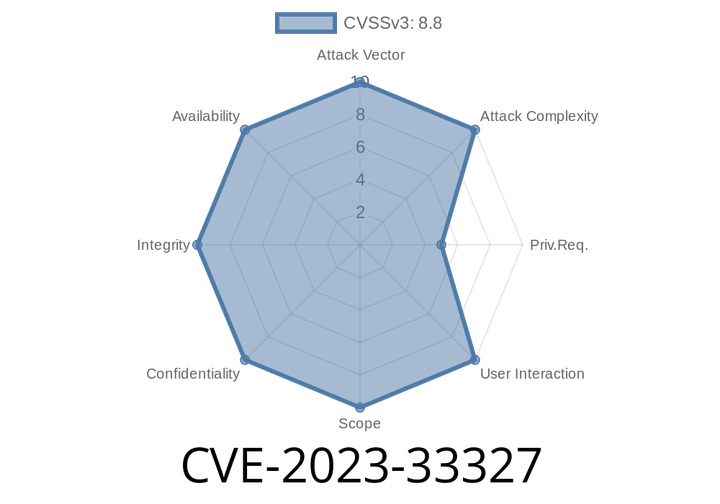
CVE-2023-33327 - How Improper Privilege Management in Leyka Opens Doors for Hackers (Including Exploit Example)
CVE-2023-33327 is an Improper Privilege Management vulnerability in the Leyka plugin, developed by Teplitsa of Social Technologies. Leyka is a popular donation and fundraising solution
CVE-2024-26026 - Unpacking the BIG-IP Next Central Manager API SQL Injection (with Exploit Details and Code Snippet)
In February 2024, a critical vulnerability—CVE-2024-26026—was discovered in the BIG-IP Next Central Manager API. This bug made it possible for remote attackers to
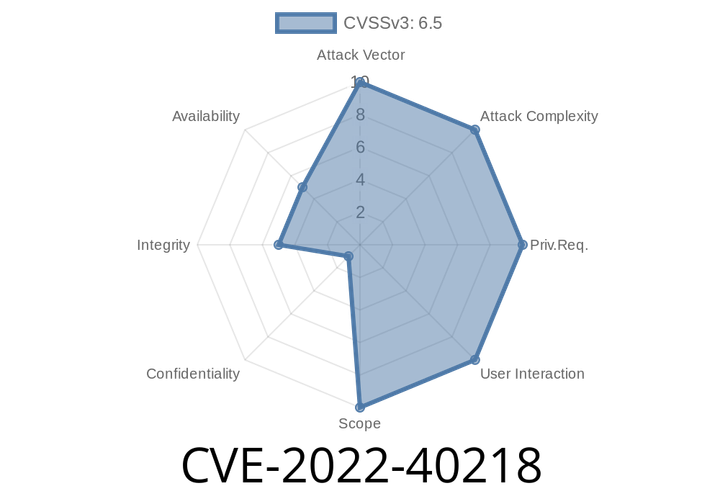
CVE-2022-40218 - Exploiting Missing Authorization in ThemeHunk Advance WordPress Search Plugin (up to 1.1.4)
WordPress is the backbone for millions of websites, and plugins make it powerful but sometimes dangerous. In 2022, a serious issue called CVE-2022-40218 was found
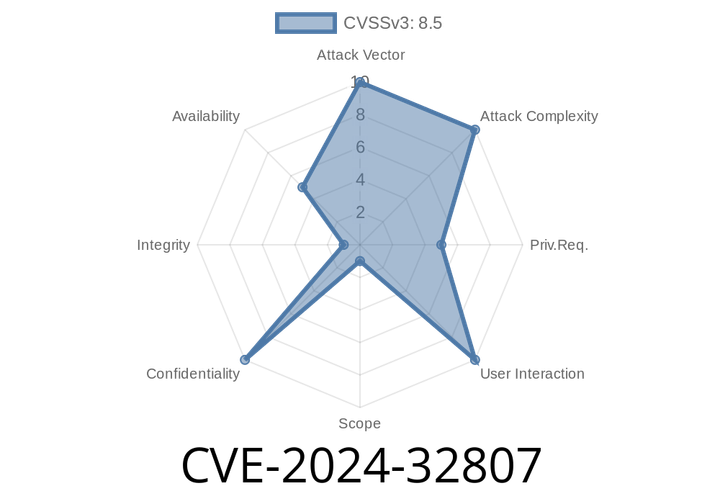
CVE-2024-32807 - Path Traversal Vulnerability in Brevo Sendinblue for WooCommerce Explained (With Exploit Example)
A serious security flaw, tracked as CVE-2024-32807, has been found in the popular Brevo Sendinblue for WooCommerce WordPress plugin. This long read explains what the
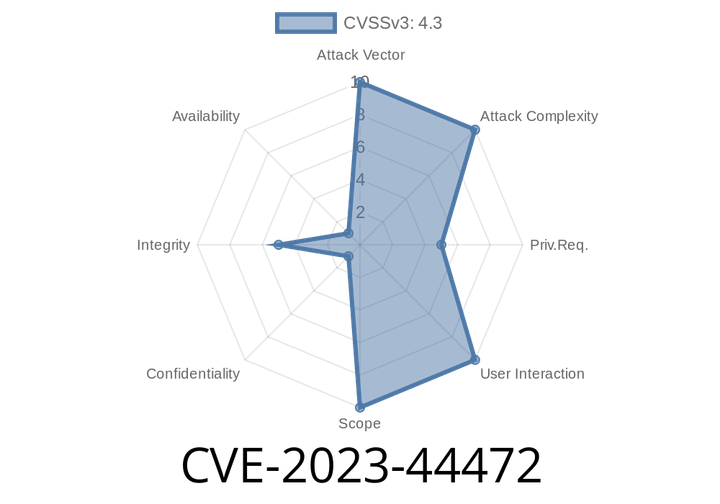
CVE-2023-44472 - How a Missing Authorization Bug Opened Thousands of WordPress Sites to Hackers (Unyson <= 2.7.28)
WordPress is the go-to platform for millions of websites, and it thrives on plugins and themes that add cool new features. But what happens when
Episode
00:00:00
00:00:00