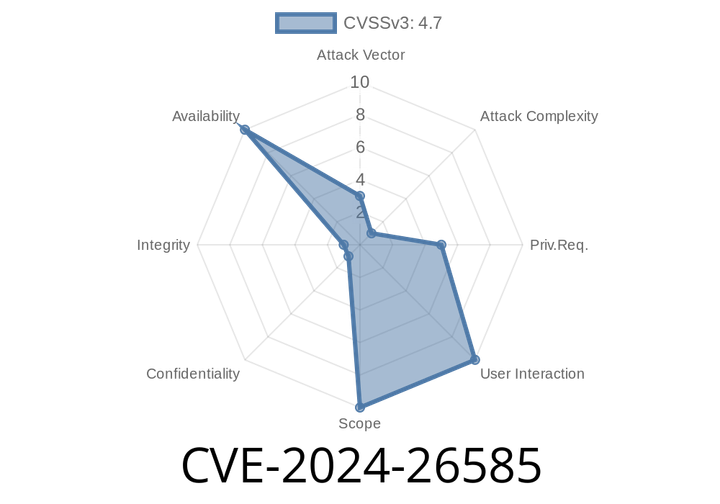
CVE-2024-26585 - Race Condition in Linux Kernel TLS - Exploit Scenario, Fix Details, and Example Code
---
Introduction
In February 2024, a serious vulnerability was identified and patched in the Linux kernel’s TLS (Transport Layer Security) stack. Tracked as CVE-2024-26585,
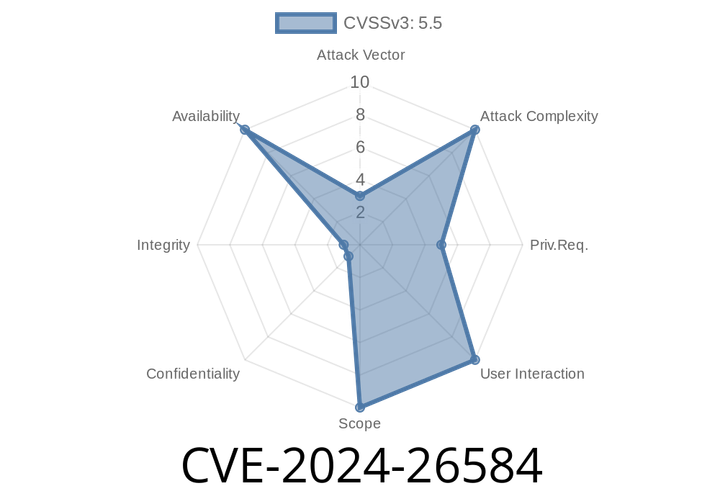
CVE-2024-26584 - Handling Crypto Request Backlogging in the Linux Kernel’s TLS Implementation
In early 2024, a subtle yet important vulnerability was addressed in the Linux kernel’s handling of TLS (Transport Layer Security) cryptographic requests. Known as
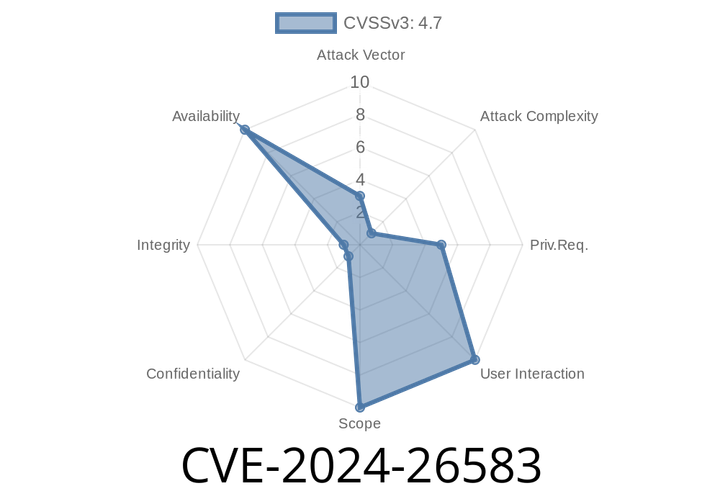
CVE-2024-26583 - Linux Kernel Async TLS Notify Use-After-Free Race Explained & Exploited
The Linux kernel, at the heart of just about every Linux system, occasionally faces subtle and critical bugs. One such issue, recently patched, is CVE-2024-26583.
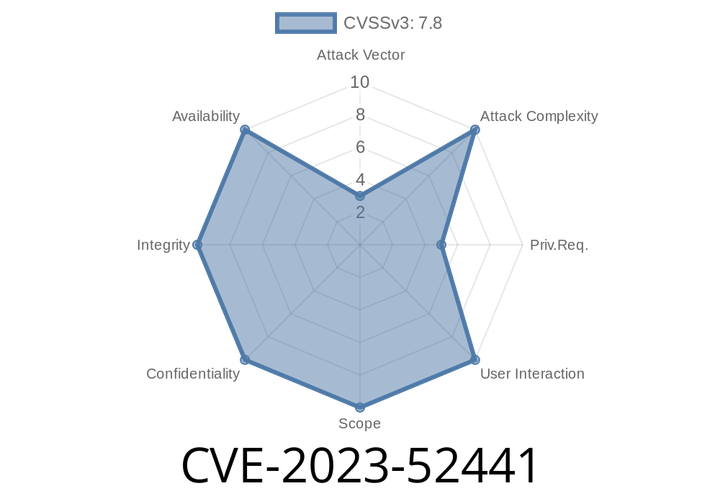
CVE-2023-52441 - Out-of-Bounds Vulnerability in Linux KSMBD – Root Cause, Exploit, and Patch Explained
The Linux kernel is the beating heart of millions of servers and devices worldwide, handling everything from laptops to huge cloud deployments. One of its
Episode
00:00:00
00:00:00