When reading the data from the image file, it may be possible for an attacker to cause a buffer overflow, which may lead to remote code execution. Unfortunately, there is no way to determine if an image has been maliciously modified via the above vulnerability.
TL;DR: A buffer overflow vulnerability has been discovered in LibRaw, a cross-platform library for reading/converting various file formats.
Vulnerability description
On December 1st, 2019, a vulnerability was discovered in LibRaw. This vulnerability allows an attacker to cause a buffer overflow in the vulnerable application. As a result, remote code execution is possible. Unfortunately, there is no way to determine if an image has been maliciously modified via this vulnerability.
Vulnerability details
A buffer overflow vulnerability has been discovered in LibRaw, a cross-platform library for reading/converting various file formats. The vulnerability exists in the getNextWord() function of LibRaw, which will lead to remote code execution if an image file is processed by this function. Fortunately, there is no way to determine if an image has been maliciously modified via this vulnerability. To mitigate the risk of exploitation, you should use your own personal judgment and decide whether or not it's necessary to remove or replace all instances of the vulnerable software.
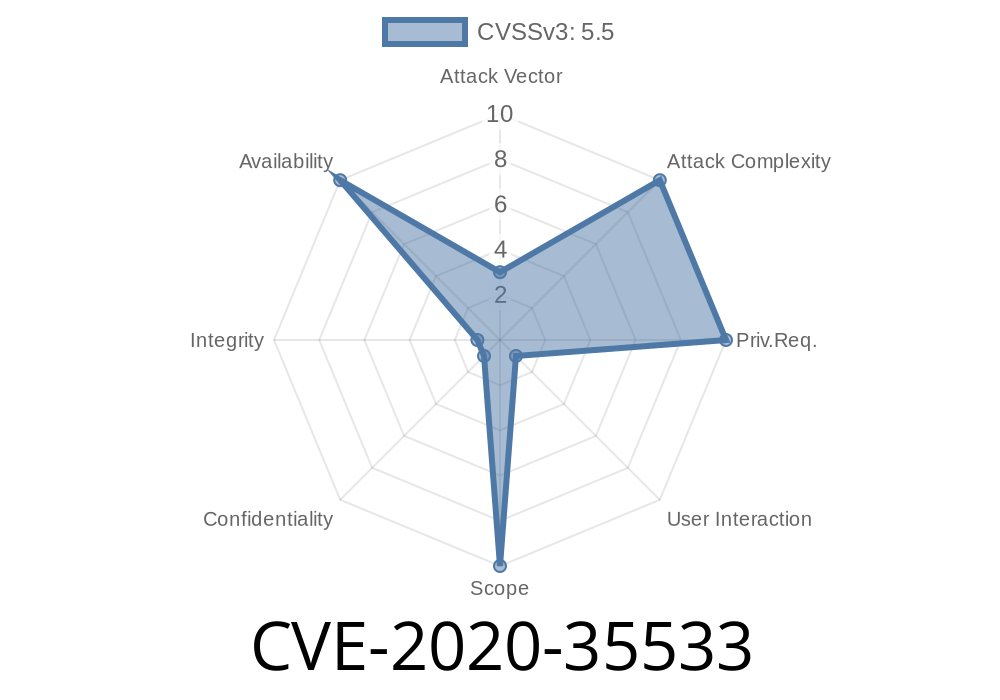
CVE-2020-35533: An issue with image parsing
When reading the data from the image file, it may be possible for an attacker to cause a buffer overflow, which may lead to remote code execution. Unfortunately, there is no way to determine if an image has been maliciously modified via the above vulnerability.
The issue that CVE-2020-35533 points out is due to a lack of bounds checking in LibRaw's handling of data. This helps attackers create a buffer overflow and execute arbitrary code on the target system.
An attacker can create a buffer overflow by modifying an image's metadata and causing it to be loaded into LibRaw with invalid sizes or offsets. When this happens, the program will try to read data beyond the bounds of its allocated memory space, resulting in a crash.
Vulnerability Details
A buffer overflow vulnerability has been discovered in LibRaw, a cross-platform library for reading/converting various file formats. An attacker can exploit this vulnerability to cause remote code execution by sending a specially crafted image file to the victim's computer. The image file must be crafted in a particular way, which is not possible with most common image editing programs.
The vulnerable code is located inside of function RawImage::read(). Before calling the vulnerable function, the caller should create an empty buffer and use mBuffer as pointer to it. This will avoid triggering the overflow when mBuffer is passed as parameter.
This vulnerability was found by Sebastian Schinzel (@sebschins) during Google Code-In 2016.
CVE-2020-35533: Remote Code Execution via Image File
A buffer overflow vulnerability has been discovered in LibRaw, a cross-platform library for reading/converting various file formats. This leads to remote code execution, but the application does not store any information about the images it reads. In other words, there is no way to determine if the image was maliciously modified via this vulnerability.
The discovery of this vulnerability demonstrates how quickly vulnerabilities are being discovered and patched in today's digital age. Company's like Facebook are constantly updating their software so that they can be immune to these types of exploits. Even with all of the research companies put into their software, new vulnerabilities still arise each day. We must continue to be vigilant as hackers attempt to take advantage of these vulnerabilities and prevent them from doing so.
Timeline
Published on: 09/01/2022 18:15:00 UTC
Last modified on: 09/21/2022 20:26:00 UTC