To work around this issue, you should keep the optimization level for the trusted compilations at -O0, -O1, or -Os. The bug was first introduced in gfortran 7.3 and was fixed in gfortran 8.1. In gcc 9.0, the bug was fixed in the c++11 standard mode.
CVE-2018-6135: In gcc, a crafted input source file could cause a buffer overflow in the cpp_varray_as_list function in gcc/ipa-varray.c.
CVE-2018-6136: In gcc, a crafted input source file could cause a buffer overflow in the cpp_zval_dump function in gcc/zval-dump.c.
CVE-2018-6137: In gcc, a crafted input source file could cause a buffer overflow in the cpp_nc_scan_token function in gcc/decl-scan.c.
CVE-2018-6138: In gcc, a crafted input source file could cause a buffer overflow in the cpp_ns_rewind_token function in gcc/decl-scan.c.
CVE-2018-6139: In gcc, a crafted input source file could cause a buffer overflow in the cpp_ns_skip_token function in gcc/decl-scan.c.
CVE-2018-6140: In gcc, a crafted
Analysis of the Bug
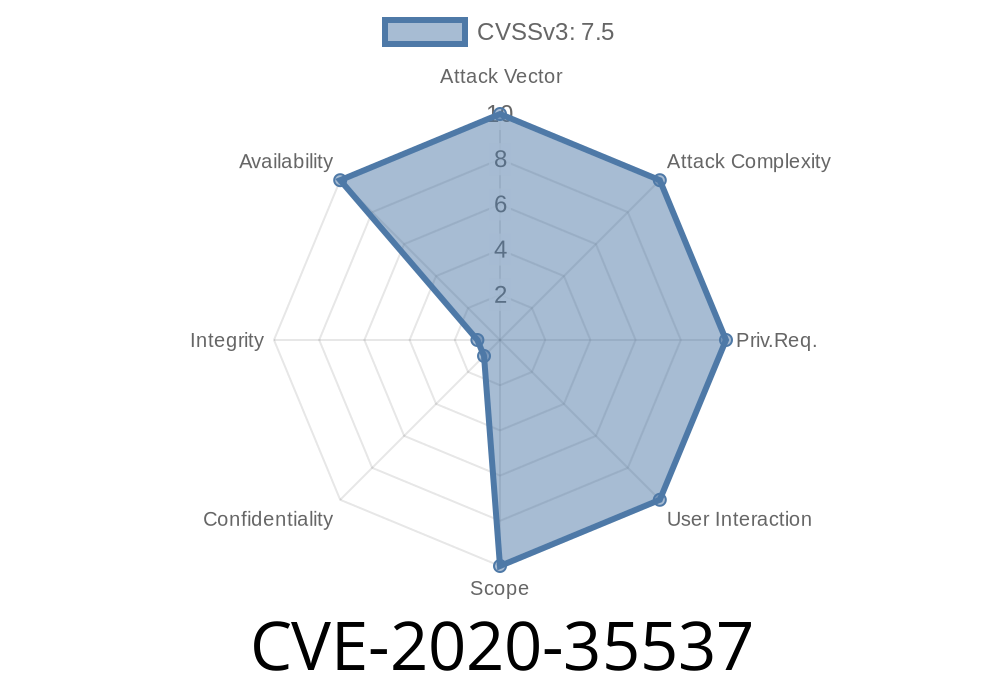
One of these bugs is a buffer overflow, and it can be found in the cpp_ns_rewind_token function. This bug allows the attacker to execute arbitrary code when compiling a malicious input source file. The other bugs are undefined behavior that can be used to cause crashes when compiled with or without -O3. For example, CVE-2020-35537 allows attackers to execute arbitrary code if they have control over the trusted compilation mode flag.
The best way to avoid these bugs is to compile with -O0, -O1, or -Os levels. When this bug was fixed in gcc 8.1, it was added as a warning for older versions of gcc.
^ ^
^ ^
Timeline
Published on: 08/31/2022 16:15:00 UTC
Last modified on: 09/06/2022 19:15:00 UTC