CVE-2025-47967 - Insufficient Warning in Microsoft Edge for Android Enables Spoofing Attacks – What You Need to Know
---
Introduction
A newly disclosed vulnerability, CVE-2025-47967, targets Microsoft Edge for Android. This flaw centers around insufficient UI (User Interface) warning mechanisms during dangerous operations.
CVE-2025-26423 - Permanent DoS and Local Privilege Escalation in Android's WifiConfigurationUtil.java
On June 2025, a critical vulnerability, CVE-2025-26423, was discovered and disclosed in Android's connectivity stack. This flaw is found inside the validateIpConfiguration function
CVE-2023-35657 - Exploiting Type Confusion in `bta_av_config_ind` for Out-of-Bounds Reading
A serious security vulnerability was identified in the Android Bluetooth stack, specifically within the function bta_av_config_ind in the file bta_av_aact.
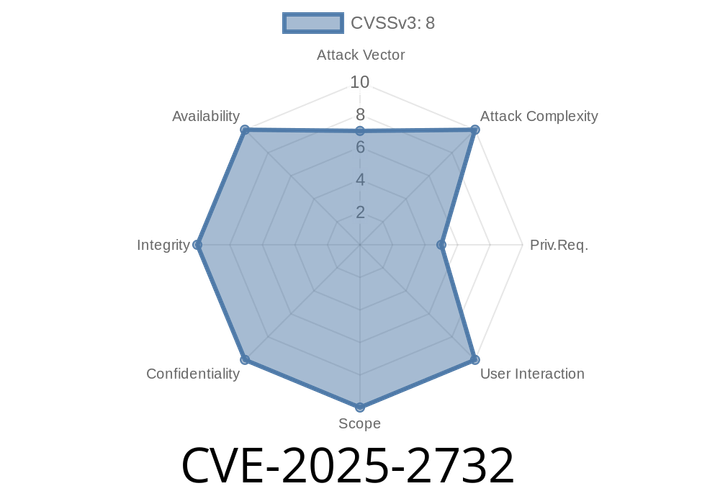
CVE-2025-2732 - Critical Command Injection in H3C Magic Routers — Full Details and Exploit Explained
Date published: June 2024
Author: CyberSafe Insights
Introduction
Recently, a new and critical vulnerability, CVE-2025-2732, was disclosed affecting multiple popular H3C Magic home and small
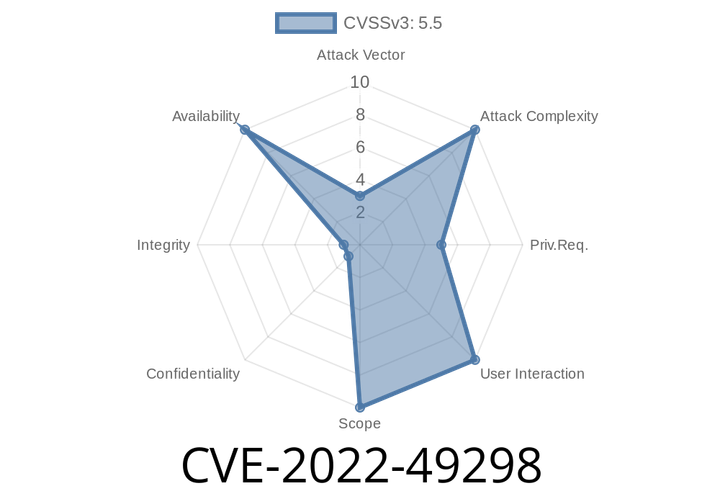
CVE-2022-49298 - Uninitialized Memory Use in Linux Kernel’s rtl8712 Staging Driver (Exploit Deep Dive)
In early 2022, a vulnerability was found in the Linux kernel’s Realtek 8712U USB WiFi driver (staging: rtl8712). Labeled CVE-2022-49298, this bug allowed for
Episode
00:00:00
00:00:00