XSS vulnerabilities can be exploited to steal data, create links for redirecting to malicious URLs, or inject arbitrary web script into the application's response. The recommended solution is to avoid the use of the title parameter in theme settings requests. In v1.7.9 and later, this issue has been fixed by updating to the latest version of the cms-framework on GitHub. For versions prior to v1.7.9, the following mitigations can be applied: - Avoid using the title request parameter in theme settings requests. - If stuck with an earlier version of the cms-framework, upgrade to the latest version on GitHub, at your own risk.
Solution: Avoid using the title request parameter in theme settings requests
The title request parameter is no longer supported in version 1.7.9 and later of the cms-framework, so this vulnerability has been fixed by updating to the latest version. If you are using an earlier version, you can mitigate this vulnerability by avoiding the use of the title request parameter.
Stored XSS vulnerability and how to fix it
If you're using WordPress, it is possible to create a stored XSS vulnerability. Luckily, there is an easy fix for this. In earlier versions, these vulnerabilities could be exploited by using the title request parameter in theme settings requests. However, with WordPress v1.7.9 and later, this has been fixed by updating to the latest version of the cms-framework on GitHub. To mitigate this issue on older versions, you can avoid using the title request parameter in theme settings requests or upgrade to the latest version of the cms-framework (v1.7.9 or later) on GitHub at your own risk if stuck with an earlier version. If you're unsure about which version of the CMS framework is running on your website and are unable to upgrade to v1.7.9 or later, we recommend that you contact our support team at support@avastthreatcenter.com
Stored XSS vulnerability
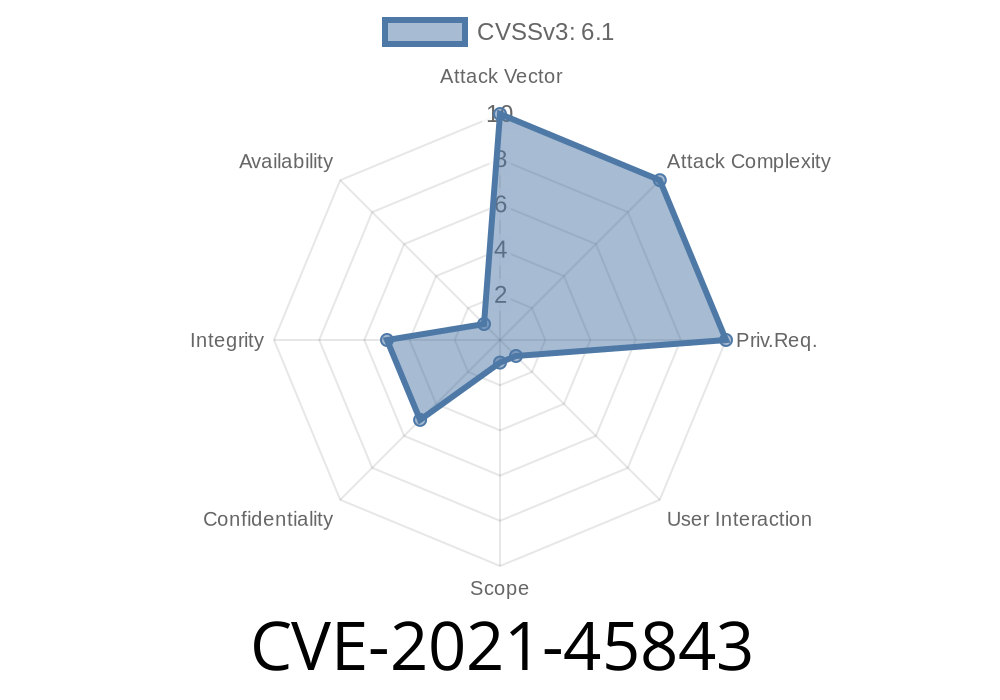
Vulnerability CVE-2021-45843 was discovered on October 31, 2018 and is stored XSS vulnerability that can be exploited to steal data, create links for redirecting to malicious URLs, or inject arbitrary web script into the application's response. The recommended solution is to avoid the use of the title parameter in theme settings requests. In v1.7.9 and later, this issue has been fixed by updating to the latest version of the cms-framework on GitHub. For versions prior to v1.7.9, the following mitigations can be applied: - Avoid using the title request parameter in theme settings requests. - If stuck with an earlier version of the cms-framework, upgrade to the latest version on GitHub, at your own risk.
Timeline
Published on: 09/29/2022 03:15:00 UTC
Last modified on: 09/30/2022 19:40:00 UTC