CVE-2025-27517 - Remote Code Execution in Volt for Livewire Explained
CVE-2025-27517 uncovers a critical vulnerability in Volt, the popular functional API package tightly integrated with Livewire for Laravel. This vulnerability, found in Volt versions before
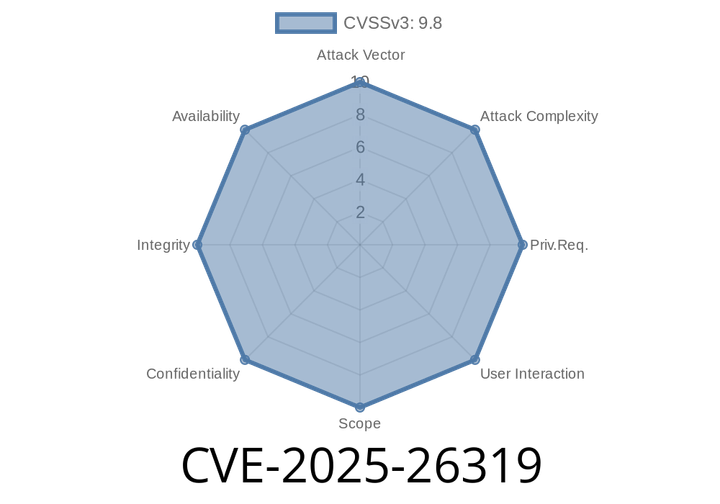
CVE-2025-26319 - Breaking Down FlowiseAI v2.2.6’s Arbitrary File Upload Vulnerability
FlowiseAI has recently been in the spotlight with the discovery of a severe vulnerability—CVE-2025-26319—affecting its v2.2.6 release. This vulnerability allows attackers
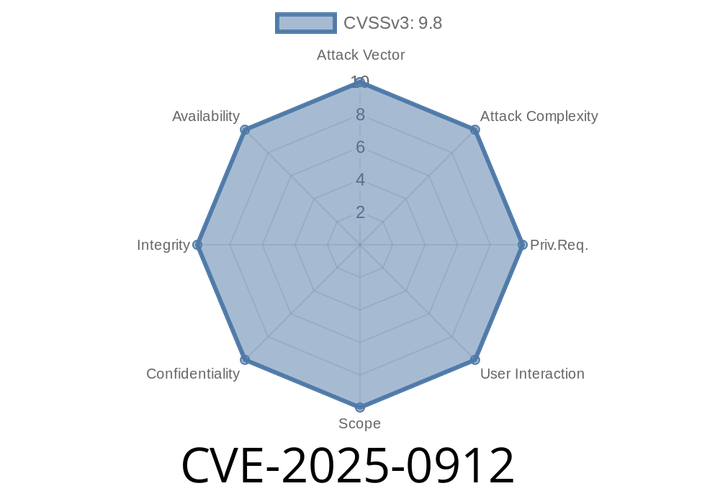
CVE-2025-0912 - Critical PHP Object Injection and RCE in Donations Widget WordPress Plugin (Up to 3.19.4)
WordPress is all about making things easier, from blogging to taking donations. But sometimes, plugins built to help can be a big risk. One such
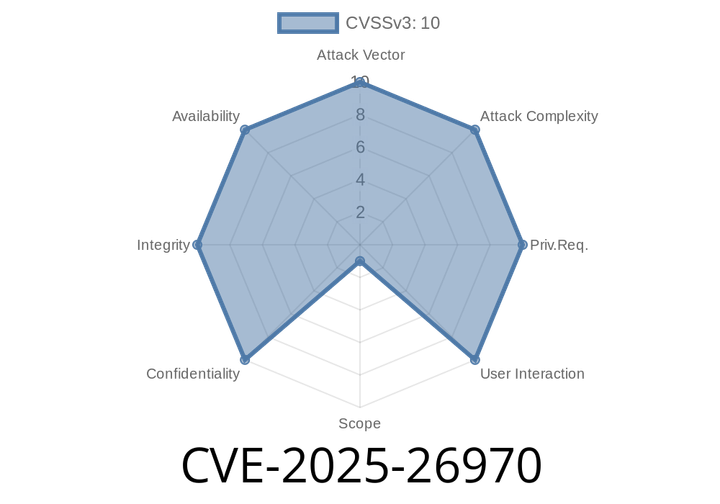
CVE-2025-26970 - Code Injection Vulnerability in NotFound Ark Theme Core (Up to 1.70.) — A Complete Guide
On May 2025, security researchers discovered a major vulnerability—CVE-2025-26970—in the popular Ark Theme Core plugin by NotFound. This vulnerability lets attackers inject their
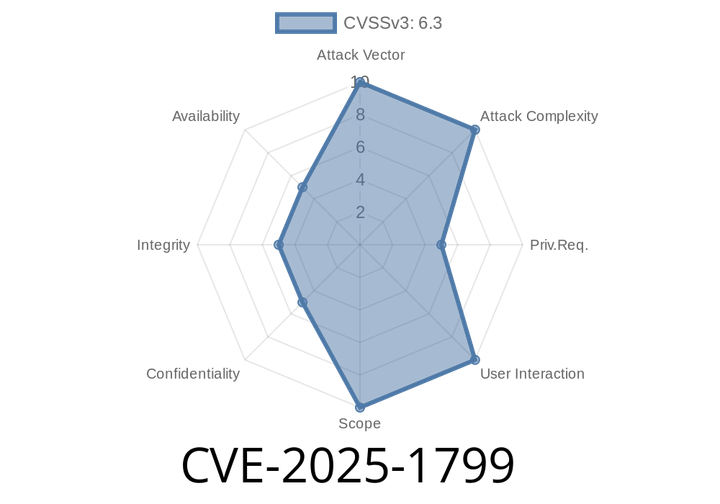
CVE-2025-1799 - Critical SSRF Vulnerability in Zorlan SkyCaiji 2.9 – Detailed Analysis and Exploit
Zorlan SkyCaiji is a popular web scraping and content collection system used by many organizations for managing large-scale data gathering. On June 13, 2024, a
Episode
00:00:00
00:00:00