An attacker could enter a line with a large number, such as "9223372036854775808". This vulnerability is most significant in applications with high concurrency, such as web applications. An attacker could enter a series of large numbers, such as "9999999999999999999999999999999999999999999".
Vulnerable code example let counter = 0;
while(counter
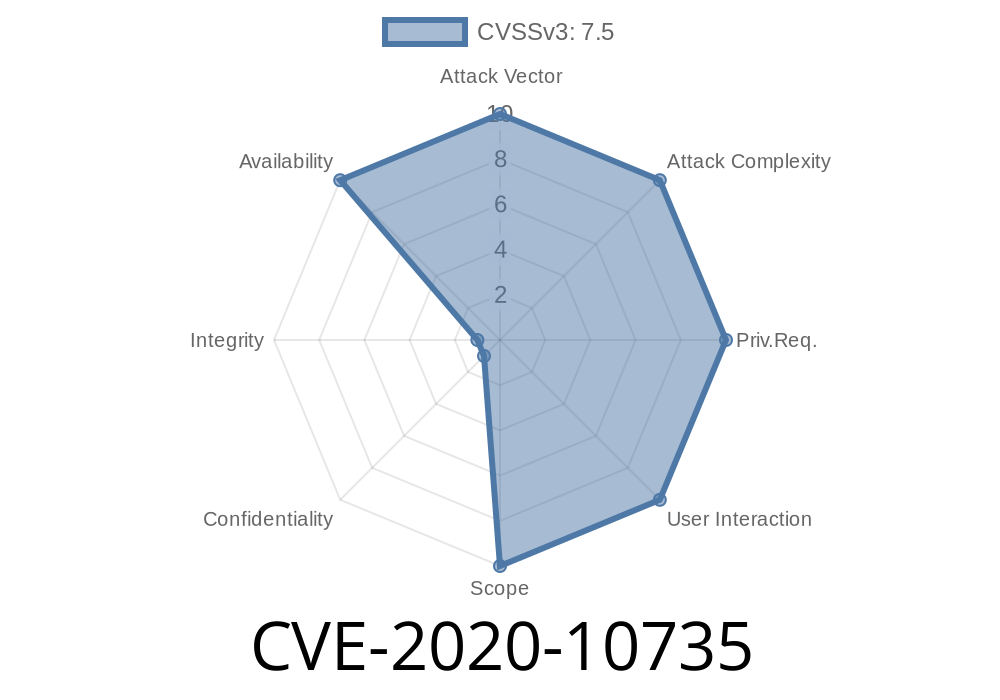
CVE-2020-10736
An attacker could enter a line with a large number, such as "9223372036854775808". This vulnerability is most significant in applications with high concurrency, such as web applications. An attacker could enter a series of large numbers, such as "9999999999999999999999999999999".
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
If you want to grow your business, great search engine optimization (SEO) is a must. The challenge? Many small businesses don’t have the time, skills, or expertise necessary to handle everything that comes with a solid SEO strategy. From keyword research to content evaluation, from page optimization to internal linking, it’s easy for companies to end up with a generic web presence that doesn’t inspire engagement or drive conversions.
Designing an effective SEO strategy isn’t a simple task. Companies have to consider how search engines are evaluating the content, what aspects of SEO offer the most impact, and where they could change their current content to better align with search engine expectations. This is especially critical as search engines like Google continually refine their ranking process. For example, page loading speed is now a factor in search result rankings. In practice, this expands the role of SEO; it’s not enough to simply weave in popular keywords and deliver high-quality content. Brands also need to consider the entire user experience. As a result, it’
High-Concurrency Remote Code Execution Vulnerability
An attacker could enter a line with a large number, such as "9223372036854775808". This vulnerability is most significant in applications with high concurrency, such as web applications. An attacker could enter a series of large numbers, such as "99999999999999999999999999999999999999999".
Timeline
Published on: 09/09/2022 14:15:00 UTC
Last modified on: 09/25/2022 04:15:00 UTC
References
- https://access.redhat.com/security/cve/CVE-2020-10735
- https://docs.google.com/document/d/1KjuF_aXlzPUxTK4BMgezGJ2Pn7uevfX7g0_mvgHlL7Y
- https://bugzilla.redhat.com/show_bug.cgi?id=1834423
- https://github.com/python/cpython/issues/95778
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/4EWKR2SPX3JORLWCXFY3KN2U5B5CIUQQ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/2VCU6EVQDIXNCEDJUCTFIER2WVNNDTYZ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/V7ZUJDHK7KNG6SLIFXW7MNZ6O2PUJYK6/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/HSRPVJZL6DJFWKYRHMNJB7VCEUCBKRF5/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/6XL6E5A3I36TRR73VNBOXNIQP4AMZDFZ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/U4ZZV4CDFRMTPDBI7C5L43RFL3XLIGUY/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/32AAQKABEKFCB5DDV5OONRZK6BS23HPW/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/SZYJSGLSCQOKXXFVJVJQAXLEOJBIWGEL/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/OT5WQB7Z3CXOWVBD2AFAHYPA5ONYFFZ4/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/UBPDVCDIUCEBE7C4NAGNA2KQJYOTPBAZ/
- http://www.openwall.com/lists/oss-security/2022/09/21/1
- http://www.openwall.com/lists/oss-security/2022/09/21/4
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/OKYE2DOI2X7WZXAWTQJZAXYIWM37HDCY/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/PD7FTLJOIGMUSCDR3JAN6WRFHJEE4PH5/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/OT5U223OE5ZOUHZAZYSYSWVJQIKDE73E/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/76YE7AM37MRU76XJV4M27CWDAMUGNRYK/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ZEOAJWGGY55QU35UM2OVZATBW5MX2OZD/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2020-10735