CVE-2022-42187 - XSS Vulnerability in Hustoj 22.09.22 – Exploit Details and Code Walkthrough
In September 2022, a Cross-Site Scripting (XSS) vulnerability was discovered in Hustoj, a popular open-source Online Judge platform (version 22.09.22). The flaw exists
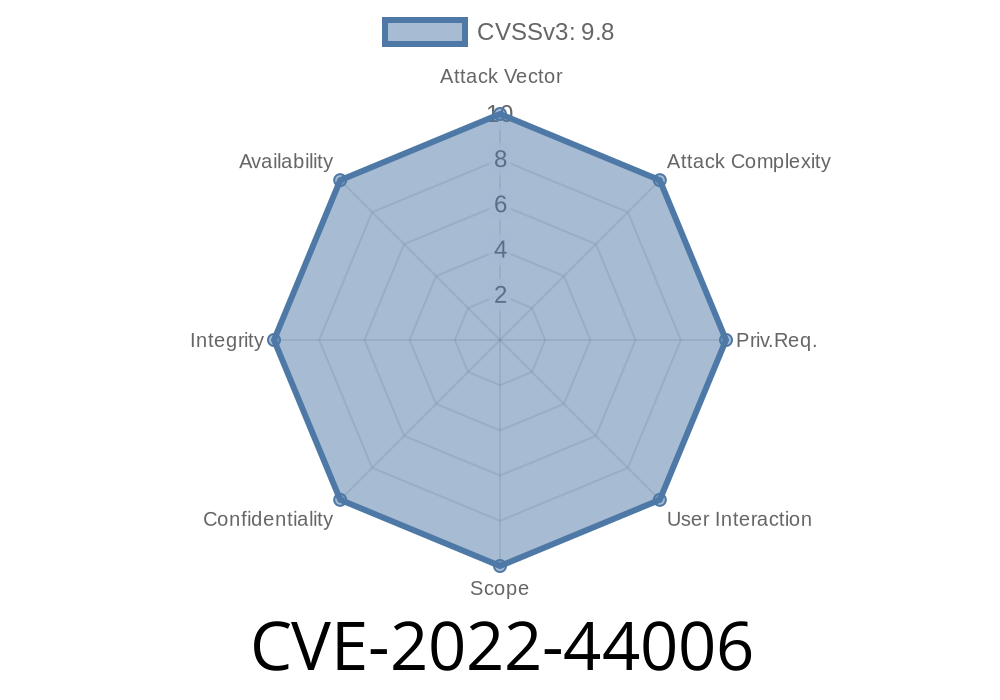
CVE-2022-44006 An issue was found in BACKCLICK 5.9.63, which has a validating and sanitizing issue that allows uploading files to unintended locations.
For example, a user uploads a PHP code file named “ calc.php” and another user with write access to that directory could overwrite that file
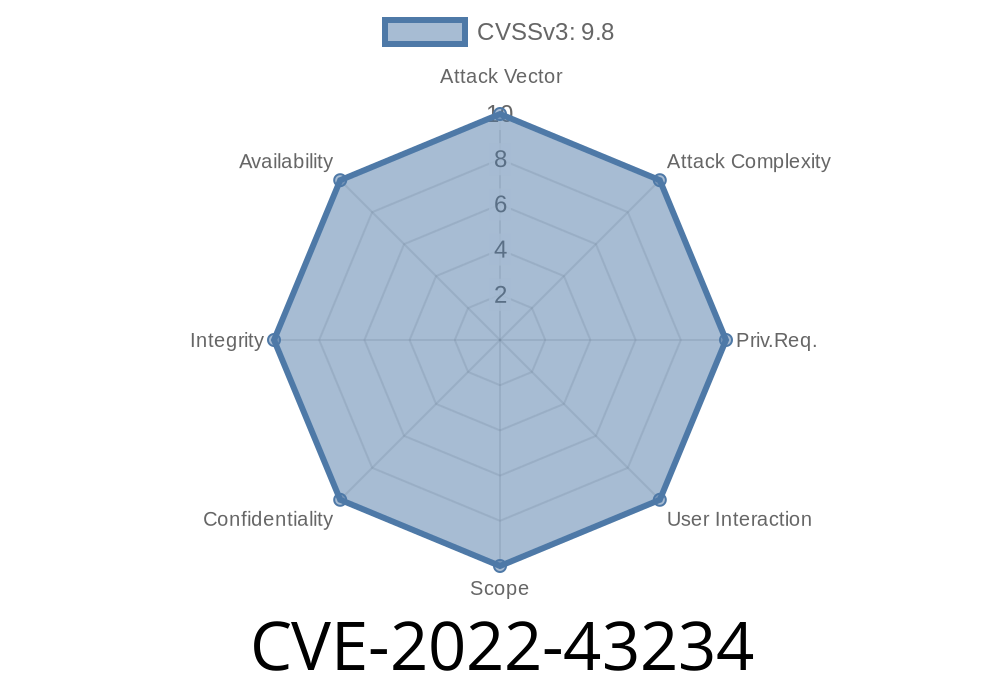
CVE-2022-43234 An arbitrary file upload vulnerability in the /attachments component of Hoosk v1.8 allows attackers to execute arbitrary code.
