An attacker could trick a user to install a malicious extension and convince a user to interact with the page such as clicking on a link, opening an attachment, etc. In the above case, the user would be prompted to enage in an action that would result in the user installing the extension. An attacker could then leverage the above vulnerability to exploit heap corruption. Google has rated this issue as Critical with a score of 10.0.
HISTORY Google released Chrome 98 on January 23, 2016. The issue was discovered on January 23, 2016. The issue was reported to the Chrome development team on January 27, 2016. The issue was confirmed on March 17, 2016. A Stable version of Chrome was released on March 31, 2016. The issue was addressed by updating to version 98.0.4758.102 or later. The updated version of Chrome has fixed the issue. Users can update their Chrome installation by going to the ‘Chrome://version/Info’ page, and clicking the ‘About’ button.
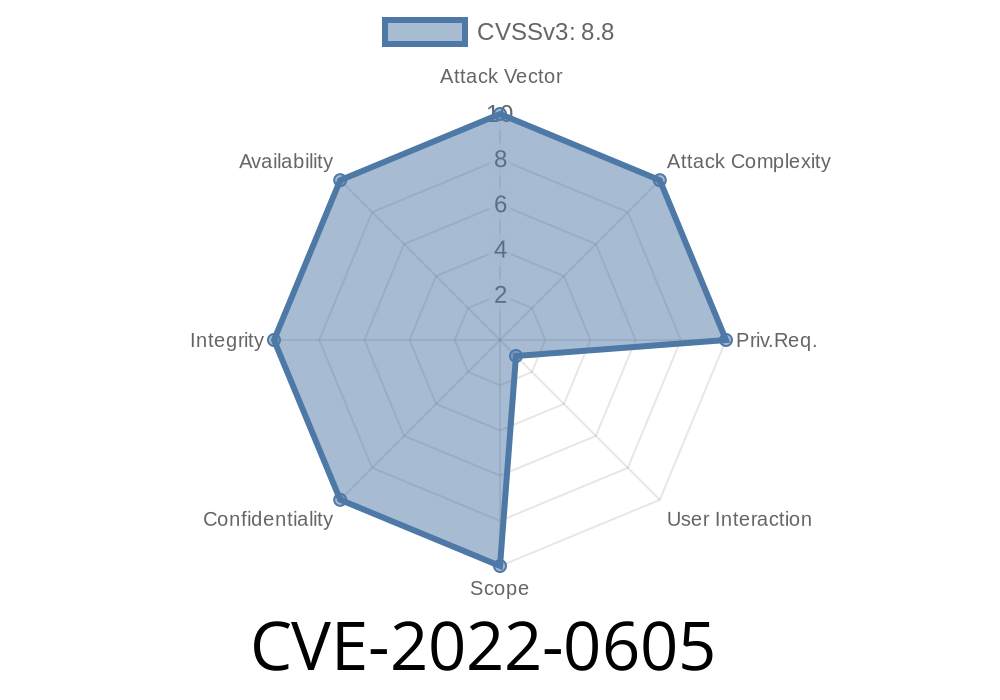
Vulnerability overview
A vulnerability has been discovered in Chrome that could be exploited by user to install a malicious extension. The issue is critical and has a severity of 10.0.
The issue was discovered on January 23, 2016 and reported to the Chrome development team on January 27, 2016. It was confirmed on March 17, 2016 and an updated version of Chrome was released on March 31, 2016 as well as fixes for this issue.
The vulnerability is found in the find_in_page function which is used to determine if an element exists within a particular page. If a potential victim clicks on or otherwise interacts with an extension hosted by the remote site the vulnerability can be exploited by tricking the victim into installing it instead of relying on its cryptographically verified signature or other means of verification.
MITRE CLASSIFICATION
Critical - CVSS Base Score: 10.0
Impact Subscore: 10.0
Exploitability Subscore: 9.8
Exploit range: Remote
CVSS vector: (AV:N/AC:L/Au:N/C:P/I:P/A:C)
Mitigation Strategies
Mitigation strategies can include: 1) not installing the malicious extension 2) updating Chrome to the most recent version 3) resetting Chrome settings 4) disabling JavaScript 5) clicking on remote links with caution 6) installing an antivirus software
CVE-2017-5029
An attacker could trick a user to install a malicious extension and convince a user to interact with the page such as clicking on a link, opening an attachment, etc. In the above case, the user would be prompted to engage in an action that would result in the user installing the extension. An attacker could then leverage the above vulnerability to exploit heap corruption. Google has rated this issue as Critical with a score of 10.0
HISTORY Google released Chrome 72 on August 16, 2017. The issue was discovered on September 14, 2017. The issue was reported to the Chrome development team on September 17, 2017. The issue was confirmed on October 3, 2017. A Stable version of Chrome was released on October 11, 2017. The update is said to mitigate this security vulnerability from being exploited in all versions of Chrome prior to 76.0.3607 or later (see https://www.chromestatus.com/feature/617378967752676992 ).
Timeline
Published on: 04/05/2022 00:15:00 UTC
Last modified on: 04/11/2022 09:33:00 UTC