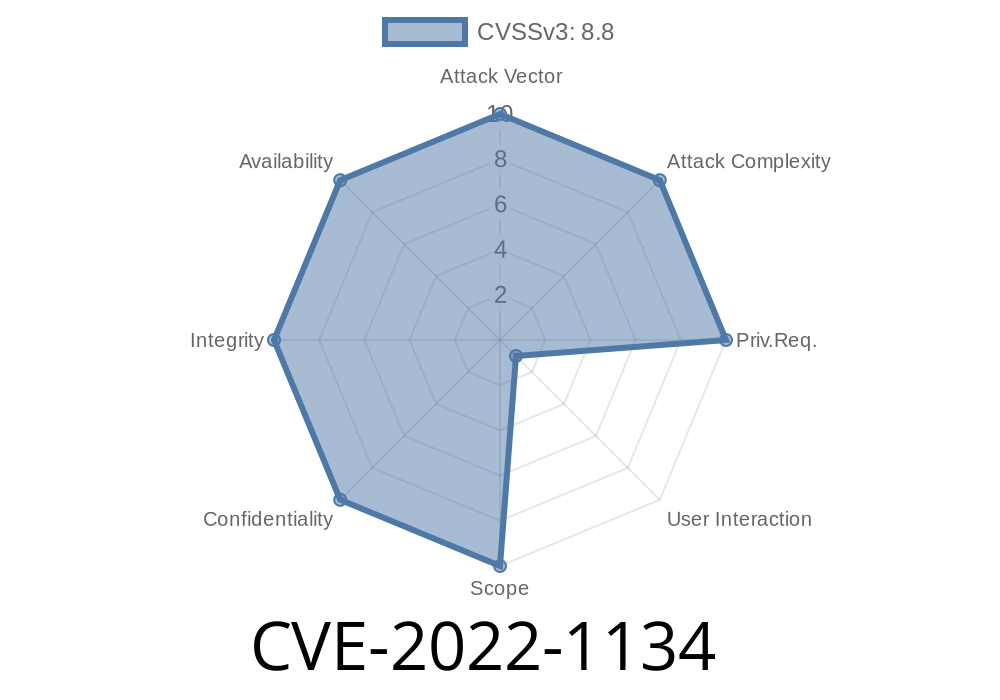
Google Chrome stands as one of the world’s most popular browsers, but even the toughest software has hidden weaknesses. In early 2022, security researchers uncovered a serious vulnerability in Chrome’s JavaScript engine, V8, officially labeled as CVE-2022-1134. In this blog post, we’ll break down what went wrong, how attackers could exploit it, and provide example code that highlights the danger.
Let’s get right to the heart of it—anyone running Chrome versions before 100..4896.60 was potentially at risk of attackers corrupting their browser's heap memory by luring them onto a malicious HTML page.
What is CVE-2022-1134?
CVE-2022-1134 is a type confusion bug in the V8 JavaScript engine. In programming, "type confusion" means the program treats a block of memory as being of a different type than it actually is. This kind of mistake can cause unpredictable behavior and is a common starting point for browser exploits.
The bug was present in the V8 engine before version 100..4896.60 of Chrome. To put it simply: an attacker could trick the engine into mixing up types, then use that confusion to overwrite critical memory areas (the heap). That, in turn, could allow them to run their own code on your device.
Official Background and References
- Chrome Release Blog – March 29, 2022 (Stable Channel Update)
- NVD – CVE-2022-1134
How Does Type Confusion Happen in V8?
In JavaScript, objects can be of different internal structures—sometimes, the engine gets confused and applies the wrong operations. Let’s walk through what that might look like conceptually.
Suppose there’s an internal function that expects an array of integers but, thanks to some programming tricks, ends up treating an array of objects as an array of integers. If you can control what’s in the array, you might trick the engine into overwriting data it shouldn’t.
Here’s a simplified JavaScript snippet inspired by type confusion bugs
function confuseTypes() {
let arr = [1.1, 2.2, 3.3]; // Array with doubles (floating-point numbers)
let objArr = [{}, {}, {}]; // Array with objects
arr.__proto__ = objArr.__proto__; // Force the arrays to share the same prototype
// Exploit attempt: Overwrite the elements kind information
arr[] = {}; // Placing an object into what’s supposed to be a float array
// If V8 loses track of the real type, memory corruption may occur here
// In real exploits, attackers fine-tune this to achieve arbitrary memory access
}
confuseTypes();
*Note: This code won’t crash a modern, patched browser, but it demonstrates the logic behind a type confusion vulnerability.*
Real Exploitation—What Does an Attacker Need?
With CVE-2022-1134, an attacker could embed code like the one above into a specially crafted web page. If a victim visits the page, the exploit attempts to force V8 into mismanaging object types, opening the door to heap corruption. In many real-world exploits, this is just the first step—attackers usually chain this with another bug (like leaking memory addresses) to fully take over the browser process.
Trigger the confusion: Carefully crafted JavaScript triggers the type confusion bug.
3. Gain memory control: By causing V8 to treat an object as a different type, attacker corrupts the heap.
Proof-of-Concept Reference
While Google and other security firms do not publish live, weaponized exploits, the Project Zero team’s blog covers similar type confusion bugs in V8, walking through the type-mixing and heap manipulation tricks attackers use.
Google quickly patched the bug in Chrome 100..4896.60. If you’re not sure you’re patched
1. Update Chrome: Click the three-dot menu, go to “Help” → “About Google Chrome,” and ensure you’re fully updated.
Conclusion
CVE-2022-1134 is a prime example of how deep, technical bugs in browser engines can be weaponized with something as innocent-looking as a web page. Type confusion vulnerabilities are tricky, but with careful patching and public awareness, you can stay one step ahead of attackers.
References
- https://chromereleases.googleblog.com/2022/03/stable-channel-update-for-desktop_29.html
- https://nvd.nist.gov/vuln/detail/CVE-2022-1134
- https://googleprojectzero.blogspot.com/2017/05/exploiting-type-confusion-in-v8.html
Timeline
Published on: 07/23/2022 00:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC