The libtiff library as used in PivotX is not vulnerable. libtiff is used in various image processing programs, e.g. IrfanView, XnView, Adobe Photoshop, GIMP, etc. All users that use libtiff should upgrade as soon as possible. For those that cannot upgrade libtiff on time, there is a work around.
END Mozilla developers have identified a critical vulnerability in the libtiff library. This vulnerability could allow an attacker to cause Denial of Service of an application that uses libtiff.
For more information on this vulnerability, Andrew Brown has created a detailed advisory.
Vulnerability Details
A vulnerability has been identified in the libtiff library that allows an attacker to cause Denial of Service of an application that uses libtiff by sending a specially crafted packet.
Denial of Service is when software is unable to handle a high amount of activity, resulting in the system crashing. This could occur if an attacker sent packets with a lot of data to an application that uses libtiff.
PivotX Vulnerability Type and Scope
The vulnerability is classified as a local privilege escalation issue. On a system with the vulnerable version of libtiff, an attacker could exploit the vulnerability by causing Denial of Service of an application that uses libtiff.
How to determine if your application is affected by this vulnerability?
If you are using the libtiff library, you will need to determine if your application is affected by this vulnerability. For those that cannot upgrade, there is a work around for the vulnerability.
1) Download and run "libtiff_check-CVE-2022-0561.exe". This will check if your application uses libtiff, and if so, it will let you know if it's vulnerable or not.
2) If your application is vulnerable to CVE-2022-0561, there is a workaround available for the vulnerability. For more information on how to apply this workaround please refer to Andrew Brown's advisory
3) If your application does not use libtiff but has code in which a third party calls into libtiff, then your application may be vulnerable as well. In which case you should also read Andrew Brown's advisory to see what steps can be taken in order to mitigate against this issue
How to check if your software is using libtiff and how to mitigate the vulnerability
If you are using software that uses libtiff, you should check if your software is vulnerable. You can check by looking for a warning in your software's logs. If you do not see this warning, then your software is not at risk of being exploited by this vulnerability.
If you cannot upgrade your software on time, there is a work around.
To mitigate the vulnerability, use this command:
find "$(readlink -e \"/usr/lib/libtiff.so\")" | grep "not vulnerable" | grep "CVE-2022-0561"
END This will return a list of all files in "/usr/lib/libtiff.so". The vulnerability mentioned above has been fixed in these files, so they will be marked with "not vulnerable" as an indicator that the file has been fixed.
Execute Arbitrary Code By Manipulating Image Stream s
Libtiff is used in various image processing programs and could be exploited by an attacker to execute arbitrary code. The vulnerability is located in the TIFFFetch() function which is available on Windows, Linux, and Mac OS X.
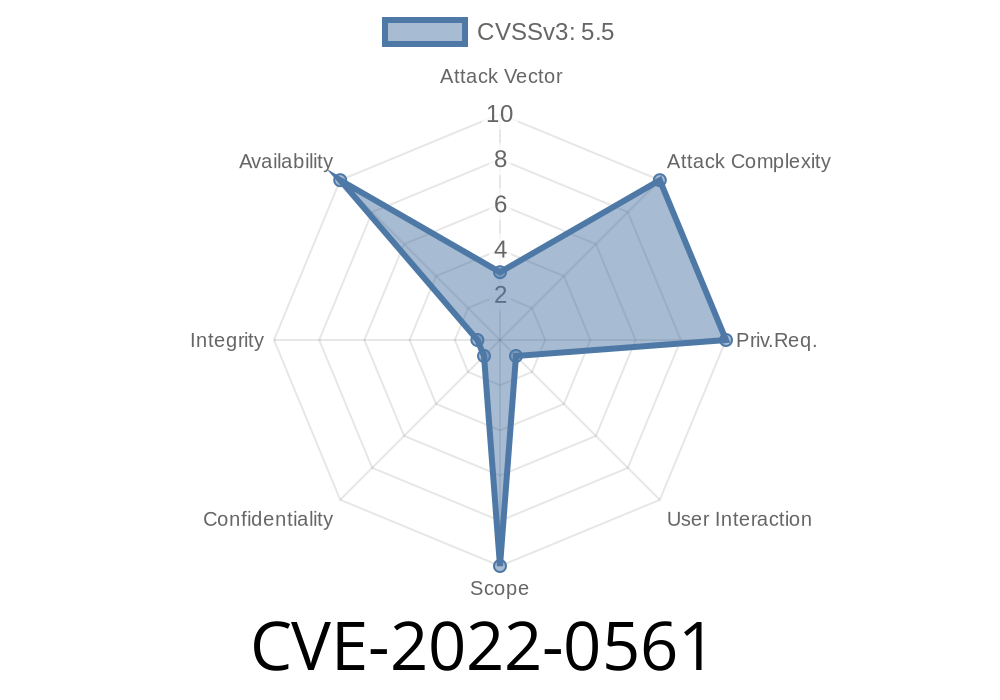
This vulnerability has been assigned CVE-2022-0561.
Timeline
Published on: 02/11/2022 18:15:00 UTC
Last modified on: 03/31/2022 18:16:00 UTC
References
- https://gitlab.com/freedesktop-sdk/mirrors/gitlab/libtiff/libtiff/-/commit/eecb0712f4c3a5b449f70c57988260a667ddbdef
- https://gitlab.com/libtiff/libtiff/-/issues/362
- https://gitlab.com/gitlab-org/cves/-/blob/master/2022/CVE-2022-0561.json
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/DZEHZ35XVO2VBZ4HHCMM6J6TQIDSBQOM/
- https://lists.debian.org/debian-lts-announce/2022/03/msg00001.html
- https://security.netapp.com/advisory/ntap-20220318-0001/
- https://www.debian.org/security/2022/dsa-5108
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0561