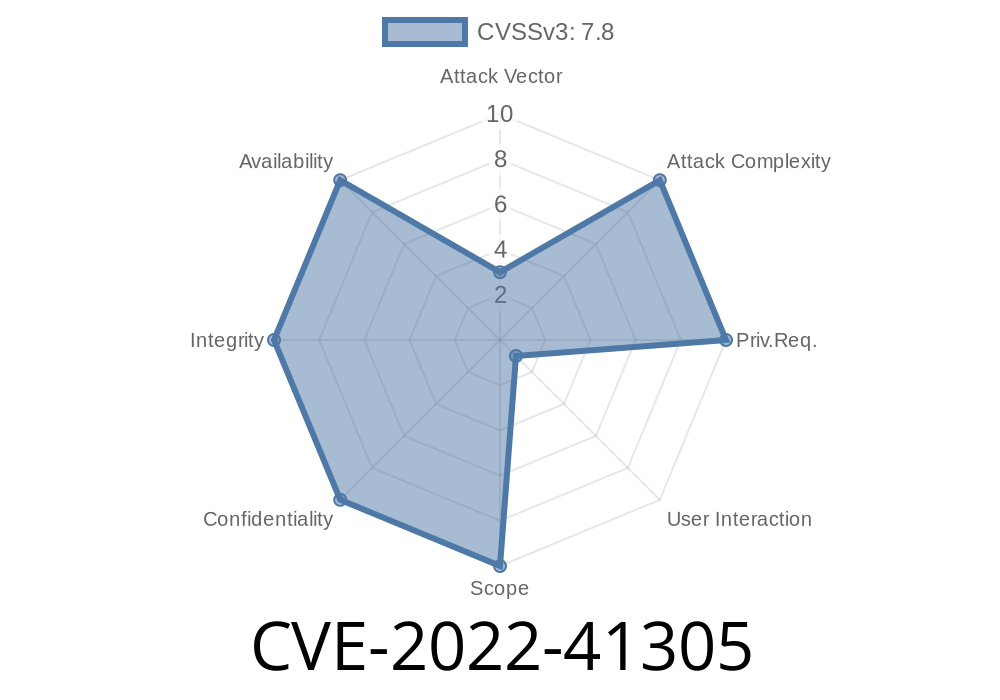
CVE-2022-41305 Malicious PKT file could lead to memory corruption vulnerability by write access violation.
SubassemblyComposer.exe application is commonly used to build custom SCCM packages, and it’s installed with Windows operating system. If an attacker successfully exploits this
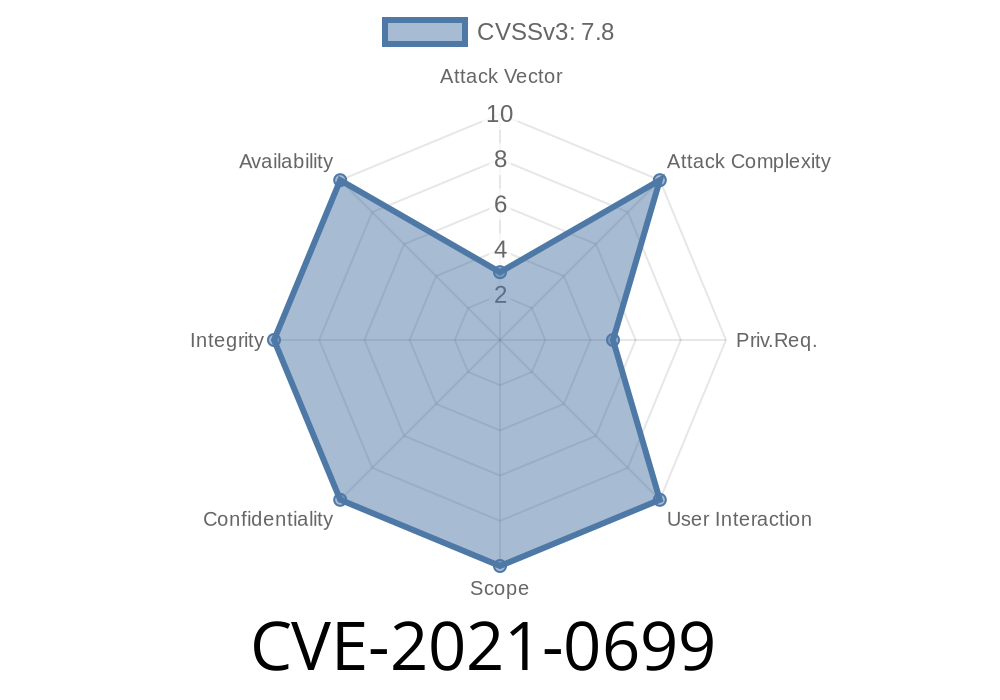
CVE-2021-0699 An out of bounds write in HTBLogKM could lead to local escalation of privilege in the kernel.
