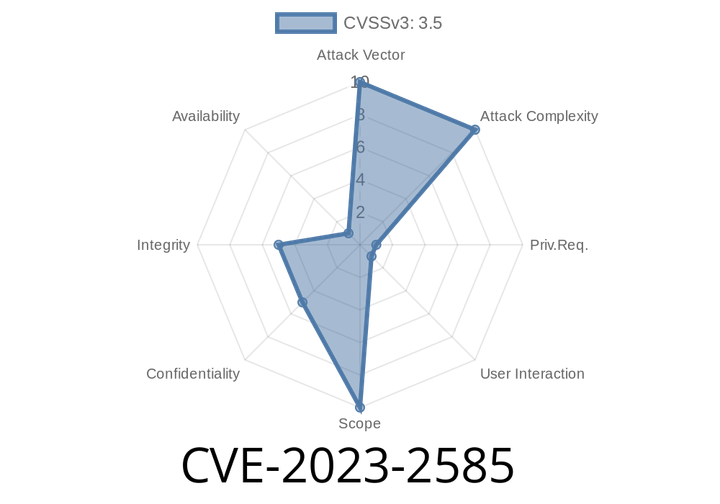
CVE-2023-2585 - How Keycloak’s Device Authorization Flaw Could Let Attackers Trick OAuth Admins (With Exploit Walkthrough)
Keycloak is one of today’s most relied-upon open source identity and access management (IAM) solutions. If you use OAuth in your organization, there’s
CVE-2023-3223 - How a Sneaky Multipart Upload Flaw in Undertow Could Crash Your Java Server
---
Introduction
Did you know a simple tweak to an HTTP request could bring some Java servers to their knees? That’s what happened with