CVE-2025-47273 - Critical Path Traversal in setuptools Before 78.1.1 — Exploiting Python Package Management
Published: June 2024
Severity: High
Component: setuptools (before 78.1.1)
Exploit Type: Path Traversal (Write Arbitrary Files / Possible Remote Code Execution)
Introduction
Python developers
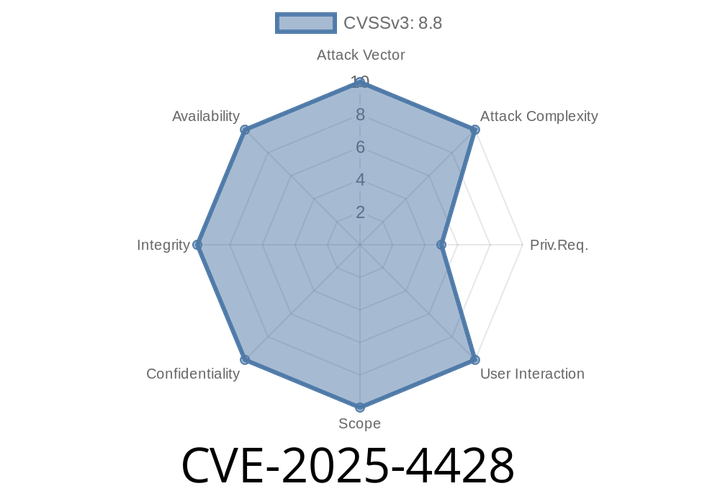
CVE-2025-4428 - Remote Code Execution in Ivanti Endpoint Manager Mobile (EPMM) API – Full Exploit Details and Analysis
Published: June 2024 <br>Author: Infosec Explainers
Overview
A new critical vulnerability CVE-2025-4428 has been discovered in Ivanti Endpoint Manager Mobile (EPMM) versions
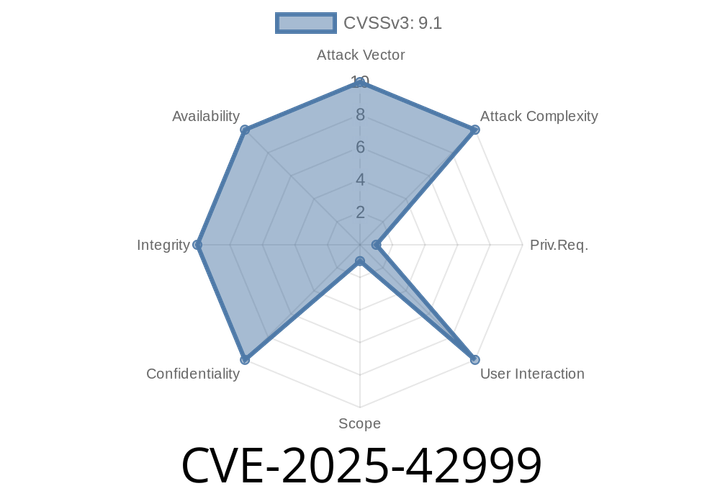
CVE-2025-42999 - SAP NetWeaver Visual Composer Metadata Uploader – Untrusted Deserialization Vulnerability Explained
CVE-2025-42999 is a newly discovered vulnerability in SAP NetWeaver Visual Composer (VC). This vulnerability lets a user with upload permissions—sometimes even an internal or
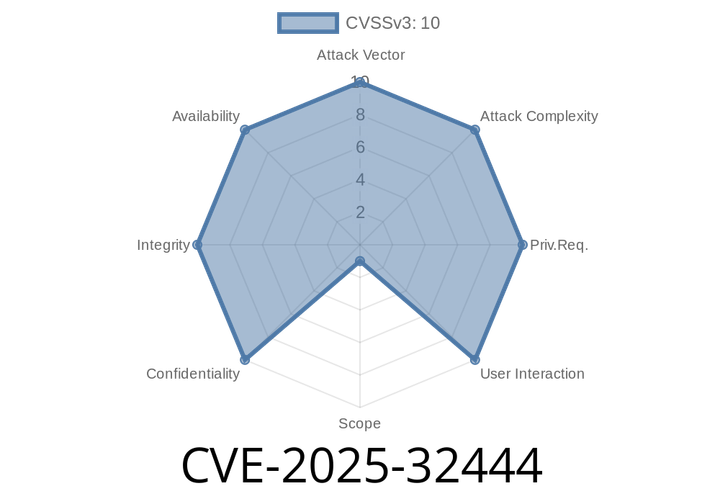
CVE-2025-32444 - Remote Code Execution in vLLM Mooncake Integration via Unsafe Pickle Serialization
A new security vulnerability, CVE-2025-32444, impacts certain versions of vLLM – a popular high-throughput and memory-efficient inference and serving engine for large language models (LLMs). This
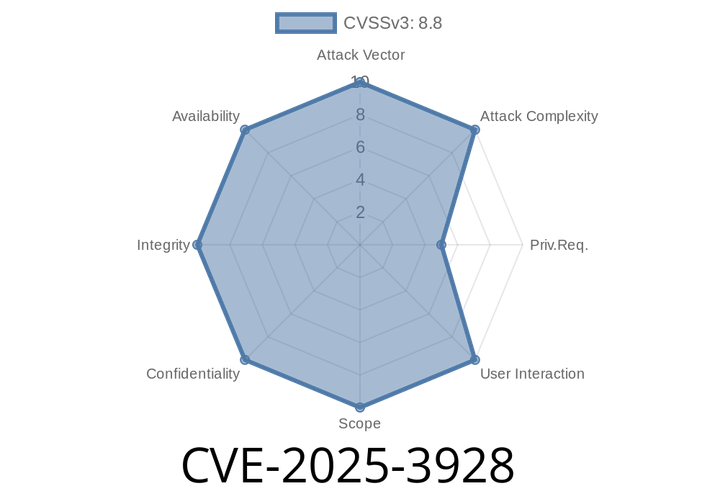
CVE-2025-3928 - Commvault Web Server Webshell Vulnerability Explained (with Exploit Details)
Commvault is a popular data protection and information management platform, used by enterprises worldwide for backup and recovery. It offers a web-based interface that helps
Episode
00:00:00
00:00:00