This issue exists because of a bug in the implementation of the bounds check. It can be exploited after gaining access to a privileged process.
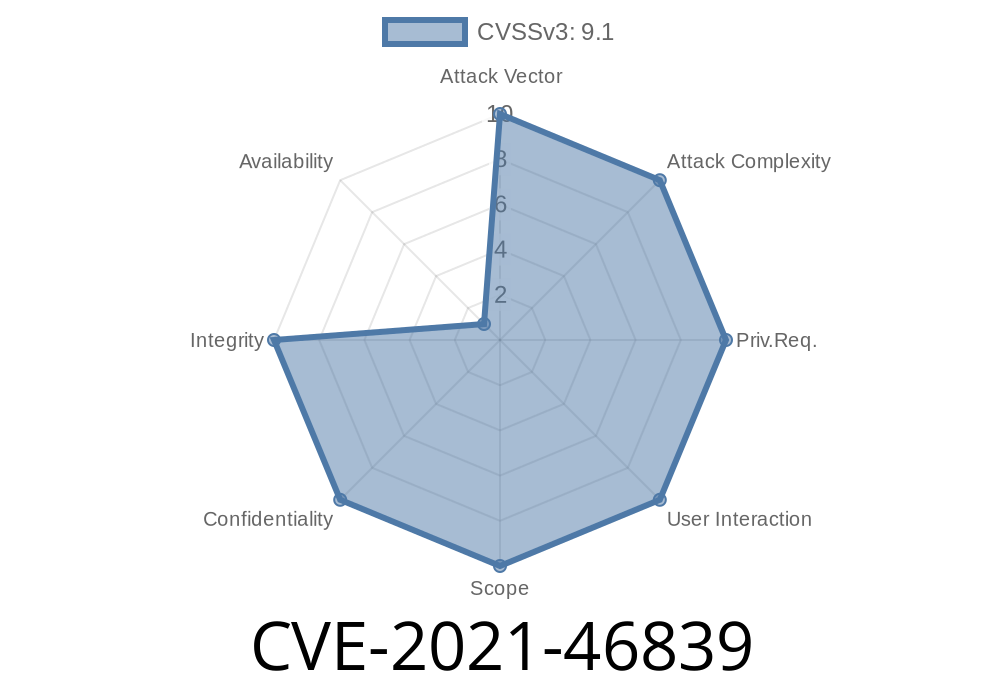
CVE-2021-46839 The HW_KEYMASTER module has a vulnerability of missing bounds check on length. Successful exploitation may cause malicious construction of data and out-of-bounds access.
