Due to the nature of this issue - a stack buffer overflow - it could happen due to the following scenarios:
Incorrect input validation.
Redeploying the application.
TIFF image files with invalid header information.
Stack buffer overflow can happen due to the following reasons and scenarios:
Redeploying the application.
Incorrect input validation.
Upgrading software components.
Stack buffer overflow due to improper validation of input data could happen due to the following scenarios and circumstances:
Incorrect input validation.
Redeploying the application.
Upgrading software components.
Redeployment scenario could happen due to the following circumstances:
Redeploying the application.
Incorrect input validation.
Upgrading software components.
Incorrect input validation could happen due to the following reasons and circumstances:
Incorrect input validation.
Upgrading software components.
Attackers can exploit this issue to execute arbitrary code on the affected system.
Existing mitigations for this issue would not be effective in view of the fact that the issue itself is a stack buffer overflow.
Mitigation for this issue is to avoid using libtiff library and to avoid TIFF image files when possible.
Libtiff library is a large and complex software with various dependencies that are updated frequently. As a result, it’s difficult to know if an image
Table of Contents
1. Introduction
2. Description of Issue
3. Impact
4. Workarounds
5. Mitigation
6. Conclusion
What to do if you are using Libtiff library?
If you are using libtiff library and vulnerable to CVE-2022-0891, the following steps should be taken in order to mitigate the risk:
Install latest updates of the affected software components.
Disable features of the affected software components when they are not needed.
Protect against attackers by properly validating input data before using it.
It is recommended to modify existing applications or create new code that does not use libtiff library and does not rely on TIFF image files with invalid header information.
Timeline
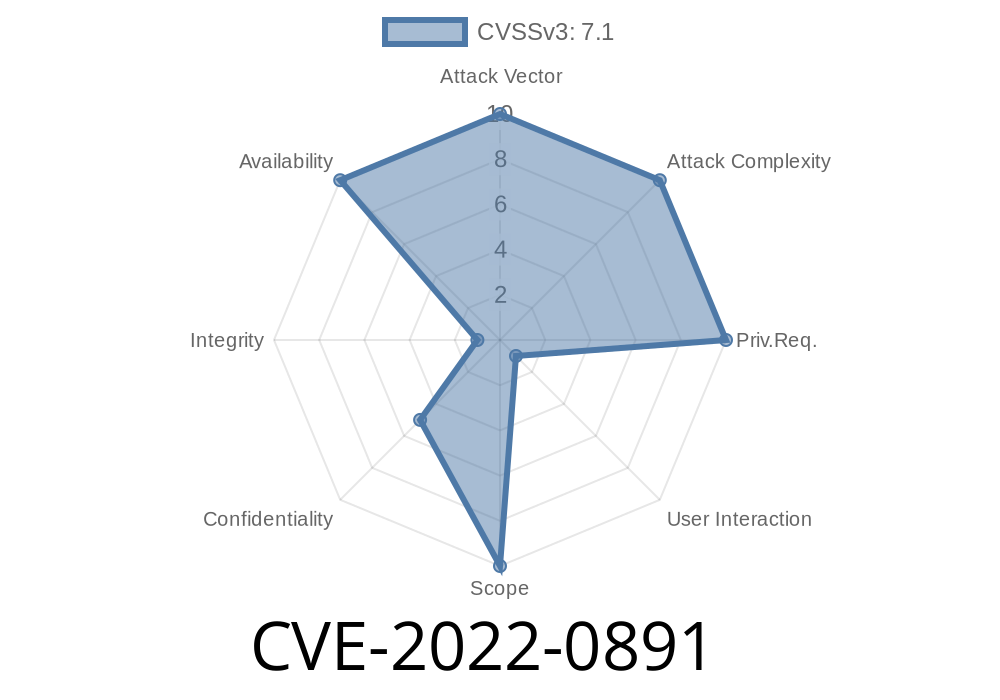
Published on: 03/10/2022 17:44:00 UTC
Last modified on: 04/18/2022 18:49:00 UTC
References
- https://gitlab.com/gitlab-org/cves/-/blob/master/2022/CVE-2022-0891.json
- https://gitlab.com/freedesktop-sdk/mirrors/gitlab/libtiff/libtiff/-/commit/232282fd8f9c21eefe8d2d2b96cdbbb172fe7b7c
- https://gitlab.com/libtiff/libtiff/-/issues/382
- https://gitlab.com/libtiff/libtiff/-/issues/380
- https://www.debian.org/security/2022/dsa-5108
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ZQ4E654ZYUUUQNBKYQFXNK2CV3CPWTM2/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/RNT2GFNRLOMKJ5KXM6JIHKBNBFDVZPD3/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0891