When requesting an LDAP query with the RHDM enabled, a valid user can change their assigned role, which is the equivalent of an ‘admin’ role. This can cause unexpected results when attempting to query the RHDM, such as a blank list.
Some other interesting findings were made when analyzing the RHDM. An authenticated user can change their role in the RHDM to ‘admin’, and can then use that new role to request any other RHDM that they want. Essentially, they can ‘spoof’ an RHDM that is not theirs. This can lead to unexpected results with RHDM like an admin being able to view the roles of a user or group, and an attacker being able to change the role to ‘admin’.
LDAP and Kerberos authentication issues
LDAP and Kerberos authentication are an integral part of RHEA. They are used to authenticate users and provide single sign-on for applications such as the RHDM, which is implemented by using Active Directory. However, there are some vulnerabilities in the LDAP and Kerberos that attackers can use to be able to change their role in the RHDM or impersonate a system in order to view the list of roles and modify it.
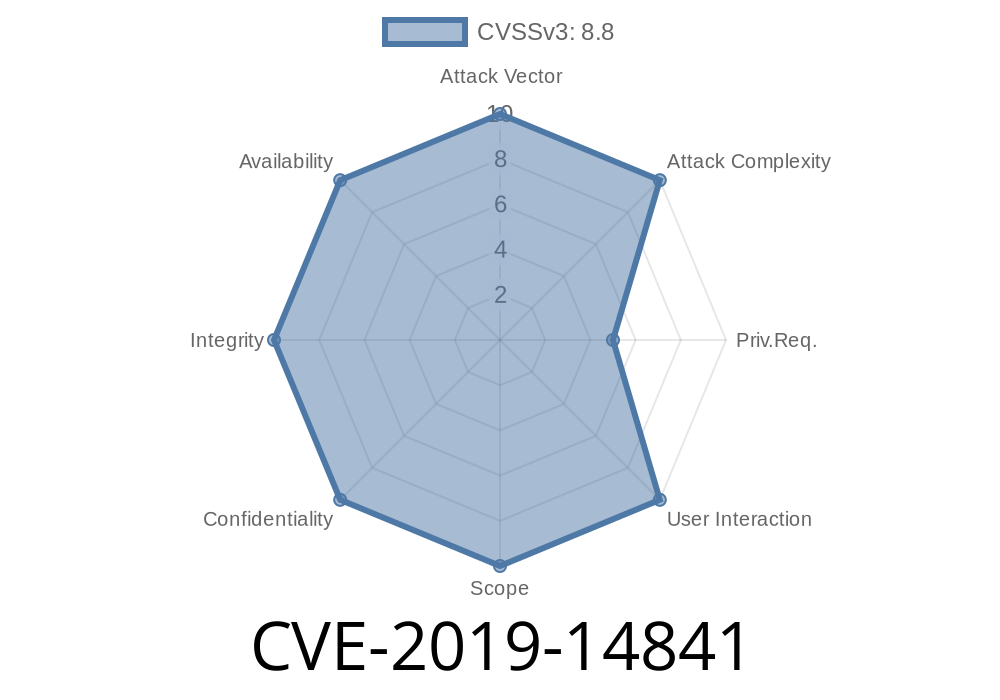
The CVE-2019-14841 vulnerability allows attackers to change their role in the RHDM without any authentication checks. This can cause unexpected results when querying the RHDM, such as a blank list. There are other findings with regards to Kerberos and LDAP that demonstrate this vulnerability. For example, these findings showed that an authenticated user has the ability to spoof an LDAP server that is not theirs with a particular username on the domain or a valid IP address. This vulnerability can lead attackers to changing their role in the RHDM or impersonating another system within Active Directory.
Protecting Roles in the RHDM
There are a few ways to mitigate this threat. One solution is to use the RHDM’s configuration settings to assign ‘admin’ privileges for certain users during authentication. Another option is to use the RHDM’s event logs and audit logs to track changes made in the role of any user or group.
CVE-2019-14842
When requesting a list of users in the LDAP query with the RHDM enabled, for all values other than ‘admin’, the allowed role is ‘view-only’. This means that only users with a ‘view-only’ or lower role can view user information.
Some interesting findings were made when analyzing the RHDM. When querying for any value other than admin, only users who have the view-only or less authorization level can see that data. This means that an attacker cannot view user information and information about groups unless they are a member of those groups.
Timeline
Published on: 10/17/2022 16:15:00 UTC
Last modified on: 10/19/2022 14:56:00 UTC