CVE-2025-0868 - Remote Code Execution in DocsGPT via /api/remote and Unsafe JSON Parsing
Summary:
A critical vulnerability (CVE-2025-0868) has been found in popular open-source documentation assistant DocsGPT, versions .8.1 through .12.. If you're running an
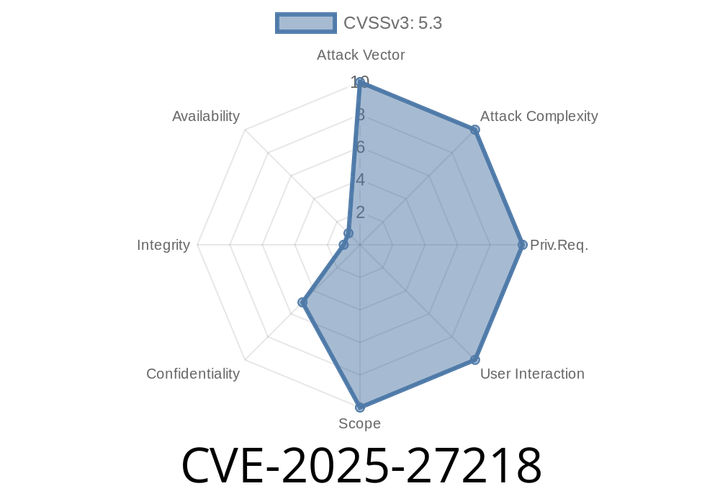
CVE-2025-27218 - Critical Remote Code Execution in Sitecore XM/XP 10.4 via Insecure Deserialization
Sitecore is a popular enterprise-grade content management system used by organizations worldwide. In March 2025, a serious vulnerability was identified in Sitecore Experience Manager (XM)
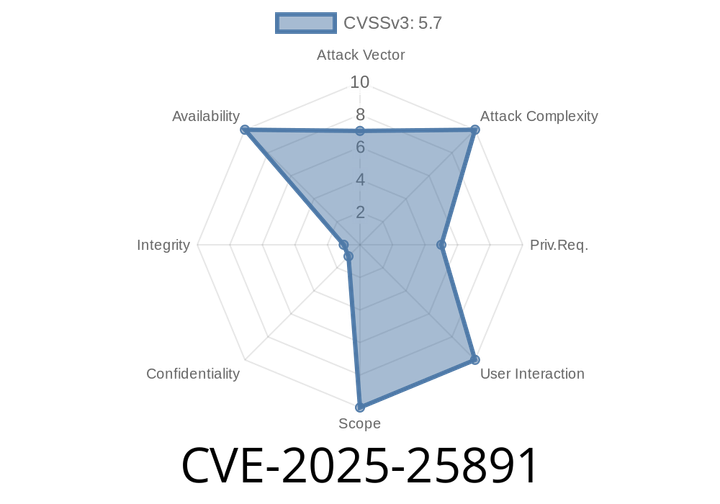
CVE-2025-25891 - Buffer Overflow in D-Link DSL-3782 v1.01 — Exploit Details and Analysis
Recently, security researchers uncovered CVE-2025-25891, a critical buffer overflow vulnerability in the D-Link DSL-3782 wireless router, firmware v1.01. The flaw is tied to the
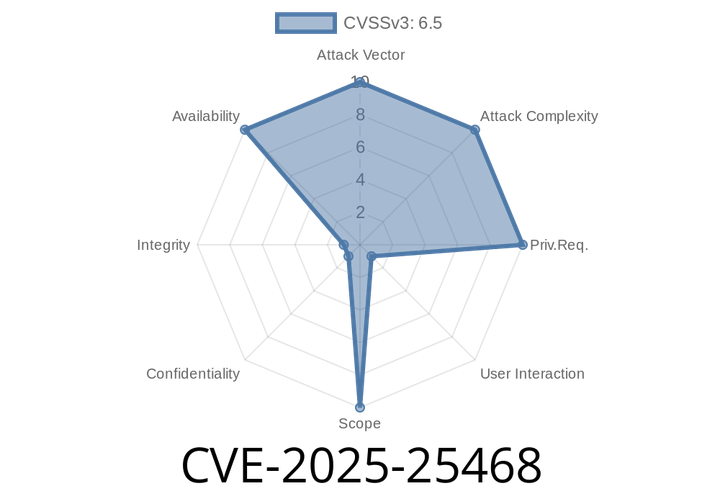
CVE-2025-25468 - FFmpeg Memory Leak in libavutil/mem.c (git-master < d5873b)
On February 2025, the security vulnerability CVE-2025-25468 was assigned to a newly discovered memory leak in FFmpeg. This problem affects the code in the libavutil/
CVE-2025-0422 - Authenticated Remote Code Execution in "bestinformed Web" via ScriptVars
A new vulnerability tracked as CVE-2025-0422 has been discovered in the "bestinformed Web" application, exposing organizations to remote code execution (RCE). This severe
Episode
00:00:00
00:00:00