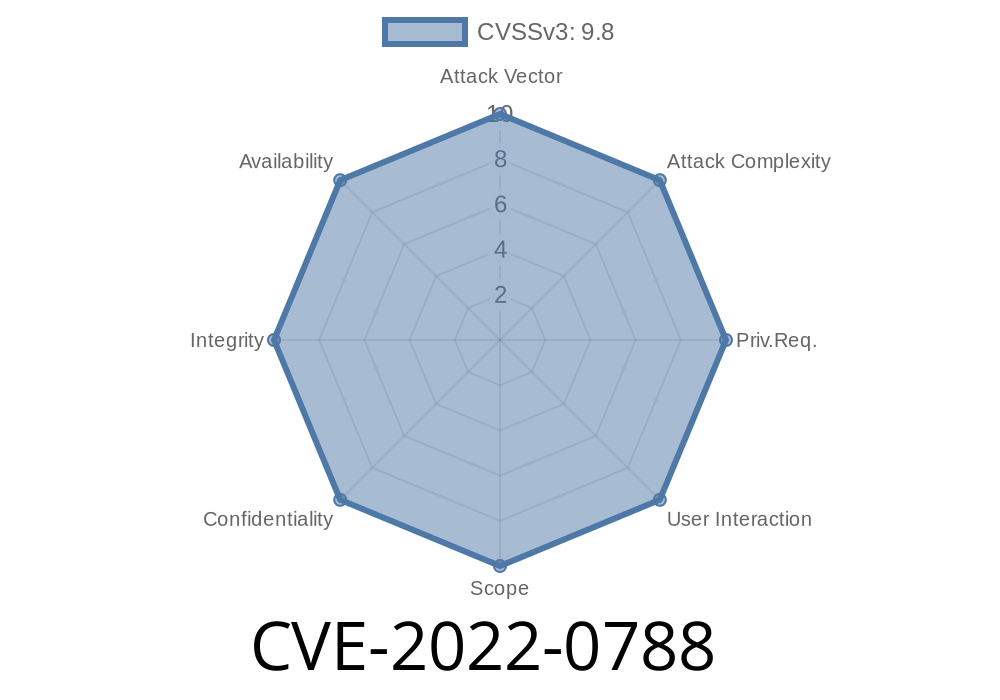
CVE-2022-0788 The WordPress plugin before 1.5.0 does not sanitize and escape a parameter before using it in a SQL statement, which can be exploited by unauthenticated users.
If a user can inject a WP REST API endpoint via a SQL injection, then the WP REST API can be used to perform any
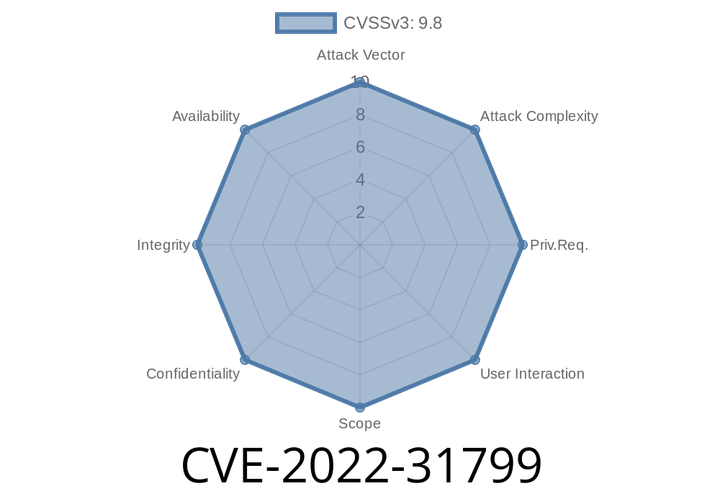
CVE-2022-31799 - Deep Dive Into Bottle Web Framework Error Handling Vulnerability Pre-.12.20
In May 2022, CVE-2022-31799 was assigned to a security vulnerability found in the popular Python micro web framework Bottle. This bug affects all versions before
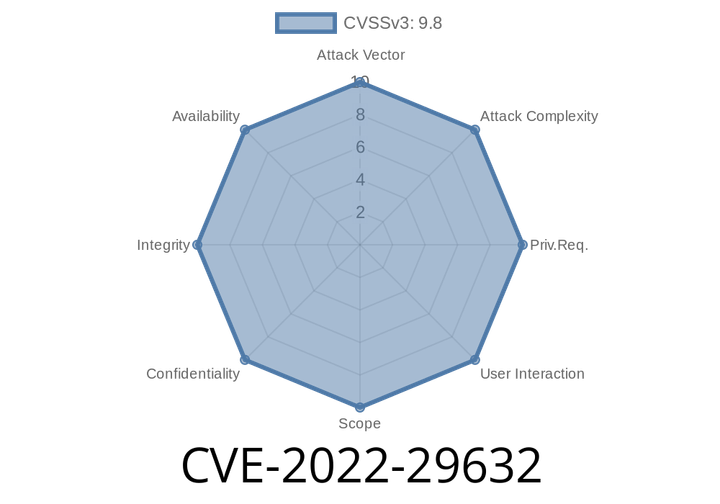
CVE-2022-29632 - How an Arbitrary File Upload Bug in Roncoo Education v9.. Leads to Remote Code Execution
