However, if the device is connected to a network not accessible from the internet, an attacker would have to have access to the device to exploit this vulnerability. To exploit this vulnerability, an attacker would have to be on the same network as the Linksys E5350 WiFi Router. An attacker would have to have access to the Linksys E5350 WiFi Router's web interface. An attacker can exploit this vulnerability by accessing the /SysInfo.htm URI with a device with remote management enabled and login privileges to the device. If remote management is enabled and the user has login privileges to the device, an attacker can exploit this vulnerability. End users who are not remote management enabled or do not have login privileges to the device can also access this web page by directly accessing the /SysInfo.htm URI with a device with internet access. However
Vulnerable Linksys E5350 WiFi Routers
An attacker could use this vulnerability to obtain sensitive information, such as the current system time, network access point name (APN), and wireless network name.
By default, Linksys E5350 WiFi Routers are vulnerable to this issue. To protect against exploitation of this issue, Linksys E5350 WiFi Routers should be configured with a password that is at least eight characters long.
Vulnerable Software:
Linksys E5350 WiFi Router
A vulnerability in the Linksys E5350 WiFi Router has been discovered that could allow an attacker to exploit a system.
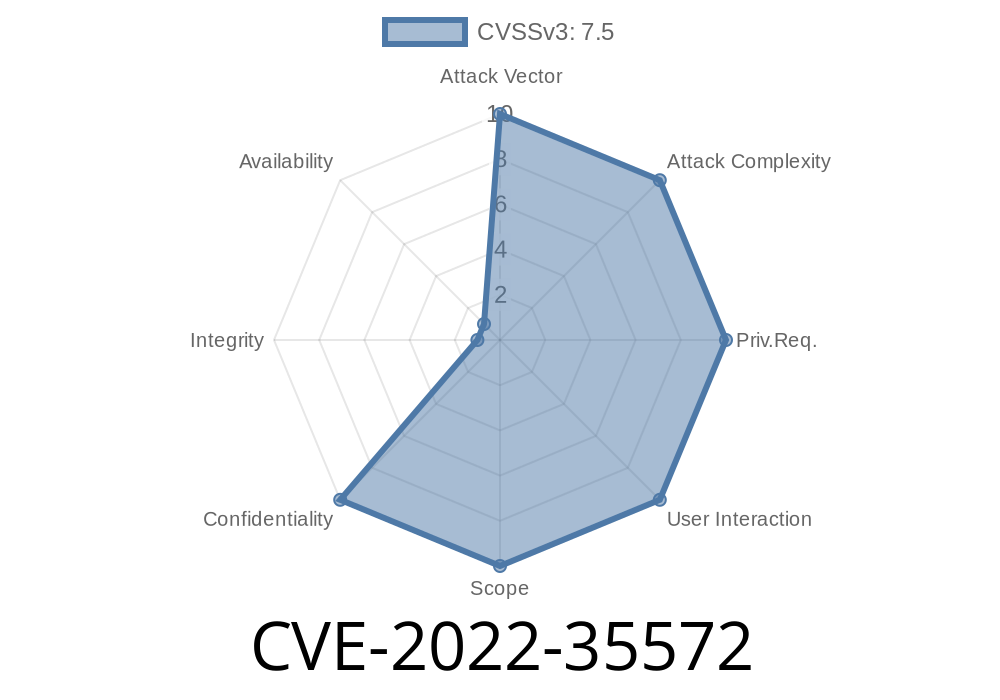
Vulnerability Scope and Requirements
The vulnerability is caused by a web interface that does not have authentication and remote management enabled. An attacker must have valid credentials to the device to exploit this vulnerability. This vulnerability can be exploited on Linksys E5350 WiFi Routers that are connected to a network not accessible from the internet and have the remote management feature enabled.
Timeline
Published on: 09/12/2022 22:15:00 UTC
Last modified on: 09/14/2022 17:44:00 UTC