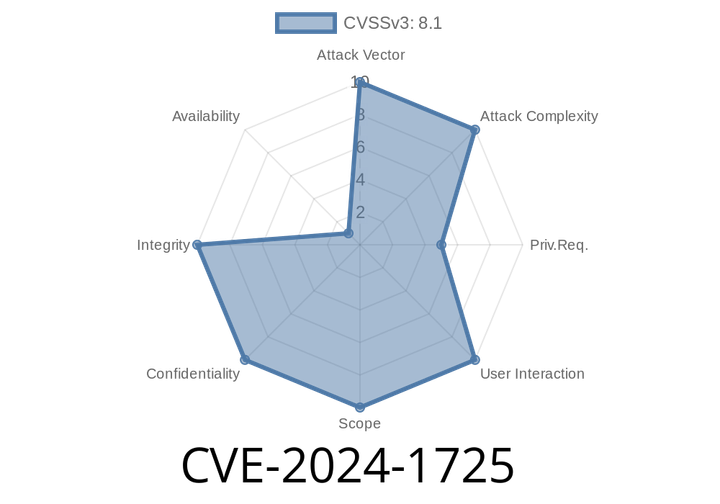
CVE-2024-1725 - Exploiting kubevirt-csi in OpenShift Virtualization HCP for Root Volume Access
A recently discovered security vulnerability, CVE-2024-1725, was identified in the kubevirt-csi component used in OpenShift Virtualization's Hosted Control Plane (HCP). This flaw could
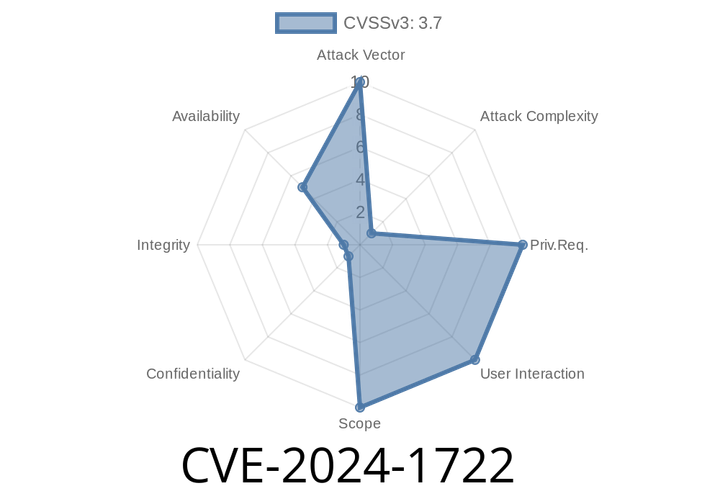
CVE-2024-1722 - How a Keycloak Flaw Lets Attackers Lock Out Legitimate Users
Keycloak is a popular open-source authentication and identity management system from Red Hat. It’s used by startups and big companies alike for single sign-on
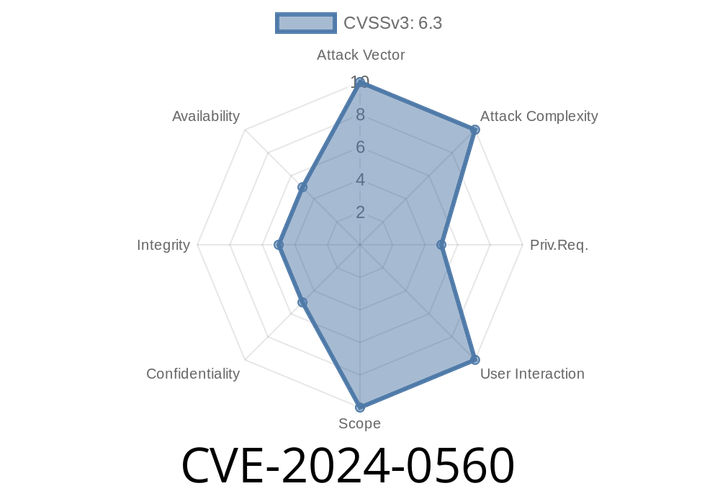
CVE-2024-0560: 3Scale Keycloak/RHSSO 7.5. Integration Auth Vulnerability
A recent vulnerability has been discovered in the integration of 3Scale with Keycloak, specifically when used with Keycloak 15 or Red Hat Single Sign-On (RHSSO)
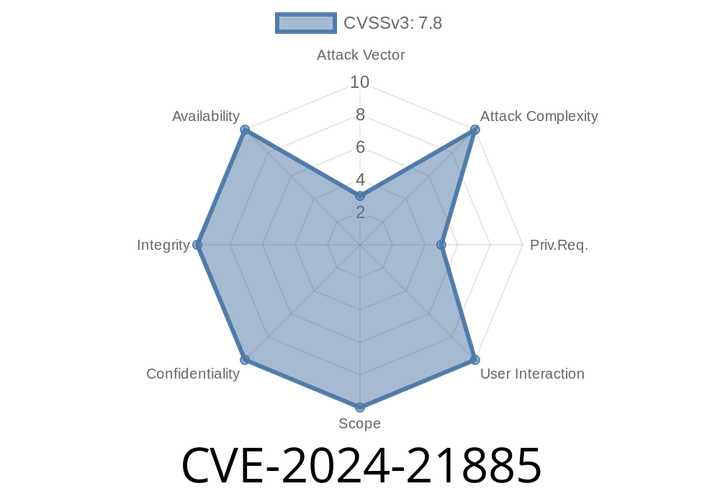
CVE-2024-21885 - Heap Buffer Overflow in X.Org Server’s XISendDeviceHierarchyEvent – Understanding the Flaw and How it’s Exploited
A new security vulnerability, CVE-2024-21885, has been discovered in the X.Org Server – the core display server for Linux UNIX systems. This flaw can potentially
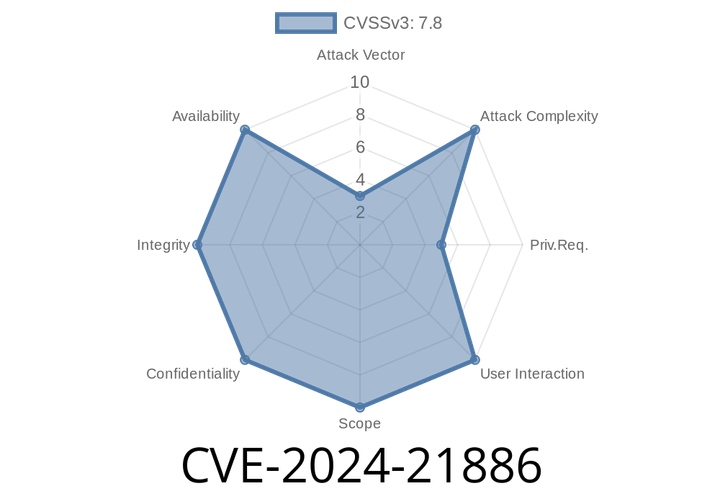
CVE-2024-21886 - Heap Buffer Overflow in X.Org Server’s DisableDevice Function Enables Remote Code Execution via SSH X11 Forwarding
In early 2024, security researchers uncovered a critical vulnerability affecting the X.Org Server, the backbone of graphical displays on many Unix-like operating systems. Registered
Episode
00:00:00
00:00:00