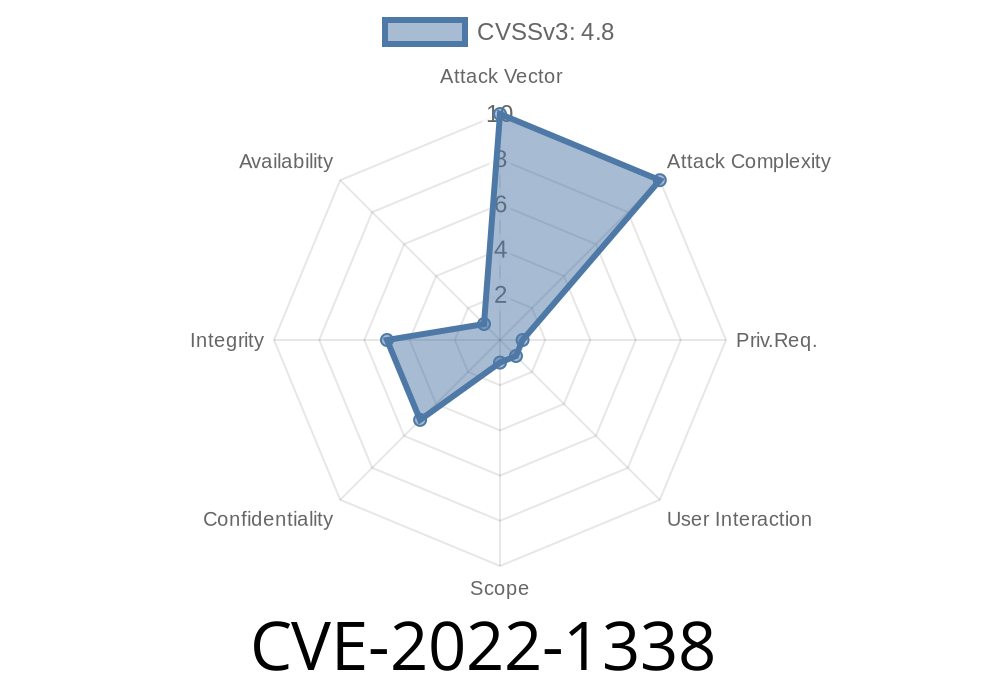
When creating a new REST API, the plugin allows for the setting of the allowed_origins capability, which if left empty defaults to the setting for the site’s parent. If the parent is a high privilege site, then an attacker can inject malicious code via XSS into the REST API settings. This can allow for a number of consequences, such as reading or writing to the settings of another site or adding a high privilege user to a WordPress team. When creating a new REST API, the plugin allows for the setting of the setting, which if left empty defaults to the setting for the site’s parent. If the parent is a high privilege site, then an attacker can inject malicious code via XSS into the REST API settings. This can allow for a number of consequences, such as reading or writing to the settings of another site or adding a high privilege user to a WordPress team. When creating a new REST API, the plugin allows for the setting of the allowed_origins capability, which if left empty defaults to the setting for the site’s parent. If the parent is a high privilege site, then an attacker can inject malicious code via XSS into the REST API settings. This can allow for a number of consequences, such as reading or writing to the settings of another site or adding a high privilege user to a WordPress team. When creating a new REST API, the plugin allows for the setting of the allowed_origins capability, which if left empty
Account Management
An attacker could access the site’s account settings to change passwords, add new users, or modify existing user data such as email addresses and usernames. This may allow for access to the WordPress database, post content, or edit other site meta-data. An attacker could access the site’s account settings to change passwords, add new users, or modify existing user data such as email addresses and usernames. This may allow for access to the WordPress database, post content, or edit other site meta-data. An attacker could access the site’s account settings to change passwords, add new users, or modify existing user data such as email addresses and usernames. This may allow for access to the WordPress database, post content, or edit other site meta-data.
Timeline
Published on: 05/09/2022 17:15:00 UTC
Last modified on: 05/16/2022 15:33:00 UTC