On March 12th, 2018 IBM released security patches for IBM Cognos Analytics 11.1.7, 11.2.0, 11.2.1, and 11.2.2 and X-Force ID 204465 has updated to reflect this. These patches address the cross-site request forgery vulnerability. Users should update to the latest version as soon as possible.
IBM Cognos Analytics Vulnerable To Cross-Site Request Forgery
Cross-site request forgery (CSRF) is a type of security vulnerability found in some websites where one part of the site unknowingly allows an attacker to make a request on behalf of a different site visitor. The vulnerability can occur when a web application takes action based on user input that comes from another site. This is typically due to the lack of input validation, or incorrect validation. IBM Cognos Analytics 11.1 and 11.2 are vulnerable to this attack, while X-Force ID 204465 has updated to reflect this.
If you have not already updated your software, we recommend that you do so now. If you are unsure how to update the software, please contact your technical support team for assistance or refer to the installation instructions provided by IBM Support.
IBM Cognos Analytics and X-Force ID 204465 Vulnerability
IBM Cognos Analytics is a business intelligence (BI) platform that provides an integrated pre-built analytics suite. The product can be configured to enable simple, easy-to-use analytical reporting and data visualization.
A cross-site request forgery vulnerability was discovered in the web client in IBM Cognos Analytics 11.1.7, 11.2.0, 11.2.1, and 11.2.2 and X-Force ID 204465 on March 12th, 2018. The vulnerability could have allowed an attacker to execute arbitrary scripts from World Wide Web Pages (WWW) that use the vulnerable software by interacting with the affected client to read content from the server as part of a normal browser session without requiring user interaction or knowledge of the attack scenario or machine credentials to exploit this vulnerability
The risk of exploitation depends on how click events are implemented in specific applications that use IBM Cognos Analytics, but it is likely most impacted by malicious HTML document links or external data sources with insecure HTTP connections that could allow an attacker to register a new account under certain conditions.
IBM Cognos Analytics 11.1.7
, 11.2.0, 11.2.1, and 11.2.2 and X-Force ID 204465
This month IBM released security patches for IBM Cognos Analytics 11.1.7, 11.2.0, 11.2.1, and 11.2.2 and the X-Force ID 204465 has updated to reflect this release as well as a new cross-site request forgery vulnerability that was discovered when it was exploited in real world attacks.
IBM Cognos Analytics
- CVE-2021-29823
The flaw affects the following models:
IBM Cognos Analytics 11.1.7, 11.2.0, 11.2.1 and 11.2.2
X-Force ID 204465
IBM Cognos Analytics 11.2.0 and 11.2.1 Patches
The following two patches released on March 12th, 2018 address the cross-site request forgery vulnerability. Users should update to the latest version as soon as possible:
IBM Cognos Analytics 11.2.0 Patch
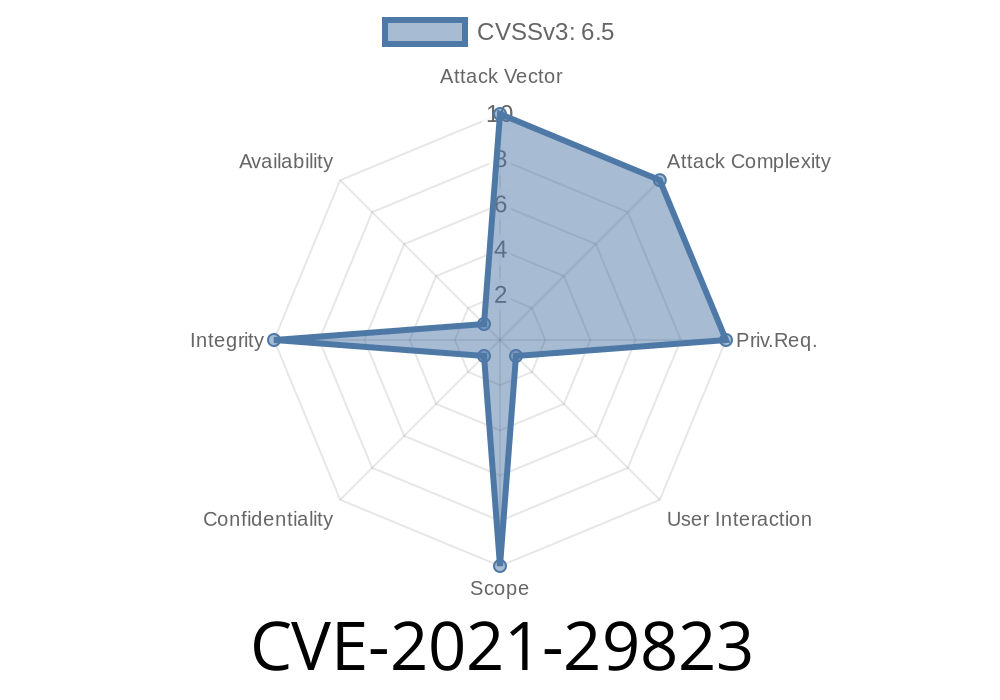
CVE-2021-29823
Cross-Site Request Forgery (CSRF) vulnerability in IBM Cognos Analytics 11.2 and 11.2.1 allows attackers to execute commands via crafted URLs that are not properly handled by the "getUrl" command of the "jQuery" JavaScript library. IBM Cognos Analytics versions 11.2 and 11.2.1 are vulnerable to CSRF attacks because they don't validate parameter values before calling getUrl() to construct a URL, which may result in an arbitrary execution of the malicious script on a user's system with privileged rights over resources controlled by another application, like a web server or database server.. This flaw occurs when users send an XSS payload using a GET request to one of these URLs:
http://cognos/getConfig?lang=en&folder=myFolder&id=3
http://cognos/getConfig?lang=en&folder=myFolder&id=4
http://cognos/getConfig?lang=en&folder=myFolder&id=5
When getConfig() is called, it calls getUrl() with a malformed parameter value and does not validate it
Timeline
Published on: 09/01/2022 19:15:00 UTC
Last modified on: 09/07/2022 14:10:00 UTC