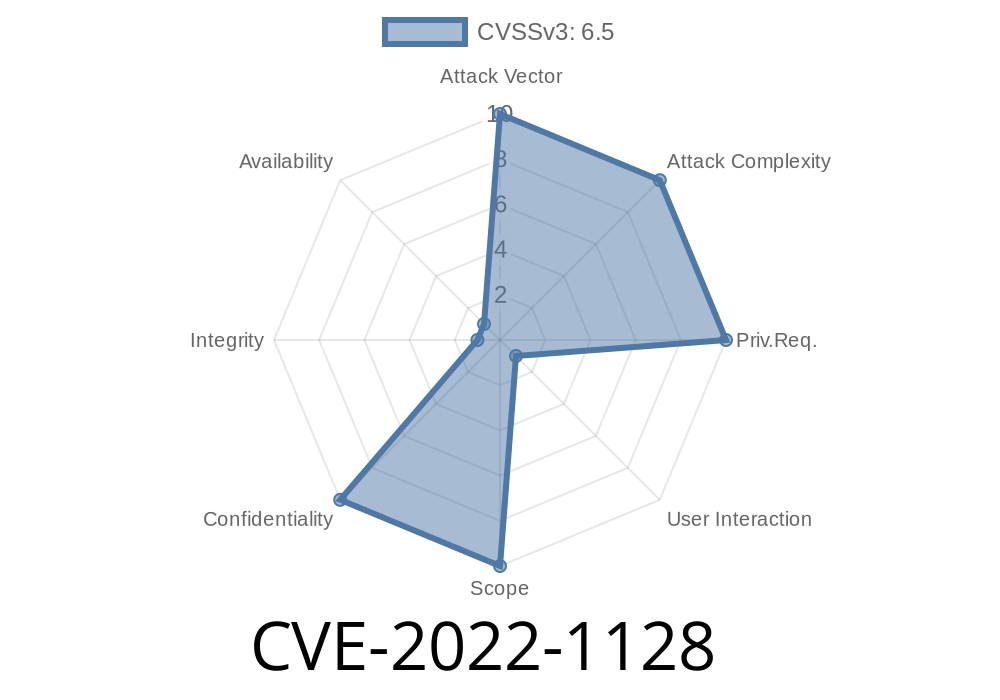
This issue was addressed by restricting data flow across origins. As a general security best practice, applications should avoid transmitting data across origins. This can be problematic if the data being transmitted is not sufficiently validated, has an origin that has been hardcoded, or is being sent across an insecure connection such as unencrypted HTTP. In these cases, an attacker could potentially exploit this behaviour to steal data. An application that needs to transmit data between origins must do so using a secure protocol, and through an encrypted origin.
Summary
This issue was addressed by restricting data flow across origins. As a general security best practice, applications should avoid transmitting data across origins. This can be problematic if the data being transmitted is not sufficiently validated, has an origin that has been hardcoded, or is being sent across an insecure connection such as unencrypted HTTP. In these cases, an attacker could potentially exploit this behaviour to steal data. An application that needs to transmit data between origins must do so using a secure protocol, and through an encrypted origin.
CVE-2022-1129
Multiple cross-site scripting vulnerabilities were found in the way OpenSSL handled DTLS messages during an SSL/TLS handshake. A remote attacker could possibly exploit these issues to execute arbitrary script code in a user's browser session.
Timeline
Published on: 07/23/2022 00:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC