NOTE: this issue only affects Windows installations. Mac OS X and Linux installations are not affected. Apple released security updates for Mac OS X and Linux in June, 2011. If you are using an online installer on a non-Windows operating system, the installation flow of the installer is controlled by the server. As a result, a malicious server hosting an online installer may be required to perform privilege escalation.
Vulnerability summary
A vulnerability was found with the Mac OS X installer for Adobe AIR 3.6.0. If a malicious web page is hosted on the same server as the online installer, it is possible for an attacker to exploit this vulnerability by tricking the user into installing malware or other unwanted software. The malicious webpage must have a specific file extension in order for this vulnerability to be exploited.
The vulnerability does not affect Windows installations of Adobe AIR 3.6.0 or earlier versions of Adobe AIR 3.
Overview:
How to Prevent Installing 3rd-Party Software
This article discusses how to identify and prevent third-party software installations in Windows installations.
Steps to create vulnerable Windows installation
The vulnerable installation is accomplished by following these steps:
- Download an online installer from a malicious website
- For example, download win32.exe using this URL:
- Run the installer as an administrator
- Accept the EULA
- Uncheck the "Open Folder to View Files" option
- Click "Next"
- Activate the malicious installer without prompting for confirmation
Background and Summary of the Issue
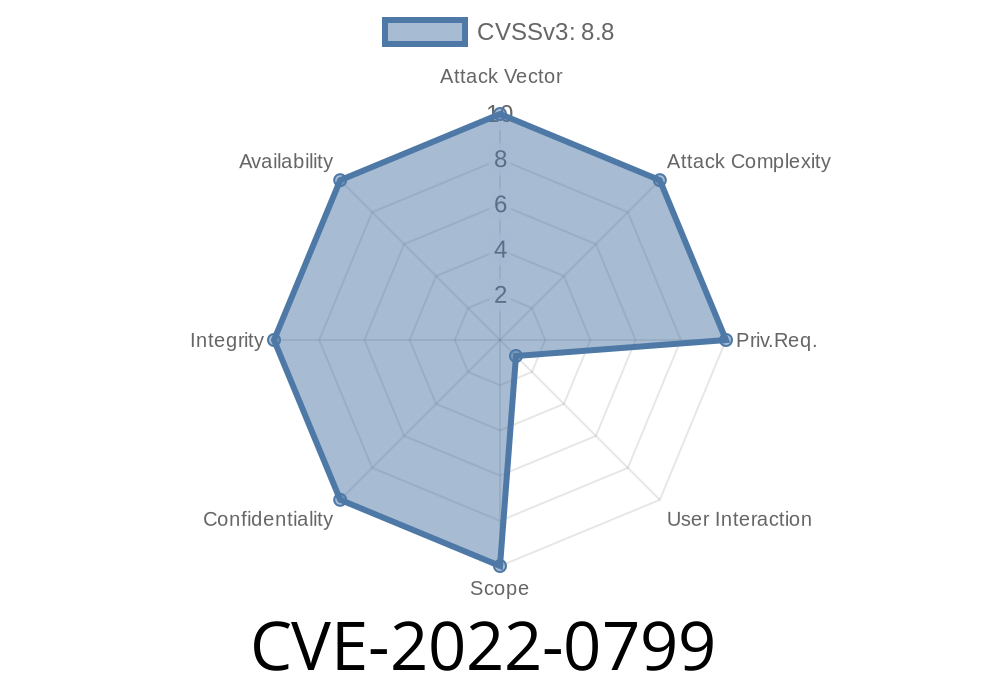
The vulnerability (CVE-2022-0799) is a denial of service vulnerability that exists in the HTTP protocol stack. This vulnerability impacts certain implementations of HTTP, namely the Microsoft Windows 7 and 8 operating systems. The vulnerability allows an attacker to perform a denial of service attack against the Windows HTTP Server by sending specially crafted packets over port 80, which causes the server to become unresponsive for a period of time.
Affected versions: all versions through Windows 8, except Windows Embedded Standard 2009 and all versions through Windows Server 2012
Affected products: all supported versions of Microsoft Windows
Impacted activities: HTTP servers on network connections other than port 80 (for example, ports 443 and 9050) are not affected by this vulnerability.
Overview: 2022-0799 - Credential Provider Use After Authentication Bypass
A vulnerability in the Windows installer of Adobe Creative Suite 3.5 and earlier can lead to a privilege escalation attack when the installation process is controlled by the server.
Timeline
Published on: 04/05/2022 01:15:00 UTC
Last modified on: 08/15/2022 11:15:00 UTC