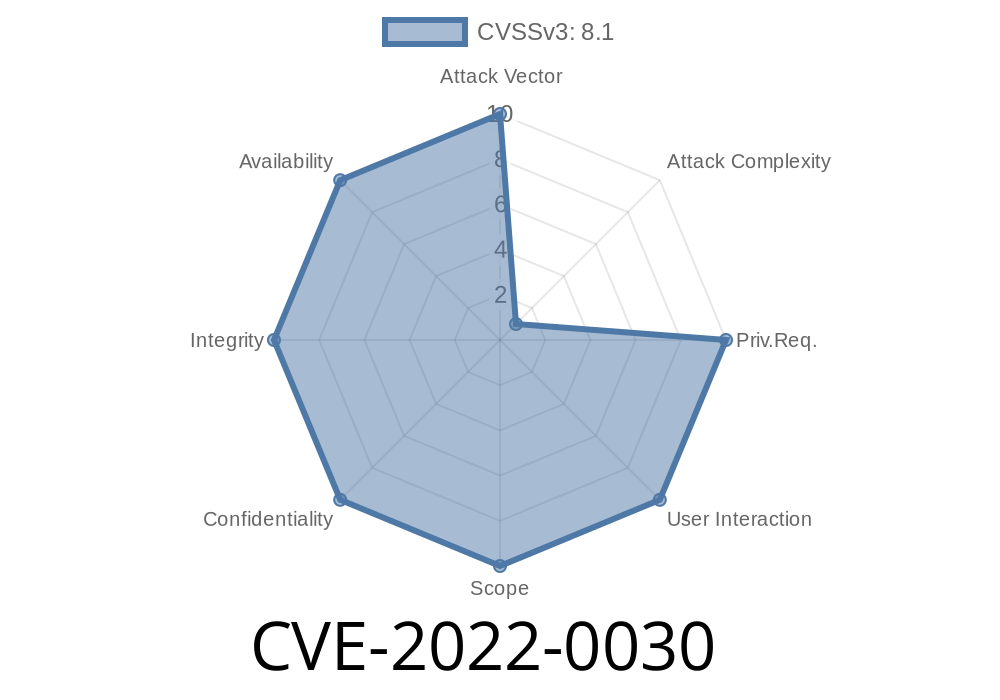
This authentication bypass vulnerability can be exploited remotely by crafting a malicious email message or a malicious URL that is redirected to a specially crafted URL. Network-based attackers must have valid credentials to exploit this vulnerability.
The authentication bypass vulnerability can be exploited by a network-based attacker to impersonate an existing PAN-OS administrator and perform privileged actions. Panorama appliance administrators and PAN-OS firewall administrators must be aware of this vulnerability and protect against attempts to exploit it.
PAN-OS 8.1 is a modified version of the original PAN-OS. It has been modified to support IPv6, firewall and VPN configuration changes, and other changes.
To exploit this authentication bypass vulnerability, an attacker must have valid administrator credentials. An attacker must be PoP (point of presence) to the target network. To exploit this authentication bypass vulnerability, an attacker must have valid administrator credentials. An attacker must be PoP (point of presence) to the target network. - Exploitation details - This authentication bypass vulnerability can be exploited by a network-based attacker to impersonate an existing administrator. An attacker must have valid administrator credentials to exploit this authentication bypass vulnerability
Vulnerability overview
A vulnerability was discovered that can be exploited by a network-based attacker to impersonate an existing administrator and perform privileged actions. Panorama appliance administrators and PAN-OS firewall administrators must be aware of this vulnerability and protect against attempts to exploit it.
The authentication bypass vulnerability can be exploited remotely by crafting a malicious email message or a malicious URL that is redirected to a specially crafted URL. Network-based attackers must have valid credentials to exploit this vulnerability.
PAN-OS 8.1 authentication bypass vulnerability - Technical overview
This authentication bypass vulnerability can be exploited remotely by crafting a malicious email message or a malicious URL that is redirected to a specially crafted URL. Network-based attackers must have valid credentials to exploit this vulnerability.
PAN-OS 8.1 is a modified version of the original PAN-OS. It has been modified to support IPv6, firewall and VPN configuration changes, and other changes.
To exploit this authentication bypass vulnerability, an attacker must have valid administrator credentials. An attacker must be PoP (point of presence) to the target network. To exploit this authentication bypass vulnerability, an attacker must have valid administrator credentials. An attacker must be PoP (point of presence) to the target network.
PAN-OS 8.1 Authentication Bypass Vulnerability - Proposal
Administrators should disable the 'Authentication by Password' option for the Web UI and API (application programming interface). This will protect against this vulnerability. Additionally, administrators should implement strong password policies in order to mitigate any vulnerabilities that may be present.
Firewall administrators should enable authentication between a PAN-OS appliance and an external network device, such as a firewall or VPN concentrator. This will protect against this vulnerability.
Network-Based Attack Methods
An attacker must have valid administrator credentials to exploit this authentication bypass vulnerability. An attacker can be a PoP (point of presence) or a malicious insider.
PAN-OS 8.1 is a modified version of the original PAN-OS. It has been modified to support IPv6, firewall and VPN configuration changes, and other changes.
Timeline
Published on: 10/12/2022 17:15:00 UTC
Last modified on: 10/14/2022 15:33:00 UTC