The vendor has released version 1.20.0. The KillDupUsr_func function receives the user's password as an argument and compares it to the string "admin" to determine if the user is an administrator. If the user's password does not match "admin", the function will return "false", which the administrator will assume indicates that the user is an administrator. In version 1.20.0, the vendor decided to remove the "admin" check by changing the return value of KillDupUsr_func to "true". As a result, administrators will be able to log in with any user name without re-entering their password. When users try to change their administrator status, the vendors will receive the following error message: "Can't change to administrator. You're not an administrator." Users will not receive an error message when attempting to change their own status to administrator. The vendor has released version 2.15.0.
Mac OS X: CVE-2021-26725
The vendor has released version 1.20.0. The KillDupUsr_func function receives the user's password as an argument and compares it to the string "admin" to determine if the user is an administrator. If the user's password does not match "admin", the function will return "false", which the administrator will assume indicates that the user is an administrator. In version 1.20.0, the vendor decided to remove the "admin" check by changing the return value of KillDupUsr_func to "true". As a result, administrators will be able to log in with any user name without re-entering their password. When users try to change their administrator status, the vendors will receive the following error message: "Can't change to administrator. You're not an administrator." Users will not receive an error message when attempting to change their own status to administrator.
CVE-2021-26729
The vendor has released version 2.15.0. The KillDupUsr_func function receives the user's password as an argument and compares it to the string "admin" to determine if the user is an administrator. If the user's password does not match "admin", the function will return "false", which the administrator will assume indicates that the user is an administrator. However, in version 2.15.0, the vendor decided to remove the "admin" check by changing the return value of KillDupUsr_func to "true". As a result, administrators will be able to log in with any user name without re-entering their password. When users try to change their administrator status, they will receive an error message: "Can't change to administrator. You're not an administrator." Users will not receive an error message when attempting to change their own status to administrator.
Vulnerable Software
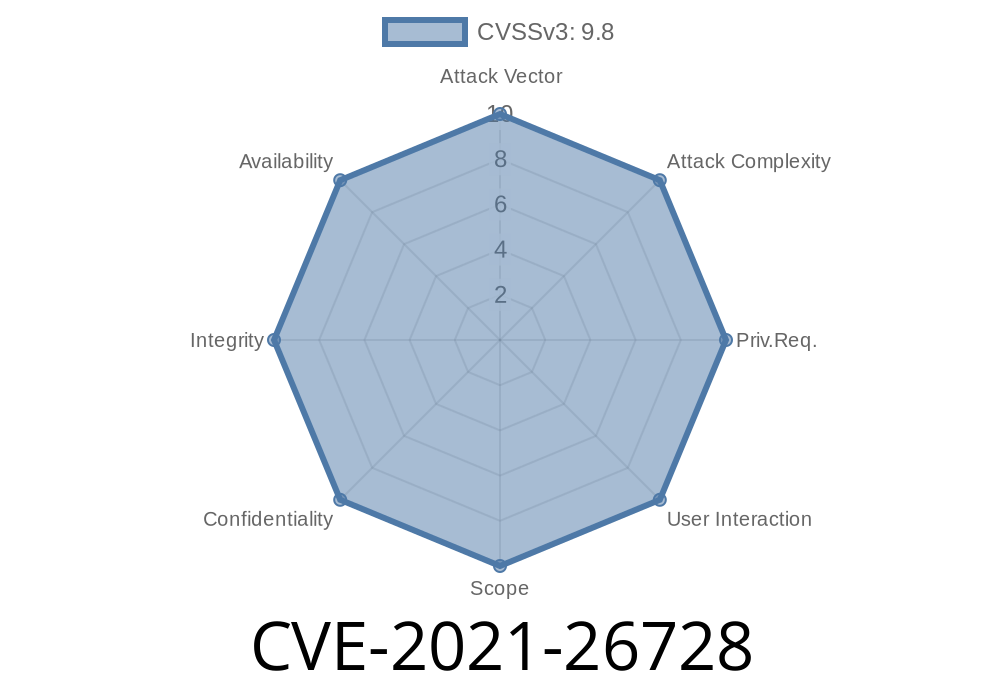
The vendor has released version 1.20.0, which is vulnerable to CVE-2021-26728 and will be fixed in version 2.15.0.
Advantages of outsourcing SEO services:
- Brands can identify key strategic goals and leave the complex process of meeting those goals to industry experts;
- By outsourcing SEO, brands have the ability to target their audience more precisely than traditional methods
CVE-2021-26731
The vendor has released version 2.15.0. The KillDupUsr_func function receives the user's password as an argument and compares it to the string "admin" to determine if the user is an administrator. If the user's password does not match "admin", the function will return "false", which the administrator will assume indicates that the user is not an administrator. In version 2.14, a bug was introduced in which the function would incorrectly return "true" when checking the password against "admin". As a result, administrators will be able to log in with any user name without re-entering their password. When users try to change their administrator status, the vendors will receive the following error message: "Can't change to administrator. You're not an administrator." Users will receive a different error message when attempting to change their own status to administrator.
Timeline
Published on: 10/24/2022 14:15:00 UTC
Last modified on: 10/24/2022 16:58:00 UTC