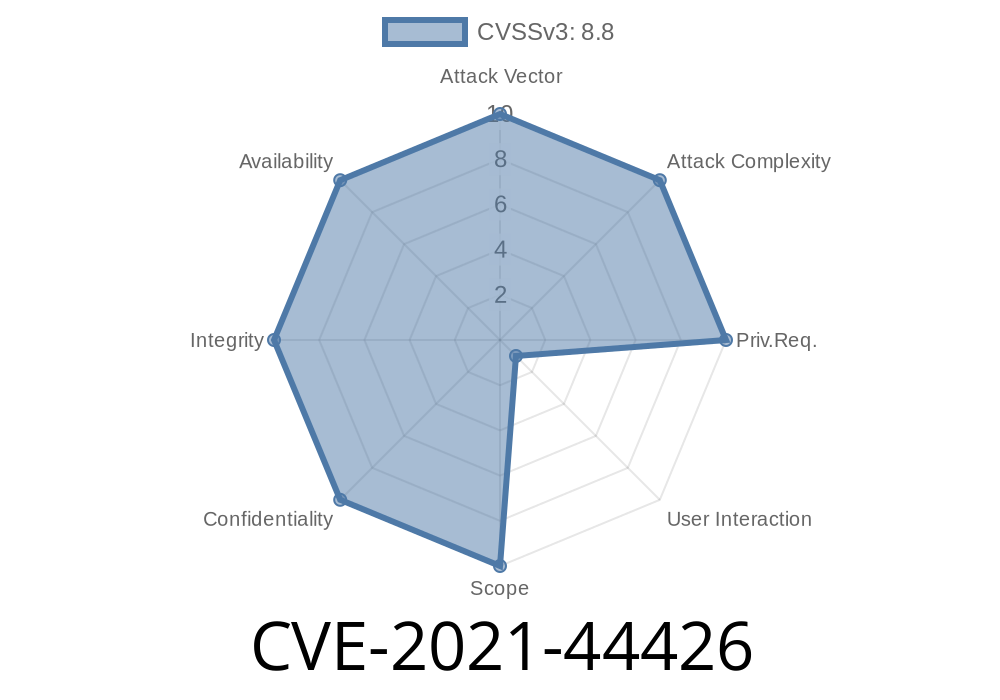
This can be exploited by a remote attacker to upload arbitrary files to a victim's local ~/Downloads/ directory. This can result in a remote attacker being able to execute arbitrary code on the vulnerable client, if the attacker is also connected via AnyDesk to the same remote machine. An attacker can leverage this issue to conduct file upload attacks to achieve arbitrary code execution or data exfiltration.
An issue was discovered in AnyDesk before 6.2.6 and 6.3.x before 6.3.5. It is possible to route requests from AnyDesk clients via a network address (hostname) other than the client's hostname. In other words, it is possible to spoof clients' hostnames via URL redirection attacks. This can be exploited by a remote attacker to send requests to the client, but respond with the remote server's own response. This results in the client being redirected to the attacker's server. An attacker can leverage this issue to conduct hostname spoofing attacks.
An issue was discovered in AnyDesk before 6.2.6 and 6.3.x before 6.3.5. It is possible to spoof the client's IP address via DNS hijacking attacks. An attacker can alter the client's DNS settings to redirect the client to their own server. This can be exploited by a remote attacker to send requests to the client, but respond with the remote server's own response. This results in the client being redirected to the attacker
Security Recommendations
All users of AnyDesk are advised to upgrade to the latest release.
A remote attacker may be able to execute arbitrary code on the vulnerable client; this can result in a loss of confidentiality, integrity, and availability of the client software or data.
Upgrade AnyDesk to version 6.2.6
Vulnerable Packages
AnyDesk: 6.2.6
AnyDesk Desktop: 2.1.1-x
AnyDesk Server: 2.1.1-x
Timeline
Published on: 09/12/2022 21:15:00 UTC
Last modified on: 09/16/2022 15:09:00 UTC