This vulnerability can be exploited by uploading a specially crafted file to /attachments. An attacker can upload a PHP shell script or use another method
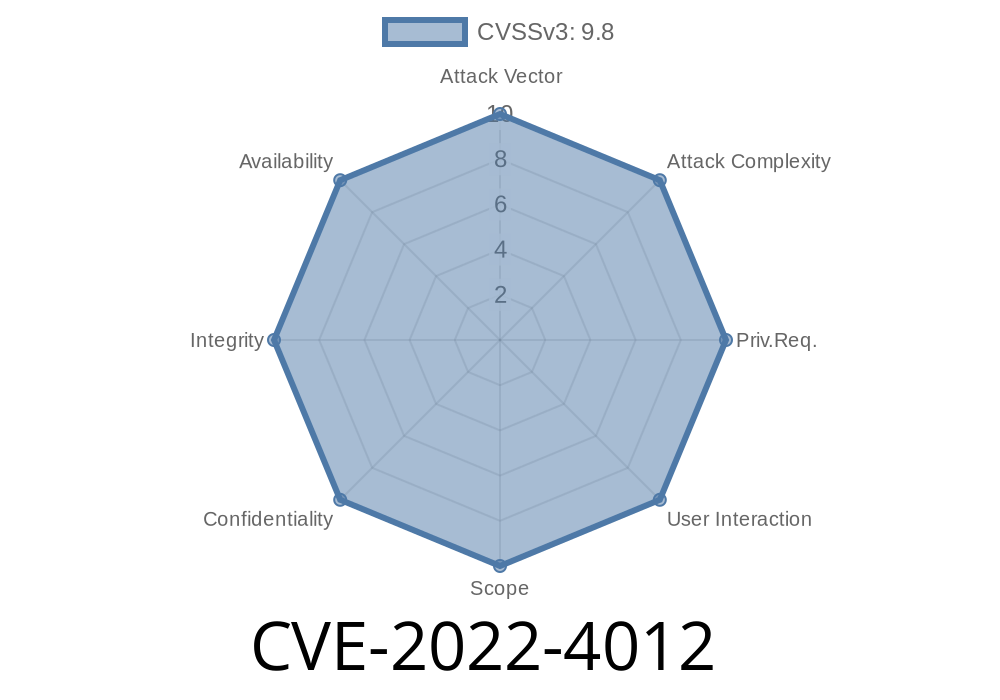
CVE-2022-4012 - Critical SQL Injection in Hospital Management Center (patient-info.php pt_id Exploit)
The cybersecurity world is constantly finding vulnerabilities, but sometimes one stands out for its simplicity and potential impact. CVE-2022-4012 is one of these dangerous flaws.
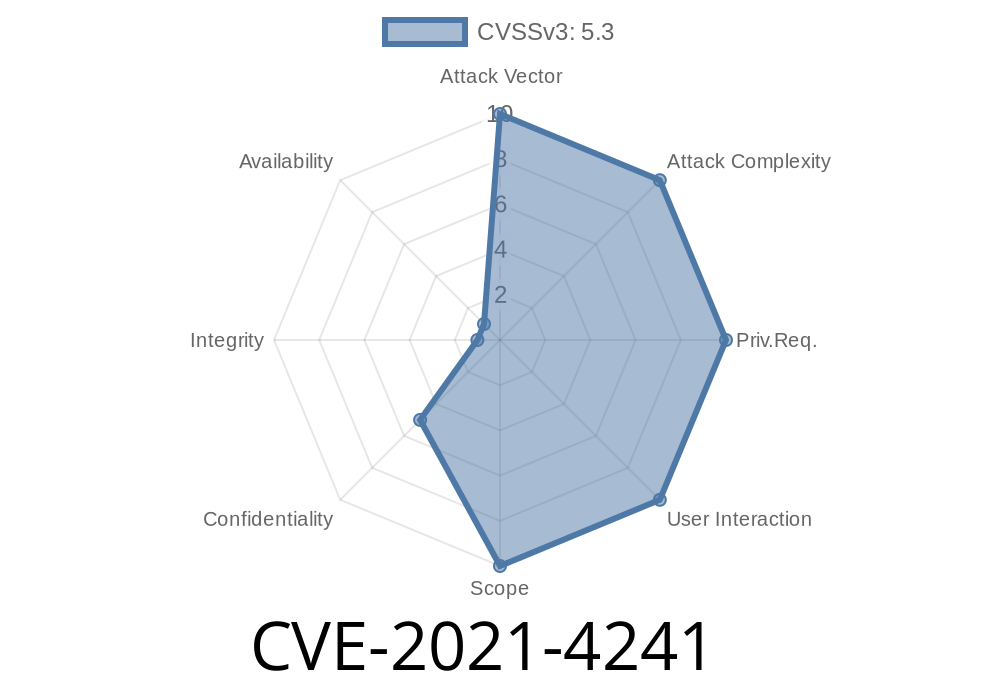
CVE-2021-4241 - Predictable Session Token Vulnerability in phpservermon (VDB-213744) — Exploit Details and Patch Guidance
In late 2021, a vulnerability identified as CVE-2021-4241 was discovered in the popular server monitoring tool, phpservermon. This issue, classified as "problematic," impacts
Episode
00:00:00
00:00:00