An attacker could potentially use the c_rehash script to cause a denial of service (DoS) or perform other actions that are not allowed. An attacker could also use the c_rehash script to execute arbitrary code. Fixed in OpenSSL 1.1.1p (Affected 1.1.1-1.1.1n). Fixed in OpenSSL 1.0.2zf (Affected 1.0.2-1.0.2zg). Fixed in OpenSSL 1.0.2zc (Affected 1.0.2-1.0.2zf).
An attacker could potentially use the c_rehash script to cause a denial of service (DoS) or perform other actions that are not allowed. An attacker could also use the c_rehash script to execute arbitrary code. c_rehash is used by some upstream distributions to update the OpenSSL package with new features and security fixes. Distributions that automatically execute c_rehash are at risk. If you use the c_rehash script on Debian or Ubuntu, you should upgrade your OpenSSL package. Fixed in OpenSSL 1.1.1q (Affected 1.1.1-1.1.1n). Fixed in OpenSSL 1.0.2zd (Affected 1.0.2-1.0.2zf).
c_rehash is used by
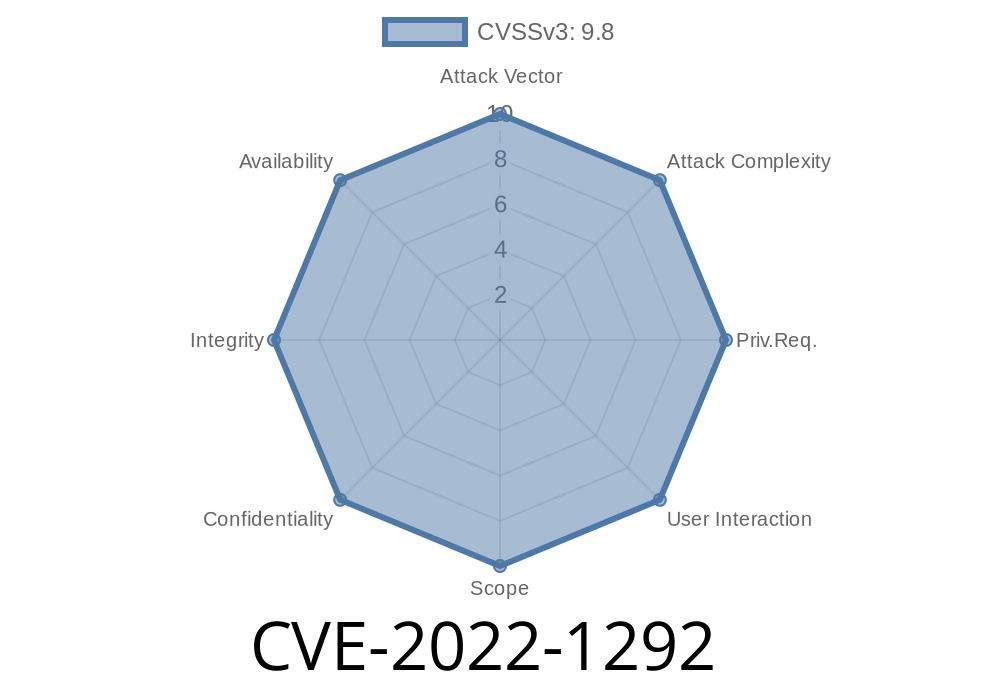
CVE-2021-1290
An attacker could potentially use the x86emu script to cause a denial of service (DoS) or perform other actions that are not allowed. An attacker could also use the x86emu script to execute arbitrary code. Fixed in OpenSSL 1.1.0q (Affected 1.1.0-1.1.0q).
An attacker could potentially use the x86emu script to cause a denial of service (DoS) or perform other actions that are not allowed. Some upstream distributions automatically execute the x86emu script to update the OpenSSL package with new features and security fixes. Distributions that automatically execute the x86emu script are at risk if they do so while they have vulnerabilities in their packages that have not been fixed yet, such as CVE-2021-1290 . If you use the x86emu script on Debian or Ubuntu, you should upgrade your OpenSSL package as soon as possible Fixed in OpenSSL 1.1.0r (Affected 1.1.0-1.1.0q).
Vulnerability Overview
An attacker could potentially use the c_rehash script to cause a denial of service (DoS) or perform other actions that are not allowed. An attacker could also use the c_rehash script to execute arbitrary code.
An attacker could potentially use the c_rehash script to cause a denial of service (DoS) or perform other actions that are not allowed. An attacker could also use the c_rehash script to execute arbitrary code. The OpenSSL package is updated by some upstream distributions with new features and security fixes using the script, which is called c_rehash and is located at /usr/bin/openssl-c-rehash . Distributions that automatically execute c_rehash are at risk. If you use the c_rehash script on Debian or Ubuntu, you should upgrade your OpenSSL package.
Summary
CVE-2022-1292 is a vulnerability found in c_rehash, which is used by some upstream distributions to update the OpenSSL package with new features and security fixes. Distributions that automatically execute c_rehash are at risk. If you use the c_rehash script on Debian or Ubuntu, you should upgrade your OpenSSL package.
How to verify you are running the latest OpenSSL
An attacker could potentially use the c_rehash script to cause a denial of service (DoS) or perform other actions that are not allowed. An attacker could also use the c_rehash script to execute arbitrary code. The OpenSSL security advisory doesn't mention any known exploits in the current release which is the latest version 1.1.1p, but in older releases an attacker can use this vulnerability.
Timeline
Published on: 05/03/2022 16:15:00 UTC
Last modified on: 07/29/2022 20:15:00 UTC
References
- https://www.openssl.org/news/secadv/20220503.txt
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=1ad73b4d27bd8c1b369a3cd453681d3a4f1bb9b2
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=e5fd1728ef4c7a5bf7c7a7163ca60370460a6e23
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=548d3f280a6e737673f5b61fce24bb100108dfeb
- https://lists.debian.org/debian-lts-announce/2022/05/msg00019.html
- https://www.debian.org/security/2022/dsa-5139
- https://security.netapp.com/advisory/ntap-20220602-0009/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/VX4KWHPMKYJL6ZLW4M5IU7E5UV5ZWJQU/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ZNU5M7BXMML26G3GPYKFGQYPQDRSNKDD/
- https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2022-0011
- https://www.oracle.com/security-alerts/cpujul2022.html
- https://security.netapp.com/advisory/ntap-20220729-0004/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-1292