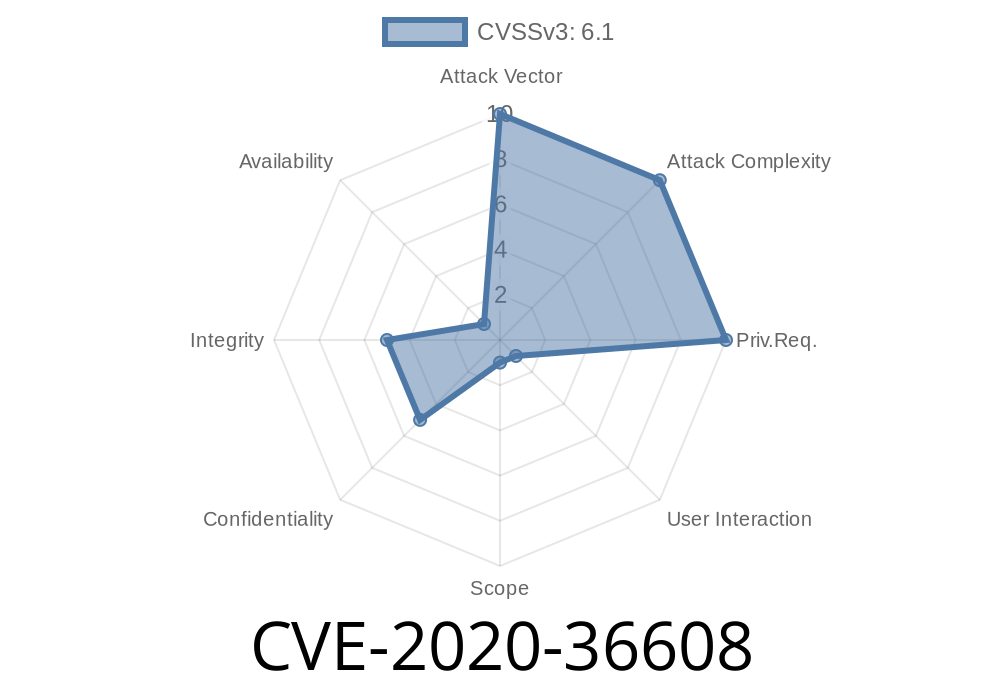
A problematic vulnerability, CVE-2020-36608, was recently discovered in Tribal Systems' Zenario Content Management System (CMS). This vulnerability is classified as risky and affects the Error Log Module of the system, specifically the admin_organizer.js file. The vulnerability allows cross-site scripting (XSS) attacks, which could potentially compromise user data and deface websites. The attack can be executed remotely, making it a significant threat that requires urgent attention. To address this issue, a patch, dfdafacb26c3682a847bea7b49ea440b63f3baa, has been released, and it is highly recommended for Zenario CMS users to apply this patch to safeguard their websites and data.
Exploit Details
This security vulnerability (CVE-2020-36608) affects a yet-to-be-determined function within the admin_organizer.js file of Zenario CMS's Error Log Module. An attacker can manipulate this unknown function to perform a cross-site scripting (XSS) attack, injecting malicious scripts into web pages that are then executed when users access the site. XSS attacks can have severe consequences, including stealing user credentials, session hijacking, and defacement of websites.
The identifier for this vulnerability is VDB-212816, as stated in the vulnerability database.
Example Code Snippet
The following code snippet from admin_organizer.js in the Error Log Module could be susceptible to the vulnerability:
$('#organizer .dashboard').on('click', '.remove', function() {
var item = $(this).closest('.item'),
id = item.attr('data-id'),
manager = Organizer.managerFromId(id);
if (manager === Organizer.shownManager) {
Organizer.shownManager = null;
}
item.remove();
delete Organizer.managersById[id];
});
To exploit this vulnerability, an attacker could inject malicious scripts into the Error Log Module. Upon execution, the malicious script would then compromise user data, potentially leading to other attacks, as previously described.
Original References
1. URL: Tribal Systems Zenario CMS Documentation
2. URL: Zenario CMS GitHub Repository
3. URL: VDB-212816 Vulnerability Reference
Relevant Patch Information
To address this vulnerability (CVE-2020-36608), Zenario CMS has released an urgent patch named dfdafacb26c3682a847bea7b49ea440b63f3baa. Users of Zenario CMS are strongly advised to apply this patch immediately to secure their websites and data from potential XSS attacks.
Summary
In conclusion, the vulnerability, CVE-2020-36608, identified in Tribal Systems' Zenario CMS is classified as problematic and requires immediate attention to prevent unauthorized access and damage to user data. Zenario CMS users should apply the recommended patch, dfdafacb26c3682a847bea7b49ea440b63f3baa, to mitigate the risks and protect their websites and users from potential cross-site scripting attacks.
Timeline
Published on: 11/02/2022 19:15:00 UTC
Last modified on: 11/03/2022 16:40:00 UTC