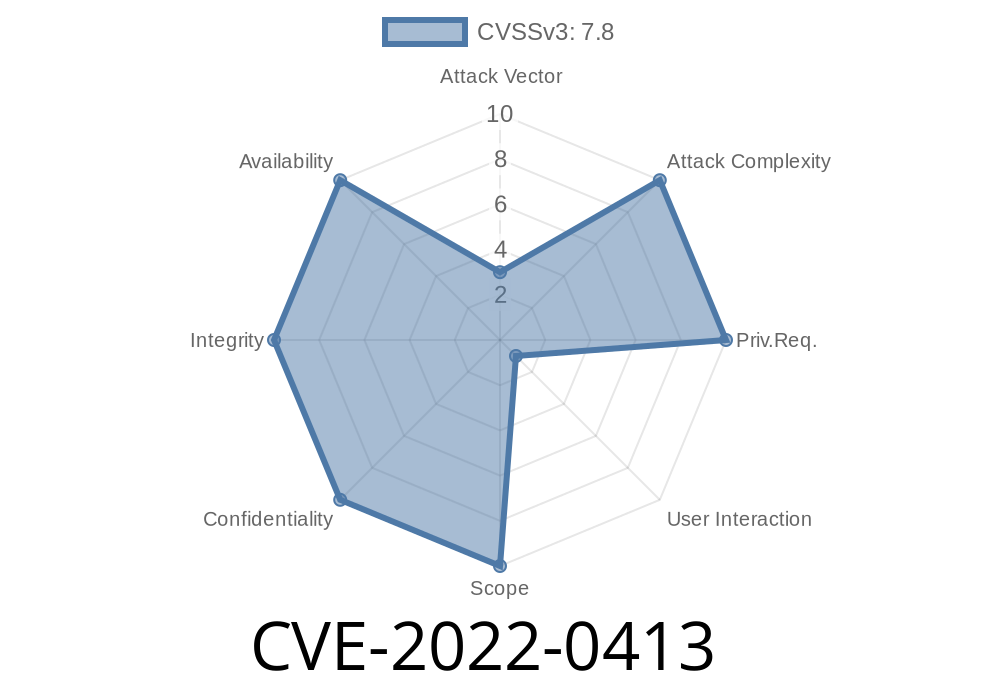
Vim is one of the most popular text editors in the world, widely used by developers, sysadmins, and hobbyists alike. Being such a crucial tool, its security is paramount. In early 2022, a critical vulnerability was discovered in Vim—CVE-2022-0413, a "use-after-free" memory bug, which could allow attackers to execute arbitrary code.
In this post, we'll break down what this vulnerability is, how it can be exploited, walk through some technical details (with code snippets), and point you to the original advisories and patches.
What Is a Use-After-Free Vulnerability?
A *use-after-free* flaw occurs when a program continues to use a chunk of memory after it's been deallocated (freed). This mistake can do everything from causing a crash to allowing attackers to gain control of a program—especially dangerous in programs like Vim that often process untrusted files.
Background: How CVE-2022-0413 Was Introduced
- Repository: https://github.com/vim/vim
Vulnerable versions: Prior to Vim 8.2 (before patch 8.2.4112)
- CVE details: https://nvd.nist.gov/vuln/detail/CVE-2022-0413
The bug existed due to improper management of memory when handling invalid spell file names. If a crafted input led Vim to process such a file, it was possible to trick Vim into using pointers that had already been freed—creating the classic use-after-free scenario.
Technical Details and Code Snippet
Let's look at a simplified piece of C code inspired by the vulnerable spot (based on Vim's patch):
char_u *fname = alloc_fname(fname_base); // Allocate memory
if (some_error_occurred(fname)) {
vim_free(fname); // Free memory on error
return FAIL;
}
// ... Later, mistakenly using fname after it was freed
process_file(fname); // Use-after-free if 'fname' is already freed!
In the real bug, the function eval_spellfile() could cause such a scenario. When cleaning up after errors, the code would sometimes free a pointer, but later continue using it.
How Could an Attacker Exploit This?
- Step 1: Craft a malicious spell file or a sequence of commands that cause Vim to load the bad file.
Step 3: Trick Vim into using the previously freed memory.
If the attacker could control what data occupies the freed memory, they might inject code, leading to memory corruption, a segmentation fault, or even arbitrary code execution.
`vim
set spellfile=/tmp/invalidname
Vim mishandles the pointer, possibly crashing or (with enough effort) leading to arbitrary code.
> Note: As of the time of writing, no public remote exploit is known, but a determined attacker (such as one sending you a malicious Vim config or file) could potentially exploit this.
Patch Reference
- GitHub Commit Fixing the Issue
Excerpt from the fix
if (fname != NULL) {
vim_free(fname);
fname = NULL; // Properly nullify the pointer!
}
Setting the pointer to NULL is a standard safety move—it stops accidental reuse.
How to Protect Yourself
Upgrade Vim!
- If you're using a version prior to 8.2.4112, upgrade immediately from https://www.vim.org/download.php.
Linux distributions shipped the patch quickly. Update your packages.
Do not open untrusted files, especially those containing Vim configuration or spell files.
Further Reading
- National Vulnerability Database: CVE-2022-0413
- Vim Security Patch (8.2.4112)
- GitHub Issue Discussion
Conclusion
CVE-2022-0413 is a great reminder that even mature, well-maintained software can have dangerous bugs. "Use-after-free" issues are tricky; they may seem like obscure memory problems, but their consequences can be severe.
Stay up to date, stay safe—and if you ever run vim --version, make sure you’re patched!
Timeline
Published on: 01/30/2022 15:15:00 UTC
Last modified on: 08/26/2022 17:35:00 UTC