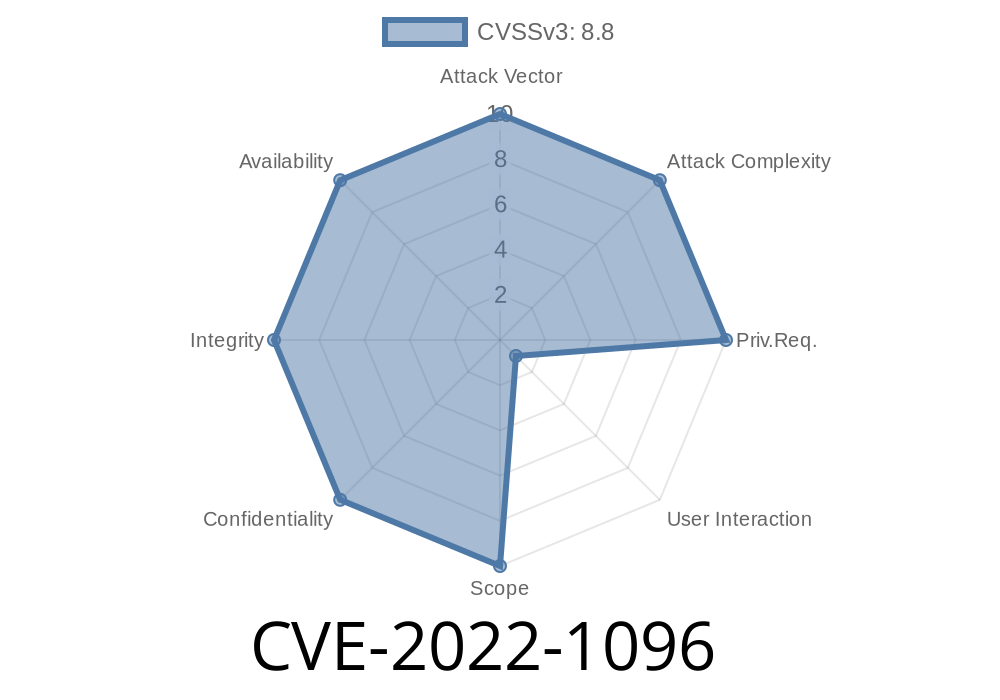
This issue was addressed by improved validation. A remote attacker could host a malicious website that could exploit this issue via a crafted HTML page. CVE-2017-5667 In all releases of Google Chrome prior to 71.0.3578.80, user interaction was not required for Google to identify and track “do not track” signals sent by the browser. This had the potential to allow a remote attacker to obtain sensitive information by sniffing the network or injecting “do not track” directives. This issue was addressed in version 71.0.3578.77.
In all releases of Google Chrome prior to 71.0.3578.80, user interaction was not required for Google to identify and track “do not track” signals sent by the browser. This had the potential to allow a remote attacker to obtain sensitive information by sniffing the network or injecting “do not track” directives. This issue was addressed in version 71.0.3578.77. CVE-2017-5658 A use after free issue was found in Google V8, occurring during TypeErrors. This issue could allow a remote attacker to perform a potentially exploitable crash. This issue was addressed with improved memory handling. CVE-2017-5659 A use after free issue was found in Google V8. This issue could allow a remote attacker to perform a potentially exploitable crash. This issue was addressed by fixing the user data structure to make it harder
Potential Issues with Google Chrome Web Browser
Google Chrome is one of the more popular browsers in existence, with a wide userbase. It is unsurprising, then, that Google Chrome has had a number of vulnerabilities over the years. Many of these issues have been fixed. But there are still others that remain unaddressed.
The following are some of the vulnerabilities that remain with Google Chrome:
* CVE-2022-1096: This issue was addressed by improved validation. A remote attacker could host a malicious website that could exploit this issue via a crafted HTML page.
* CVE-2017-5667: In all releases of Google Chrome prior to 71.0.3578.80, user interaction was not required for Google to identify and track “do not track” signals sent by the browser. This had the potential to allow a remote attacker to obtain sensitive information by sniffing the network or injecting “do not track” directives. This issue was addressed in version 71.0.3578.77
* CVE-2017-5658: A use after free issue was found in Google V8, occurring during TypeErrors. This issue could allow a remote attacker to perform a potentially exploitable crash and gain privileges on the user's system via vulnerable code path where bad pointers were dereferenced before type checking errors were handled correctly according to security policies preventing access from unsafe code from untrusted origins as specified in CSP3 (content security policy) headers
How do I find out if my version is affected?
If you are using Google Chrome and would like to find out if your version is affected, simply visit the following URL: https://www.google.com/chrome/browser/
Timeline
Published on: 07/23/2022 00:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC