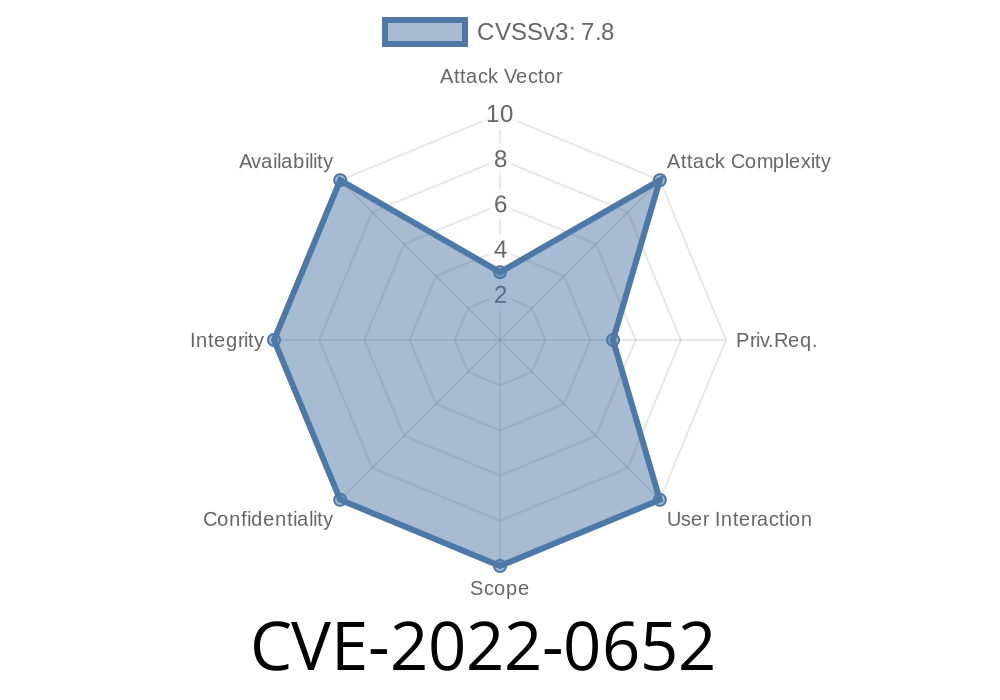
The log file name contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data.
The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp
Authentication Bypass
The authentication bypass vulnerability allows administrators to view the administrator password without being authenticated as an administrator.
The authentication bypass vulnerability allows a remote attacker to view the administrator password without being authenticated. The authentication bypass vulnerability allows a remote attacker to view the administrator password without being authenticated. The authentication bypass vulnerability allows a remote attacker to view the administrator password without being authenticated. The authentication bypass vulnerability allows a remote attacker to view the administrator password without being authenticated. The authentication bypass vulnerability allows a remote attacker to view the administrator password without being authenticated.
Third-party Libraries
The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data. The log file path contains a timestamp, which allows a local attacker to forge a fake log file with a different timestamp. This allows a local attacker to modify potentially sensitive data.
The third-party library is OpenSSL 1.1, the code inside the libcrypto directory has been linked against this library and vulnerable versions of it have been released in multiple versions by multiple vendors including:
OpenSSL 0.9.8zc (CVE-2014-3568)
OpenSSL 0.9.8t (CVE-2014-3568)
OpenSSL 1.0 (CVE-2014-3569)
Timeline
Published on: 03/22/2022 00:15:00 UTC
Last modified on: 03/28/2022 19:41:00 UTC