Cross-origin data leakage is a common issue in web applications where data from one origin is exposed to a script on another origin. Such data can be used by attackers to steal personal information, manipulate data, or launch a phishing attack. Background Fetch allows web applications to load remote resources asynchronously, such as images, stylesheets, or scripts that are loaded without blocking the main page content. Such background loading is enabled by default in Google Chrome on Windows, macOS, Linux, and Android. The Background Fetch specification defines three types of URIs that can be used for loading remote resources: http, https, and file. Google Chrome limits all URIs to be loaded via https, so file URIs can only be loaded by manually changing the type to file. https and file URIs are also limited to load remote resources from the same host, so adding cross-origin resources via https or file URIs is not possible. The Background Fetch specification does not define any limit for the size of the remote resource, but Google Chrome limits each remote resource to be no more than 1MB to reduce the memory consumption. For example, loading a remote image via https://myserver.com/image.jpg will be blocked by Google Chrome. Remote resources can instead be loaded via http://myserver.com/image.jpg to bypass the limit. Inappropriate implementation of Background FAPI in Google Chrome prior to 100.0.4896.60 allowed a remote attacker to
Vulnerability overview
A vulnerability was discovered in Google Chrome prior to 100.0.4896.60, where a remote attacker can use a file: URI to load remote resources from other origins than the origin of the current page via cross-origin content loading. Such cross-origin resources are loaded with higher privileges and can execute script code within the local context of the current domain. This allows an attacker to steal personal information or manipulate data, or launch a phishing attack. As such, no action is required by users beyond updating their software as soon as possible
Vulnerability summary
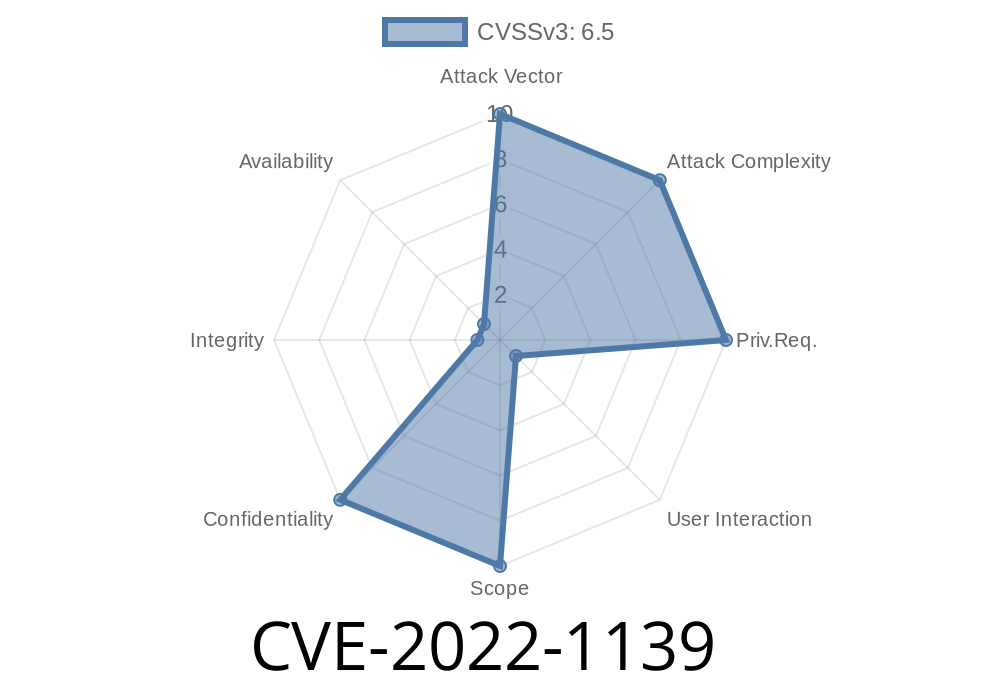
A remote attacker could exploit a vulnerability in Google Chrome prior to 100.0.4896.60 by loading cross-origin resources via an https or file URI.
The Background Fetch specification does not define any limit for the size of the remote resource, but Google Chrome limits each remote resource to be no more than 1MB to reduce the memory consumption.
For example, loading a remote image via https://myserver.com/image.jpg will be blocked by Google Chrome. Remote resources can instead be loaded via http://myserver.com/image.jpg to bypass the limit.
Description of CVE-2022-1139 Vulnerability
There is a vulnerability in the implementation of Background Fetch APIs. If there is a website that implements Background Fetch APIs, an attacker can perform Cross-origin data leakage by loading remote resources from different origins. This can be exploited to steal personal information such as SSN or credit card numbers.
Background FAPI: Cross-Origin Data Leakage in Google Chrome
Cross-origin data leakage is a common issue in web applications where data from one origin is exposed to a script on another origin. Such data can be used by attackers to steal personal information, manipulate data, or launch a phishing attack. Specifically, Cross-Origin Resource Sharing (CORS) allows scripts from one domain to have access to resources on another domain without having the resource sent to the client's browser first. The Background Fetch API (Background FAPI) provides cross-origin loading of remote resources like images and script files. Background FAPI was introduced in Google Chrome version 100.0.4896.60 but was not fully implemented because of an implementation error in Google Chrome version prior to 100.0.4896.60 that allowed a remote attacker to inject arbitrary HTML into the page via cross-origin loading of remote script files.
Vulnerability
Cross-origin data leakage is a common issue in web applications where data from one origin is exposed to a script on another origin. Such data can be used by attackers to steal personal information, manipulate data, or launch a phishing attack. Background Fetch allows web applications to load remote resources asynchronously, such as images, stylesheets, or scripts that are loaded without blocking the main page content. Such background loading is enabled by default in Google Chrome on Windows, macOS, Linux, and Android. The Background Fetch specification defines three types of URIs that can be used for loading remote resources: http, https, and file. Google Chrome limits all URIs to be loaded via https, so file URIs can only be loaded by manually changing the type to file. https and file URIs are also limited to load remote resources from the same host, so adding cross-origin resources via https or file URIs is not possible. The Background Fetch specification does not define any limit for the size of the remote resource, but Google Chrome limits each remote resource to be no more than 1MB to reduce the memory consumption. For example, loading a remote image via https://myserver.com/image.jpg will be blocked by Google Chrome. Remote resources can instead be loaded via http://myserver.com/image.jpg to bypass the limit.>>END>>
The importance of digital marketing is often overlooked because most people think it's just promoting your business through social
Timeline
Published on: 07/23/2022 00:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC