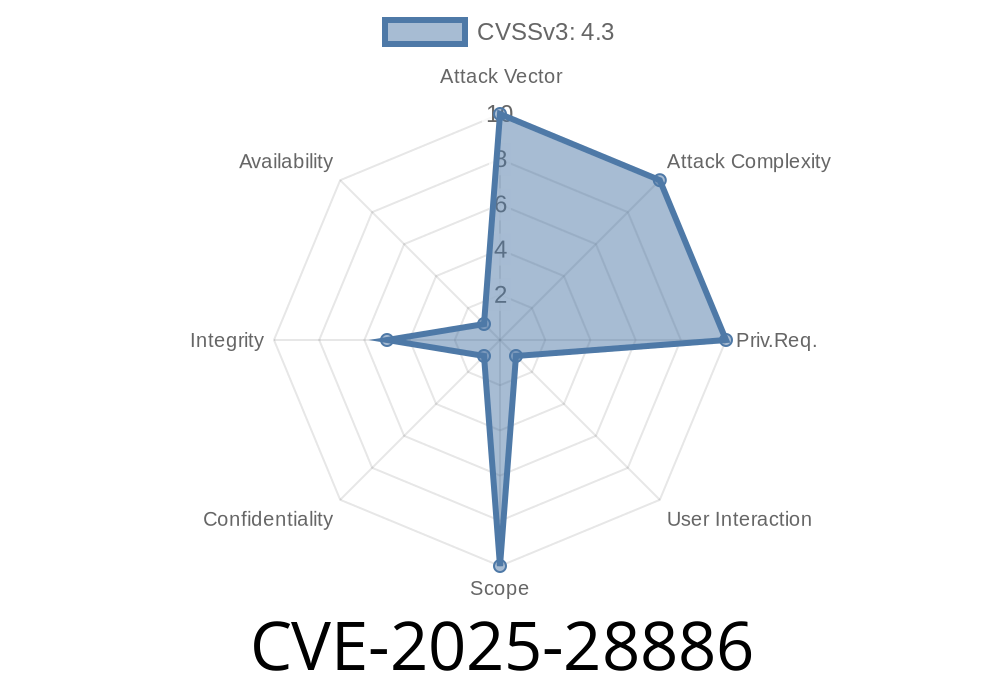
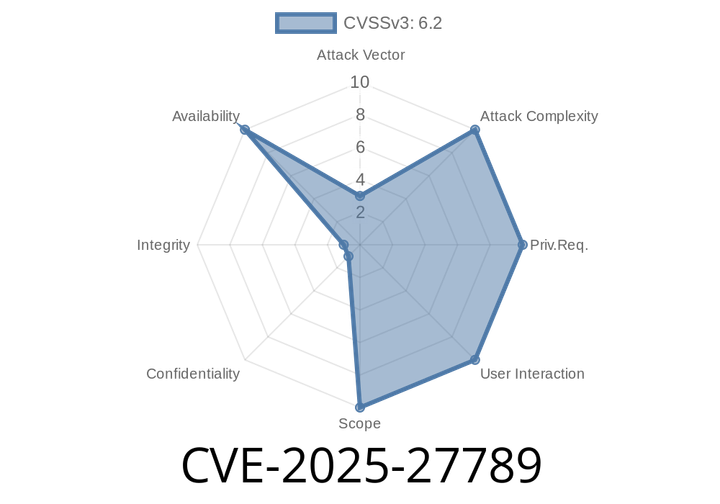
CVE-2025-27789 - Babel Regex Named Capture Groups Lead to Quadratic Performance Bug – How It Works & How to Fix
Babel helps developers use cutting-edge JavaScript—years before browsers understand it—by compiling new features to older code. However, in versions of Babel before 7.
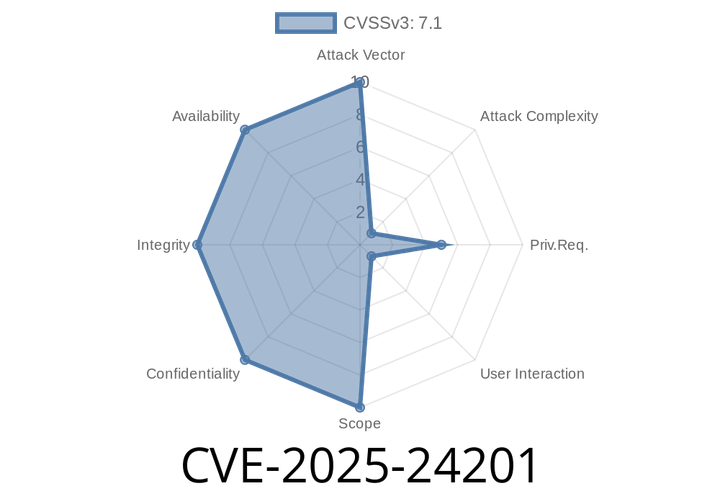
CVE-2025-24201 - Out-of-Bounds Write in WebKit—A Deep Dive Into the Latest Apple Security Patch
On July 2025, Apple released urgent security fixes across all major platforms to address a high-risk vulnerability, CVE-2025-24201. This post walks you through what went
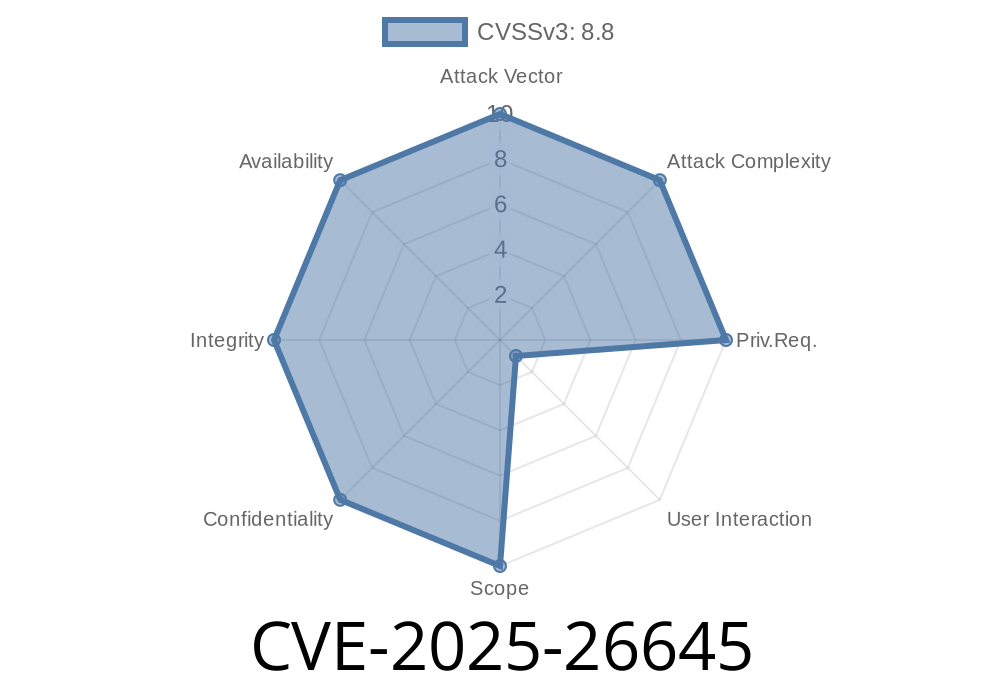
CVE-2025-26645 - Exploiting Relative Path Traversal in Remote Desktop Client for Remote Code Execution
A new high-severity vulnerability—CVE-2025-26645—has been discovered in popular Remote Desktop Client software. This flaw allows attackers anywhere on your network to execute arbitrary
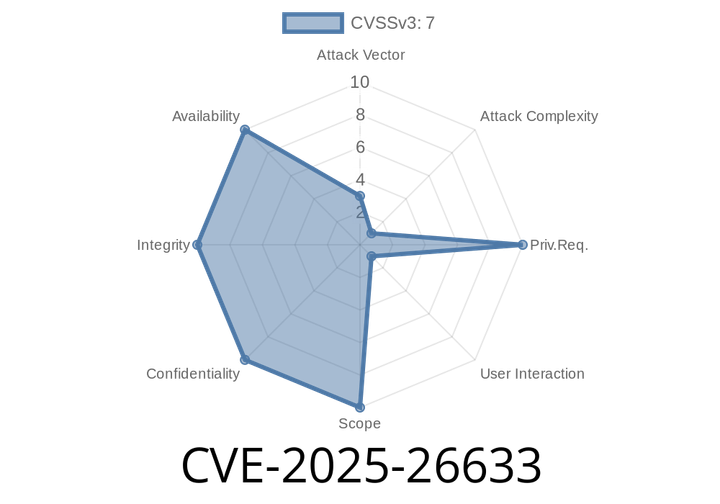
CVE-2025-26633 - Breaking Down Microsoft Management Console's Security Bypass Vulnerability
Published: June 2024
Severity: High
Impact: Local Privilege Escalation / Security Feature Bypass
Introduction
On June 5, 2024, security analysts disclosed a crucial Windows vulnerability tracked
Episode
00:00:00
00:00:00