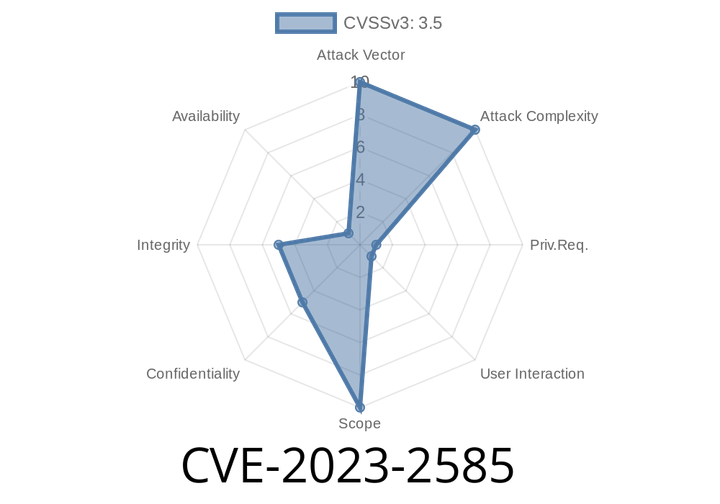
CVE-2023-2585 - How Keycloak’s Device Authorization Flaw Could Let Attackers Trick OAuth Admins (With Exploit Walkthrough)
Keycloak is one of today’s most relied-upon open source identity and access management (IAM) solutions. If you use OAuth in your organization, there’s
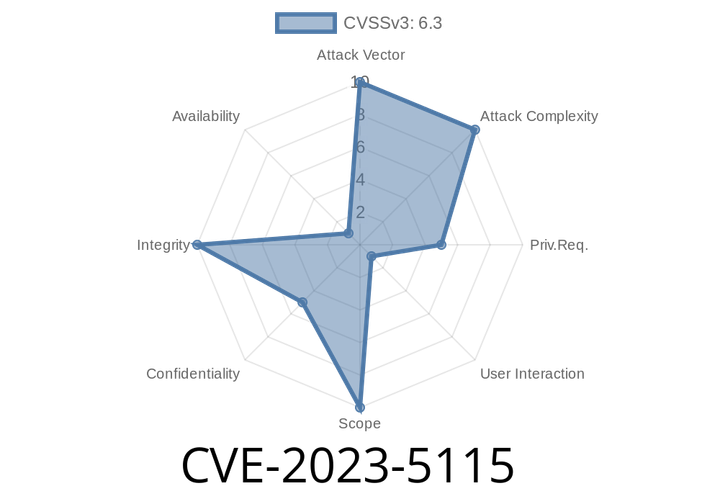
CVE-2023-5115 - Path Traversal Attack in Ansible Automation Platform with Exploit Example
In September 2023, a new security issue—CVE-2023-5115—was reported in the widely used Ansible Automation Platform. This vulnerability allows attackers to take advantage of
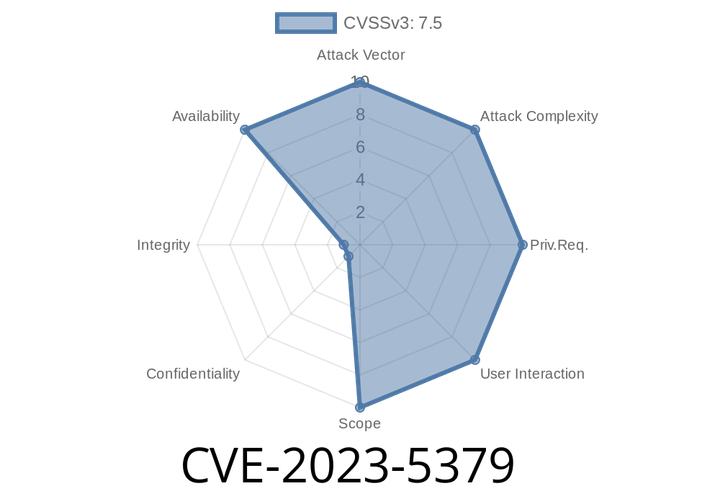
CVE-2023-5379 - Denial-of-Service in Undertow via Oversized AJP Headers
In September 2023, a vulnerability was disclosed in Undertow, the web server used by JBoss EAP (Enterprise Application Platform), which can be leveraged for Denial-of-Service
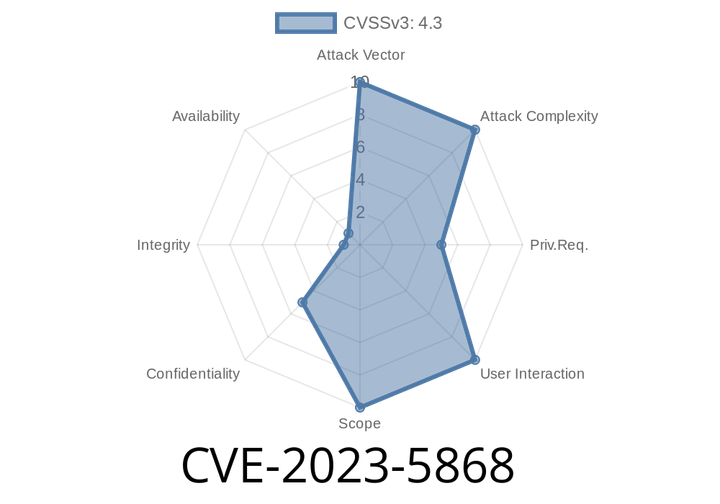
CVE-2023-5868 - Understanding PostgreSQL’s Memory Disclosure Vulnerability
PostgreSQL, one of the world’s most popular open-source databases, faced a serious security risk in late 2023: CVE-2023-5868. This memory disclosure vulnerability let remote
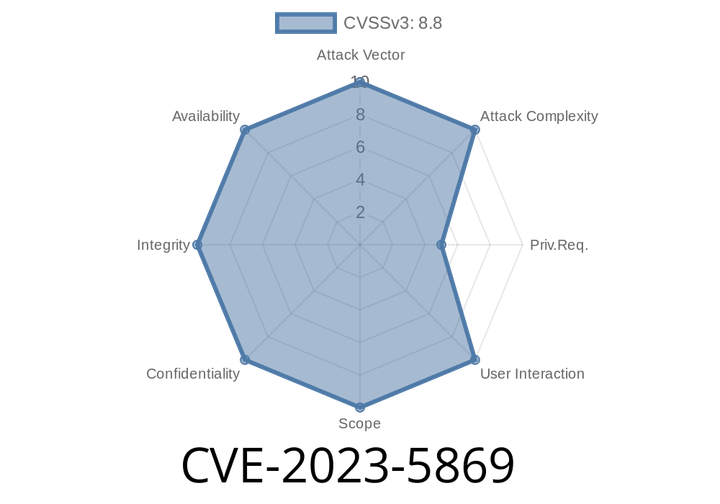
CVE-2023-5869 - Explaining the PostgreSQL Array Integer Overflow Vulnerability
CVE-2023-5869 is a dangerous vulnerability discovered in PostgreSQL, one of the world’s most popular open-source relational databases. This security flaw allows authenticated users to
Episode
00:00:00
00:00:00