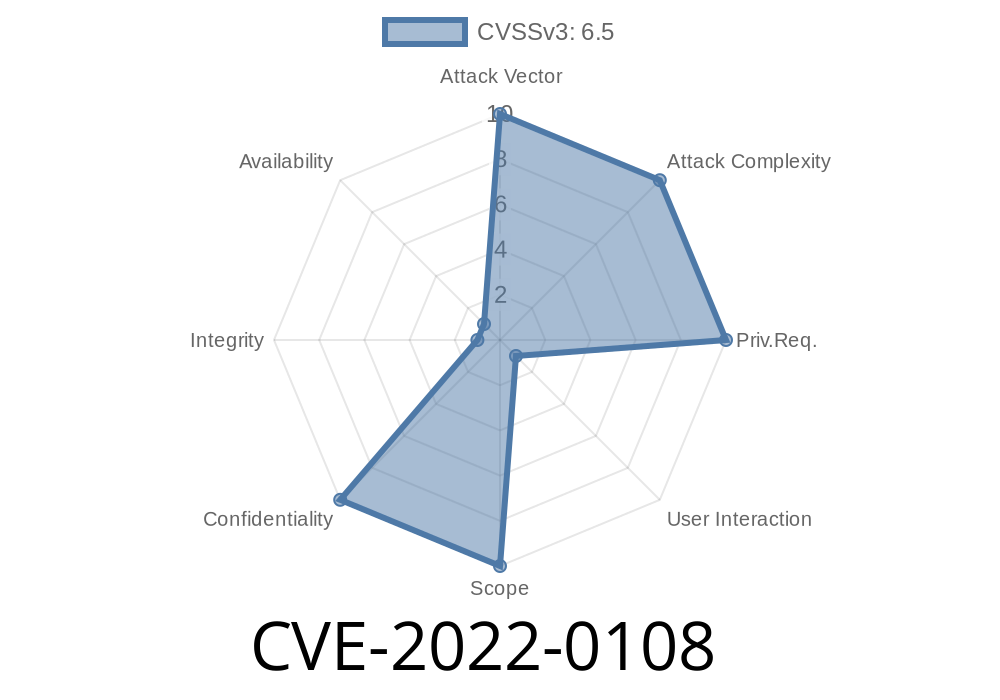
This issue was fixed in Googles implementation of Navigation in Google Chrome 97.
To exploit this issue, an attacker would have to convince a user to visit a malicious website. End users are not vulnerable to data leakage via Navigation unless the user is coerced into visiting a malicious website.
An example of such a situation could be a phishing attack where the malicious website requests the user's session cookie. If the user is then convinced to visit an attacker-controlled website, the session cookie could be used to access the session history on the original website and thereby read the user's e-mail, chat messages, or other private data.
Impact: An attacker could leverage this issue to access the session history of a website or read the content in private messages. This issue affects all users of Google Chrome on Windows, Mac, and Linux operating systems.
Inappropriate implementation in Navigation in Google Chrome prior to 97.0.4692.71 allowed a remote attacker to perform a cross-origin request and leak the origin via a crafted HTML page.
To exploit this issue, an attacker would have to convince a user to visit a malicious website. End users are not vulnerable to data leakage via Navigation unless the user is coerced into visiting a malicious website.An example of such a situation could be a phishing attack where the malicious website requests the user's session cookie
The Issue
A vulnerability in the Navigation feature in Google Chrome prior to version 97.0.4692.71 allows a remote attacker to perform a cross-origin request, leak the origin via a crafted HTML page, and read the content of private messages if exploited.
What is Navigation?
Navigation is the ability to switch between web pages in a browser. It's not just about moving between different pages, but also getting a better view of the content that's on each page. Navigation is important because it allows a user to easily move around the web, and helps users find what they're looking for more quickly.
Bypass CSRF Protection
The content of the window can be changed by an attacker, for example, by changing the text on a webpage with a malicious URL.
The Content Security Policy (CSP) should not be bypassed. If it is bypassed, it is possible to steal user session cookies that could then be used to access the user's session history and read personal information.
There are many ways to bypass the CSRF protection mechanism in Google Chrome:
- A man-in-the-middle attack where a third party intercepts and substitutes communication between the browser and another party.
- Compromising another website or server as part of a targeted attack against a specific website or domain.
This issue affects all users of Google Chrome on Windows, Mac, and Linux operating systems.
What is WebNavigation?
WebNavigation is a feature in the browser that allows developers to create and manage web applications.
This feature enables developers to write scripts that can open new windows, tabs, or navigate back and forth between pages in their web application.
The Navigation API allows developers to create their own event-based system for navigating around the web application.
The Navigation API uses JavaScript Event Listeners, which are objects that are programmed as listeners for certain events on the page. This type of object is called an "Event Listener". The Navigation API also provides methods for managing activities such as handling navigation requests and performing actions when a user presses a button on the page. From these methods, developers can retrieve information about what has happened on their page so they know where users are or how to handle other interactions on the page that occur during navigation.
This issue was fixed in Google Chrome 97.0.4692.71
Timeline
Published on: 02/12/2022 00:15:00 UTC
Last modified on: 04/19/2022 03:29:00 UTC
References
- https://crbug.com/1248444
- https://chromereleases.googleblog.com/2022/01/stable-channel-update-for-desktop.html
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/5PAGL5M2KGYPN3VEQCRJJE6NA7D5YG5X/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/KQJB6ZPRLKV6WCMX2PRRRQBFAOXFBK6B/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/MRWRAXAFR3JR7XCFWTHC2KALSZKWACCE/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0108