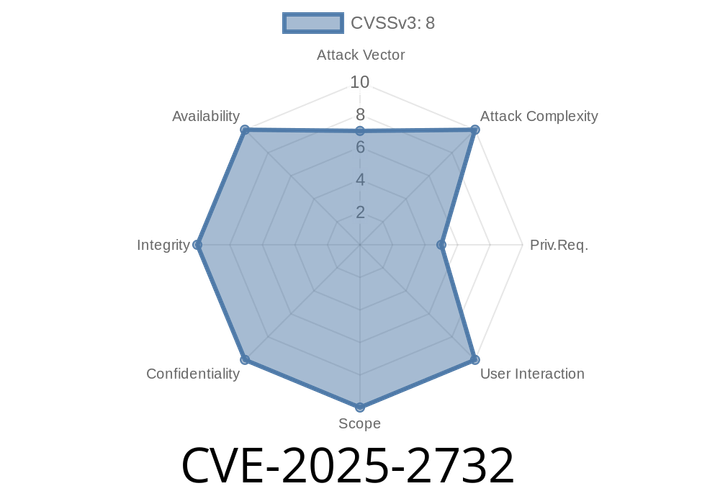
CVE-2025-2732 - Critical Command Injection in H3C Magic Routers — Full Details and Exploit Explained
Date published: June 2024
Author: CyberSafe Insights
Introduction
Recently, a new and critical vulnerability, CVE-2025-2732, was disclosed affecting multiple popular H3C Magic home and small
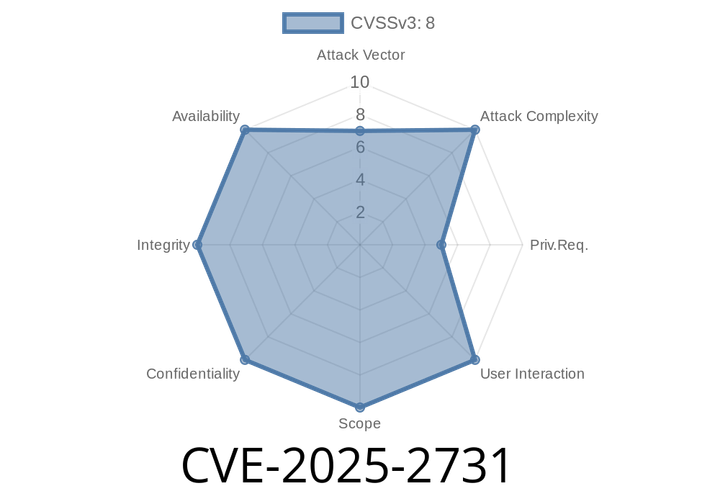
CVE-2025-2731 - Critical Command Injection in H3C Magic Routers Exposes Home and Small Office Networks
A new critical vulnerability—CVE-2025-2731—has been discovered in several H3C Magic router products, including Magic NX15, Magic NX30 Pro, Magic NX400, Magic R301, and
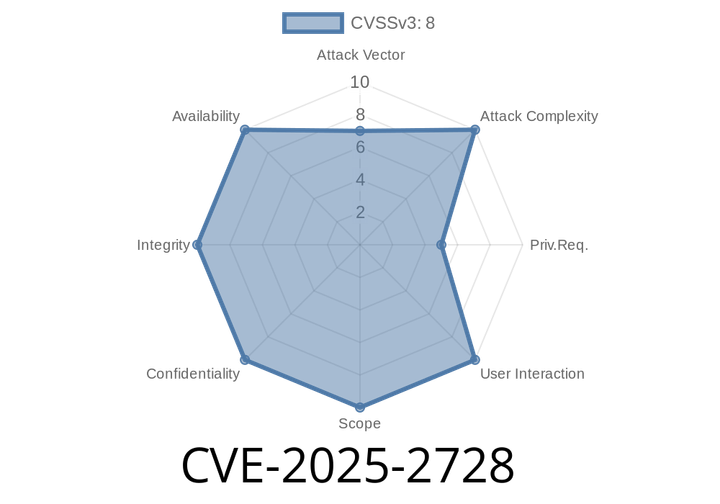
CVE-2025-2728 - Critical Command Injection in H3C Magic NX30 Pro and NX400 Routers (Up to V100R014)
Recently, a critical vulnerability, tracked as CVE-2025-2728, was discovered in H3C Magic NX30 Pro and Magic NX400 router models running firmware versions up to V100R014.
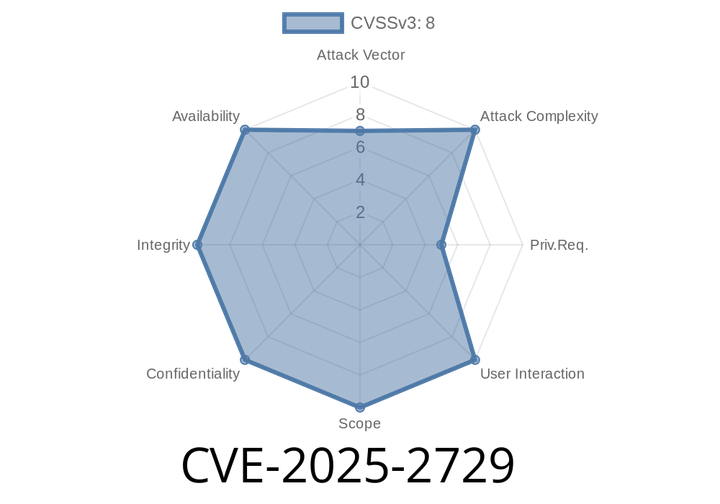
CVE-2025-2729 - Critical Command Injection Vulnerability in H3C Magic Routers (NX15, NX30 Pro, NX400, R301, BE18000)
Summary:
A critical new vulnerability, CVE-2025-2729, has been discovered in several popular H3C Magic router models: Magic NX15, Magic NX30 Pro, Magic NX400, Magic R301,
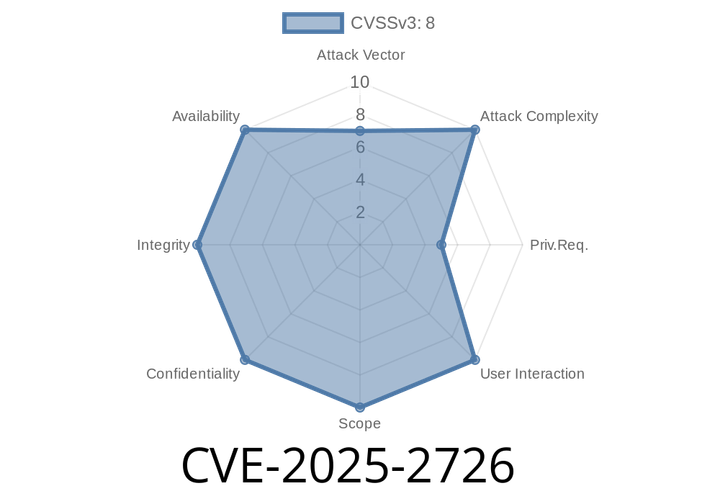
CVE-2025-2726 - Critical Command Injection in H3C Magic Routers – Full Breakdown, Exploit, and Recommendations
---
Overview
A newly discovered vulnerability, CVE-2025-2726, affects several popular H3C Magic router models, including Magic NX15, Magic NX30 Pro, Magic NX400, Magic R301, and
Episode
00:00:00
00:00:00