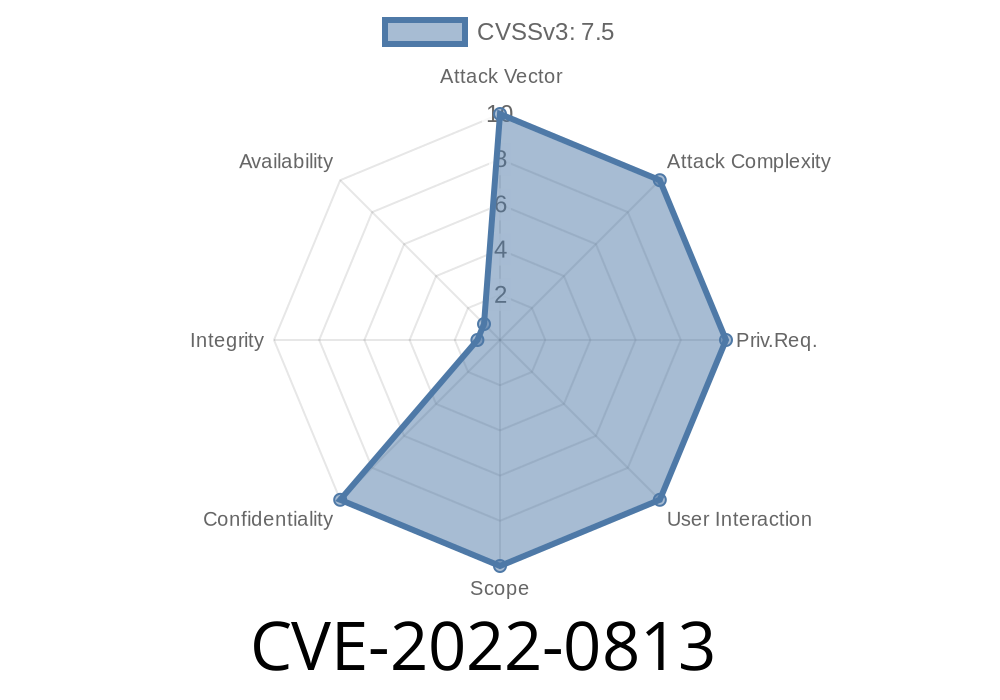
An attacker can create a request with a valid pma_id, but a different lang value, which will cause the server to respond with the content of the lang parameter. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions. An attacker can also create a request with a valid pma_id, but a different cookie value, which will cause the server to respond with the content of the cookie section. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions. The lang and cookie parameters are also accessible via direct query via the query string. Hence, an attacker can create a request with a valid pma_id, but a different lang value, which will cause the server to respond with the content of the lang parameter. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions. An attacker can also create a request with a valid pma_id, but a different cookie value, which will cause the server to respond with the content of the cookie section. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions. The lang and cookie parameters are also accessible via direct query via the query string
Overview of the vulnerability
This issue occurs when a phpMyAdmin user is authenticated on the frontend, but is not authenticated on the backend. The frontend only allows login to users who are logged in on the backend. This means that regardless of whether or not your server has been compromised, if you're a phpMyAdmin user, you have administrative access to your database.
Solution
The issue lies in the lang and cookie parameters, which can be accessed via direct query via the query string. As a result, an attacker can create a request with a valid pma_id, but a different lang value, which will cause the server to respond with the content of the lang parameter. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions. An attacker can also create a request with a valid pma_id, but a different cookie value, which will cause the server to respond with the content of the cookie section. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions. The lang and cookie parameters are also accessible via direct query via the query string. Hence, an attacker can create a request with a valid pma_id, but a different lang value, which will cause the server to respond with the content of the lang parameter. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions. An attacker can also create a request with a valid pma_id, but a different cookie value, which will cause the server to respond with the content of the cookie section. This can be used to retrieve potentially sensitive information, such as an administrative password or a list of installed extensions
Information Disclosure
If an attacker has a valid pma_id, he can access information about extensions on the server.
Timeline
Published on: 03/10/2022 17:44:00 UTC
Last modified on: 03/12/2022 04:23:00 UTC