This can lead to a Denial of Service condition if your server is accepting IPv4 or IPv6 queries, but is only responding with an IPv4 address for example. This is because the assertion that reads “An internal error has been detected and the system is being shut down” will eventually be hit. This happens because the named process periodically checks the DS records in the DNS query response to make sure that the IP address is in the expected range. When the assertion fails, named will print a message to the error log, then exit with code 5, which can be viewed in the dmesg command line utility or by issuing kill `cat `named.debug` A workaround for this issue is to update to BIND 9.17 or later, which fixes the vulnerability.
BIND 9.x and 10.x DNS server security vulnerabilities
A number of vulnerabilities in BIND 9.x and 10.x have been identified that could allow an attacker to cause a Denial of Service condition, or have other negative impacts on the system. The attacker must be able to send a specially crafted query to trigger these vulnerabilities.
The vulnerability is triggered by sending a DNS response with the following signature:
This signature is present in queries from the resolver component that attempts to check whether an error has been detected while resolving an IP address, but this signature should not be sent. BIND 9.x and 10.x versions prior to 9.17 are vulnerable, but after 9.17, these vulnerabilities can't be exploited using this signature because it was removed from DNS responses because it's unnecessary to protect against similar attacks like CVE-2020-0647 (the "TCP preconnect" attack).
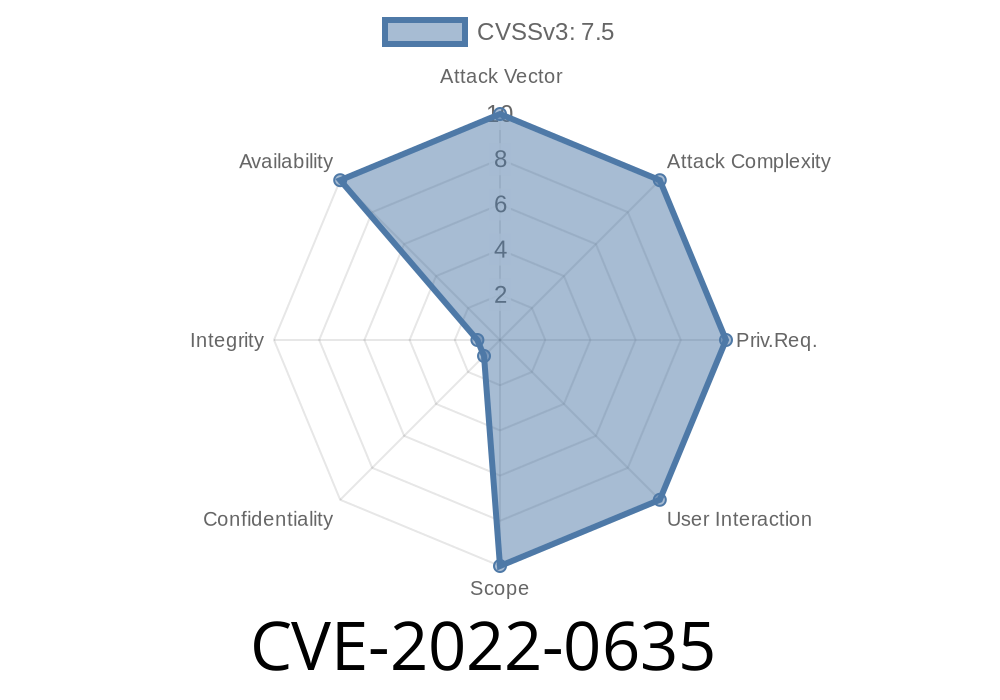
BIND Denial of Service Vulnerability – CVE-2022 -0635
A Denial of Service vulnerability was found in BIND, where the named process periodically checks the DS records in the DNS query response to make sure that the IP address is in the expected range. When the assertion fails, named will print a message to the error log, then exit with code 5, which can be viewed in the dmesg command line utility or by issuing kill `cat `named.debug` . A workaround for this issue is to update to BIND 9.17 or later, which fixes the vulnerability.
BIND Denial of Service Vulnerability – CVE-2022-0637
If you are using BIND 9.x, and your server process is running on an IPv6 address, it will periodically query the DNS server for the DS records to make sure that the IP address is in the expected range. When this query fails, BIND will print a message to the error log, then exit with code 5, which can be viewed in the dmesg command line utility or by issuing kill `cat `named.debug`
A workaround for this issue is to update to BIND 9.17 or later, which fixes the vulnerability.
Monitoring and Auditing DNS Servers
DNS servers are often the target of DDoS attacks, and it is important for administrators to regularly monitor their DNS infrastructure for anomalous activities.
BIND Doesn’t Sanitize the Time in a Zone
BIND 9.x does not sanitize the time zone when creating a new zone. This means that if you create a zone for Amsterdam, it will only have local timezone information, and will not have any of the timezone information from other zones. If you are using BIND as your primary DNS server, this can result in issues where clients cannot resolve names correctly even though they appear to be getting responses from both servers. If you are using a secondary server that is not BIND, then this issue will not affect your operation.
Timeline
Published on: 03/23/2022 12:15:00 UTC
Last modified on: 06/01/2022 19:50:00 UTC