The Common Vulnerabilities and Exposures (CVE) system is a public resource that provides a standardized method for identifying and documenting publicly disclosed security vulnerabilities in software and hardware. In this post, we will take an in-depth look at CVE-2019-8720, a vulnerability found in WebKit - a widely used web content rendering engine that powers popular browsers like Safari and many other applications across multiple platforms. We'll explore the specifics of the vulnerability, examine how it can be exploited, and discuss how improved memory handling can address the multiple memory corruption issues associated with this flaw.
Vulnerability Details
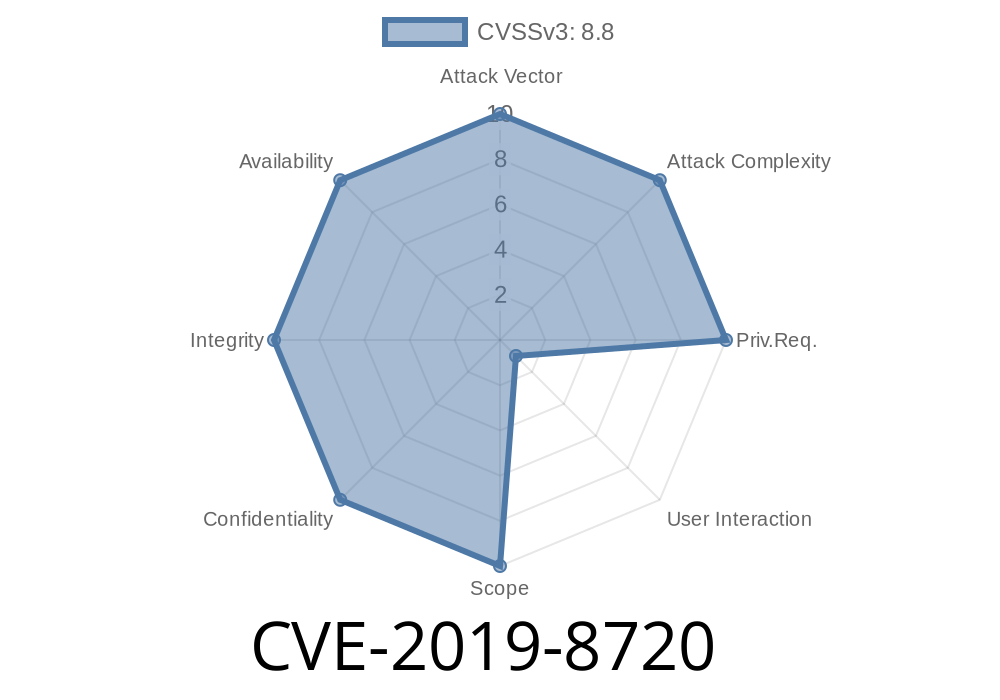
CVE-2019-8720 is a critical vulnerability in WebKit, discovered by members of Google Project Zero and Microsoft Browser Vulnerability Research teams. The flaw is triggered when WebKit processes maliciously crafted web content, which may lead to arbitrary code execution on the host system. According to the official CVE description, multiple memory corruption issues were addressed with improved memory handling.
Exploiting CVE-2019-8720
To understand the exploitation of this vulnerability, let's consider a simple code snippet that demonstrates how the malicious web content can exploit the memory corruption issues in WebKit:
<!DOCTYPE html>
<html>
<head>
<script>
function trigger_vulnerability() {
var element = document.createElement('div');
// Cause memory corruption
for (var i = ; i < x10000; ++i) {
element.appendChild(document.createElement('div'));
}
// Trigger a crash or arbitrary code execution
element.children[x1234].innerHTML = '';
}
</script>
</head>
<body>
<button onclick="trigger_vulnerability()">Exploit CVE-2019-8720</button>
</body>
</html>
When the user clicks the "Exploit CVE-2019-8720" button, the trigger_vulnerability() function is called. The function first creates a new div element and then appends a large number of child div elements to it. This operation is performed inside a loop that runs for x10000 iterations (65536 times). This manipulation leads to memory corruption in the WebKit engine. Finally, by attempting to access an out-of-bounds child element and modifying its innerHTML, the script triggers a crash or potentially arbitrary code execution.
Here are the links to the original references and in-depth technical analysis provided by the researchers who discovered the vulnerability:
- WebKit Bugzilla Entry
- Google Project Zero Analysis
- Microsoft Browser Vulnerability Research Report
Mitigation and Improved Memory Handling
Multiple memory corruption issues in WebKit were addressed with improved memory handling to fix the vulnerability. This mitigation includes the following key improvements:
1. Implementation of new memory safety mechanisms such as bounds checking and address randomization, which protect against buffer overflow attacks and make it difficult for an attacker to locate and target specific areas in memory.
2. More robust garbage collection and memory allocation processes, which helps prevent use-after-free vulnerabilities.
3. Rigorous validation and sanitization of untrusted inputs, helping to prevent malformed or malicious data from triggering memory corruption.
Conclusion
The CVE-2019-8720 vulnerability in WebKit underscores the importance of thorough and ongoing vulnerability research in web content rendering engines. The widespread use of WebKit highlights the potential impact that such vulnerabilities can have on user security and privacy. Thankfully, in this case, the vulnerability was discovered and reported by responsible security researchers, and the WebKit project promptly addressed the issue with improved memory handling techniques. Users should ensure that they keep their web browsers and other applications that use WebKit up-to-date to prevent exploitation of known vulnerabilities like CVE-2019-8720.
Timeline
Published on: 03/06/2023 23:15:00 UTC
Last modified on: 03/11/2023 02:53:00 UTC