The issue occurs as a result of insufficient validation of input data, which may lead to a crash and potentially allow a remote attacker to
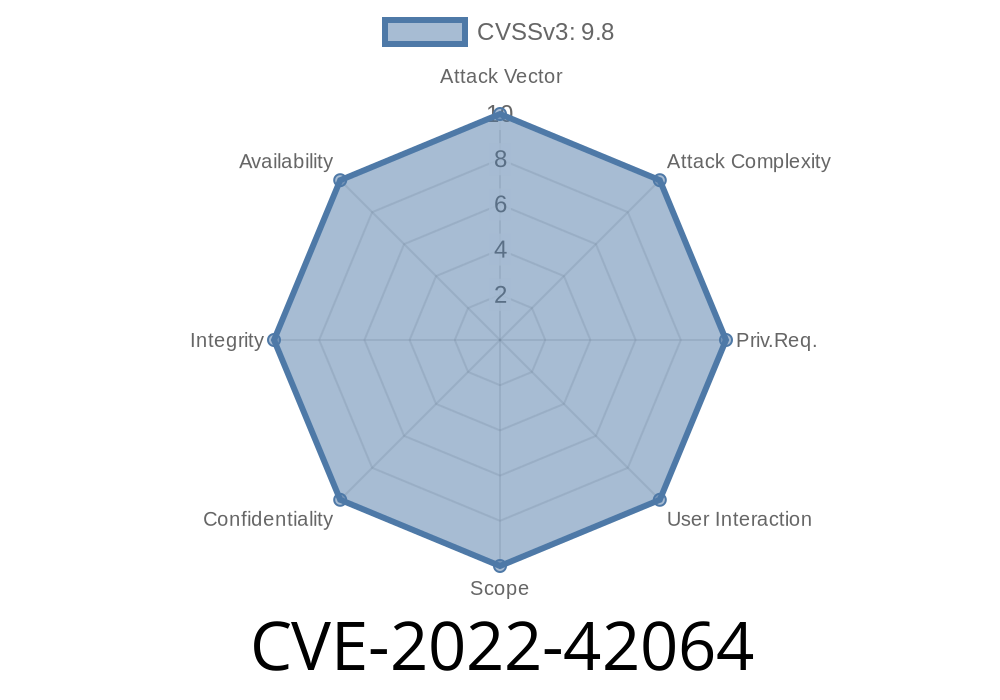
CVE-2022-42064 An attacker exploited a remote version 1.0 of the Lab Management System to upload a shell.
Once the attacker has control of the database, they can do anything they wish with the data. This can range from simply deleting the data,
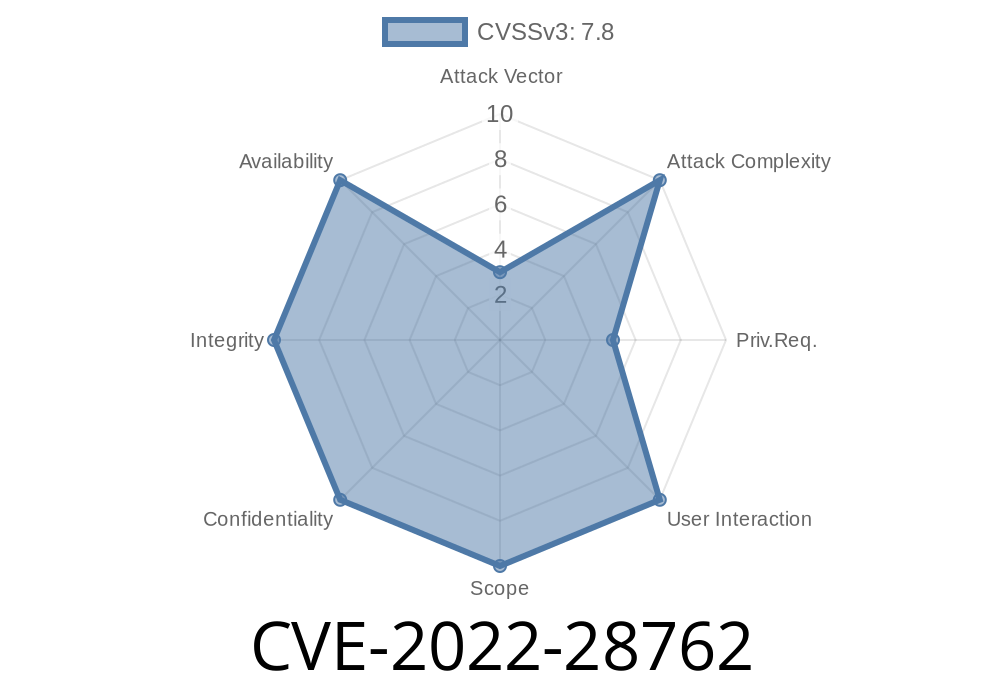
CVE-2022-28762 The Zoom Client for Meetings for Macs starting with 5.10.6 has a misconfiguration of a debugging port.
This could be used for example to launch other malware or perform other potentially unwanted actions. Zoom for meetings is a collaborative presentation and meeting
Episode
00:00:00
00:00:00