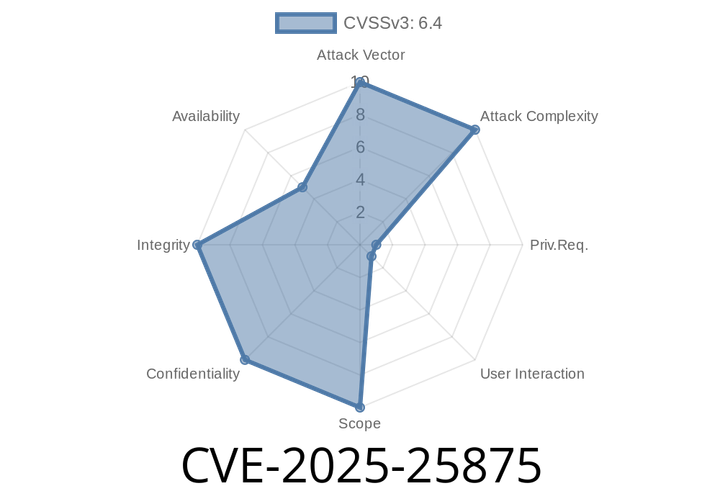
CVE-2025-25875 - SQL Injection Vulnerability in ITSourcecode Simple ChatBox ≤ 1. – Exploit Details and Remediation Guide
The digital world relies on the security of web applications, but sometimes even simple chat scripts can open the door to serious risks. One such
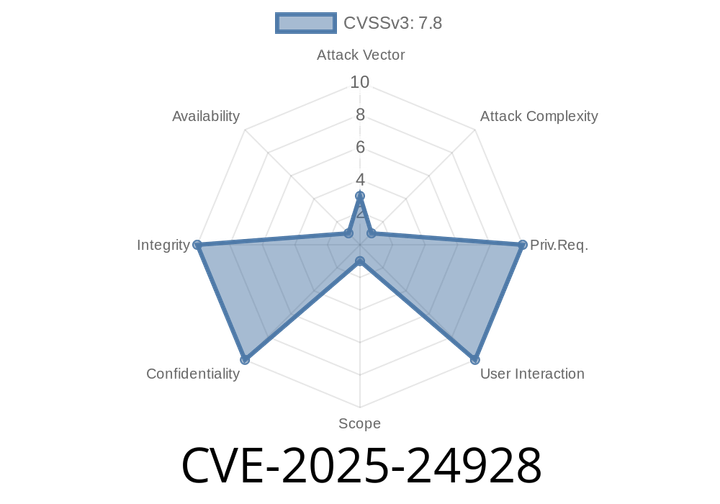
CVE-2025-24928 - Stack Buffer Overflow in libxml2’s xmlSnprintfElements Explained (Pre-2.12.10 & 2.13.6) with Exploit Details
A high-severity vulnerability was discovered in the popular XML parsing library libxml2. Tracked as CVE-2025-24928, this flaw could let attackers run code on your system
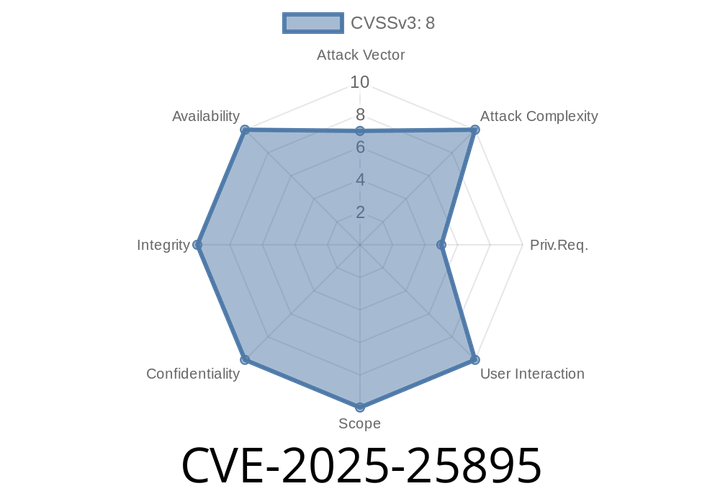
CVE-2025-25895 - Command Injection in D-Link DSL-3782 (v1.01) Explained, With Exploit Details
D-Link has repeatedly found itself in the crosshairs of researchers due to various security weaknesses in its networking gear. In this exclusive post, we dive
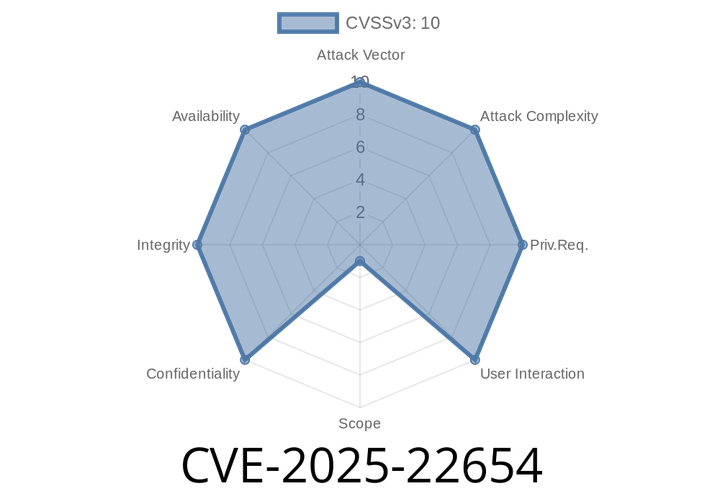
CVE-2025-22654 - Unrestricted Upload of Dangerous Files in kodeshpa Simplified (All Versions up to 1..6)
A serious security vulnerability, CVE-2025-22654, has been discovered in kodeshpa Simplified, a popular content management system used for website building and management. This vulnerability makes
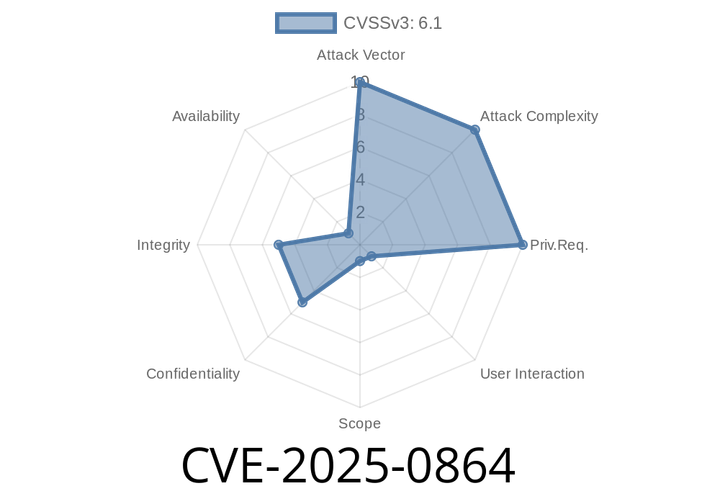
CVE-2025-0864 - Reflected XSS Vulnerability in Active Products Tables for WooCommerce Plugin (All Versions ≤ 1..6.6) Explained
If you’re running a WordPress online store with WooCommerce, you might be using Active Products Tables for WooCommerce to display product listings. However, a
Episode
00:00:00
00:00:00