---
Introduction
In 2022, security researchers identified a critical vulnerability (CVE-2022-29632) in the popular Roncoo Education platform, specifically affecting version 9... This vulnerability allows an
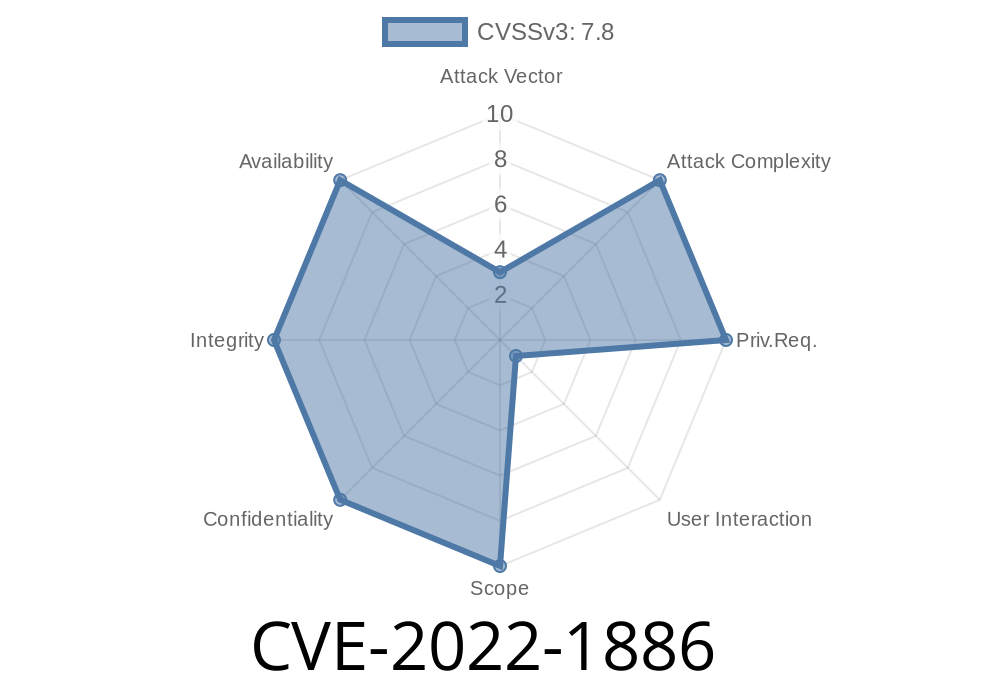
CVE-2022-1886 Heap-based Buffer Overflow in GitHub repository vim/vim prior to 8.2.
In this type of attack, an attacker tricks a user into running a specially crafted script on the web server. The specially crafted script can
CVE-2022-29248 - Guzzle Cookie Middleware Vulnerability Explained
CVE-2022-29248 is a security vulnerability discovered in Guzzle, a widely-used HTTP client library for PHP. If you develop PHP applications or maintain web APIs, you
Episode
00:00:00
00:00:00