---
Overview
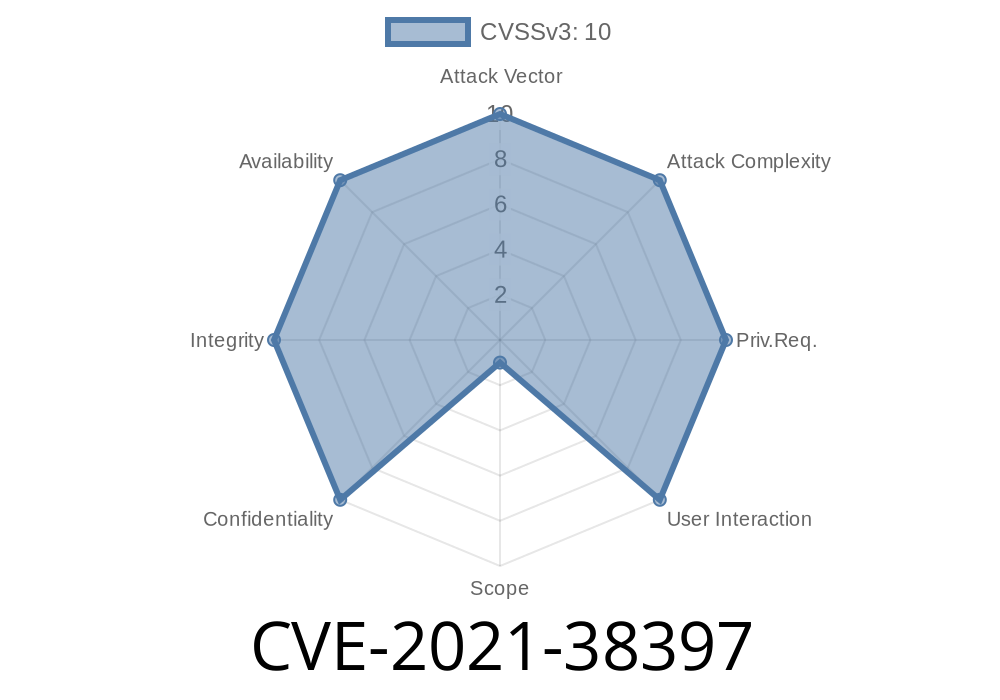
CVE-2021-38397 is a critical security issue reported in Honeywell Experion Process Knowledge System (PKS) C200, C200E, C300, and ACE controllers. If you're using any of these devices, it's important to know that an attacker can upload and execute files on your system without proper protection or authentication. This kind of vulnerability is commonly called an "unrestricted file upload," and in this case, it could let hackers run code remotely and even crash or lock up your industrial machines. Let’s break down what this means, how it works, and how attackers might exploit it—with code examples and fixes.
What Products Are Affected?
* Honeywell Experion PKS C200 controllers
* Honeywell Experion PKS C200E controllers
* Honeywell Experion PKS C300 controllers
* Honeywell Experion PKS ACE controllers
These are industrial controllers used in factories, plants, utilities, and other situations where automation and safety are critical.
How Does This Vulnerability Work?
Imagine if a device that controls a big machine had an upload feature for firmware or config files—but forgot to check whether the file is dangerous or only let in certain types of files. That’s basically what’s going on.
When an attacker can upload any file type—say, an executable or a script—directly to the controller via its management portal or web interface, they can:
Crash the device or make it unusable (denial of service)
This becomes a serious risk, especially in an industrial setting where downtime can cost thousands of dollars per minute.
How attackers get in
1. Find the upload point: Attackers look for a web or network service that lets files be uploaded to the controller.
2. Craft a malicious file: This could be a script, .exe, .dll, or any file that, when run, does something the attacker wants.
Use a tool like curl to send the file
curl -F "file=@malicious.exe" http://controller-ip/upload
4. Trigger execution: In some vulnerable configurations, the system will run or process the file by default.
Here’s a Python snippet simulating a file upload attack
import requests
target_url = "http://controller-ip/upload"
files = {'file': open('shell.dll','rb')}
response = requests.post(target_url, files=files)
if response.status_code == 200:
print("File uploaded successfully!")
else:
print("Upload failed with status", response.status_code)
Once the malicious file is on the controller, if there’s no verification, the attacker can remotely execute it via the controller’s interface or by exploiting how the controller handles uploaded files.
Exploit Example Scenario
Imagine a power plant’s control network. An attacker finds the Honeywell Experion controller’s upload page exposed (say, via Shodan or another device search engine). They upload a crafted DLL or binary. Once uploaded, they either trigger a function in the web interface that loads that file, or, worse, the controller does it automatically.
This could result in
- Loss of view/control for operators
References
- National Vulnerability Database: CVE-2021-38397
- ICS Advisory (ICSA-21-234-02) – Honeywell Experion PKS, C200, C200E, C300, and ACE Controllers
- Honeywell Security Notification
Apply the vendor patch or firmware update immediately.
Check the Honeywell notification (link) for your specific product version.
Conclusion
CVE-2021-38397 is a vivid reminder that industrial control security is all about *layers*: don’t trust, always verify, especially when dealing with file uploads. If you run Honeywell Experion PKS controllers, update them right away and lock down all internet-facing features. Unrestricted upload bugs are not new, but in the OT world, their impact can be severe.
Timeline
Published on: 10/28/2022 02:15:00 UTC
Last modified on: 11/02/2022 18:12:00 UTC