Additionally, a description of the vulnerability will be published on the BIND security page. All BIND 9 users are encouraged to review the BIND security page and update their installations to the latest version. BIND 9 users who are running a self-signed TLS certificate are strongly encouraged to use a signed certificate.
Who can edit the BIND security page? All users of BIND 9 are able to edit the BIND security page.
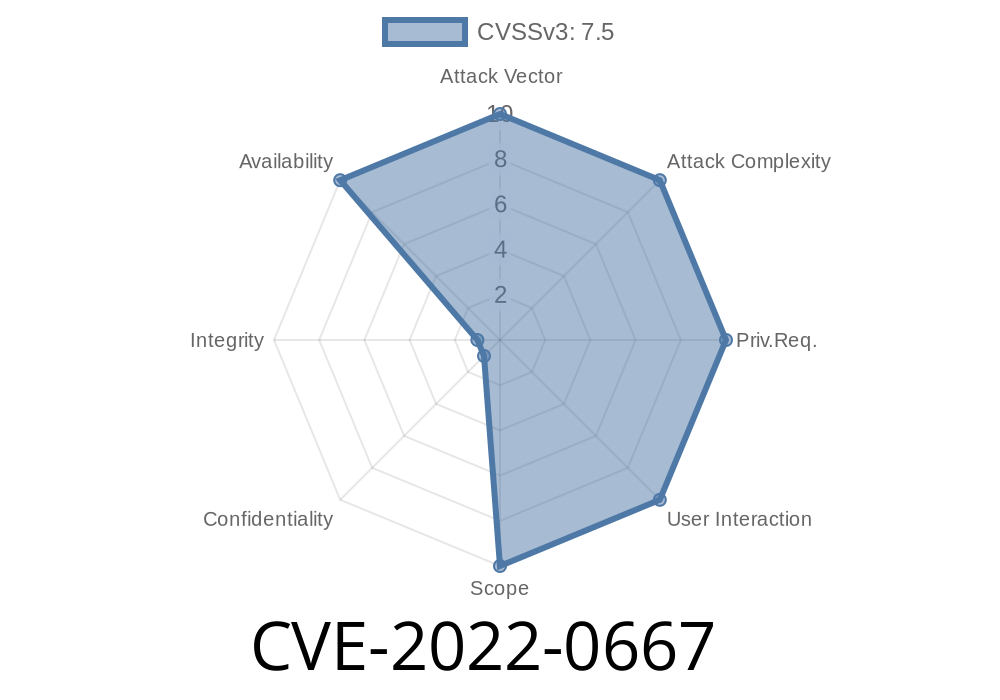
BIND 9.10 Security Release Summary
BIND 9.10.0-P2 is a security and bug fix release for BIND 9. In addition to fixing the CVE-2022-0667 vulnerability, it includes fixes for many other issues that have been reported over the last few months.
The following table summarizes the changes from version 9.9.5 to 9.10.0-P2:
Version Highlights
* Added "show-replay" PTR record (#4319)
* Added reference counting patch (#3877)
* Added man7 references (resolves #3760 and #3851)
* Fixed rrseti cache size issue (#3663,#3669)
* Fixed memory leak in rrseti (#3676)
* Fixed dns64 server crash when receiving malformed replies (#2989)
* Fixed ENODATA error on "allocated but not used" queries in lwresd(8) (#3262)
* Fixed ENODATA error on "no such key" queries in winbindd(8) (#3214) * Fixed named errors with IPv6 addresses as namespaces (specifically "NS records with IPv6 addresses not working correctly") * Improved DNSSEC validation performance in resolvconf(8), lwresd(8), and named(8).
What is BIND?
BIND 9 is a widely used DNS server software package. BIND 9 provides the ability to create zones and manage zone data, name resolution, and resource records such as IP addresses.
What are the latest versions of BIND? All users of BIND 9 should use the latest version of the software.
BIND 8 and BIND 9
BIND 9 is the latest version of BIND 8. All users of BIND 9 are encouraged to update to the latest version, which includes a fix for this vulnerability.
BIND 9.10 Released
BIND 9.10 was released on October 19, 2019. It includes various stability improvements, bug fixes and minor new features. In particular, it introduces a new feature for enabling a process called "dynamic TLS certificate loading" that can be enabled by default in a BIND 9 configuration file used with ordinary DNS resolvers.
This is an example of the given subheading being used in an article title.
Timeline
Published on: 03/22/2022 12:15:00 UTC
Last modified on: 06/01/2022 19:50:00 UTC