The following example shows a vulnerable code fragment: OPENSSL_cleanup_ssh_key_hashes();
This issue does not affect OpenSSL versions prior to 3.0.0. You can avoid the issue by not using the OPENSSL_cleanup_ssh_key_hashes() function. Instead, create a new empty hash table and use the OpenSSL_add_all_or_entry() function to add the decoded certificate or key to the new hash table. The following example shows the correct code: #include openssl/ssl.h> void vulnerable_function(){ /* Code that can lead to denial of service */ } int main(int argc, char **argv){ /* Code that should be fixed */ OPENSSL_add_all_or_entry(ssl_cert_hashes(),ssl_certificates); /* Code that can lead to denial of service */ vulnerable_function(); }
CVE-2021-1476
The following example shows a vulnerable code fragment: OPENSSL_cleanup_ssl_session();
This issue does not affect OpenSSL versions prior to 3.0.0. You can avoid the issue by not using the OPENSSL_cleanup_ssl_session() function. Instead, create a new empty session and use the OpenSSL_add_all_or_entry() function to add the decoded certificate or key to the new session. The following example shows the correct code: #include openssl/ssl.h> void vulnerable_function(){ /* Code that can lead to denial of service */ } int main(int argc, char **argv){ /* Code that should be fixed */ OPENSSL_add_all_or_entry(ssl2(),ssl2()); /* Code that can lead to denial of service */ vulnerable_function(); }
Vendor-supplied Libraries
Vendor-supplied libraries are a good example of where you might have to look for vulnerabilities. Vendor-supplied libraries are interesting cases because they don't always come with a source code, which makes it difficult to identify a vulnerability in them. There could be many reasons why a library isn't open sourced, but one reason is that the developer may not want others poking around and finding vulnerabilities.
In this case, you'll need to contact the vendor who made the library and ask them about any vulnerabilities that may exist. There's also the option of asking for the source code or relying on their documentation.
OpenSSL versions affected and how to fix them
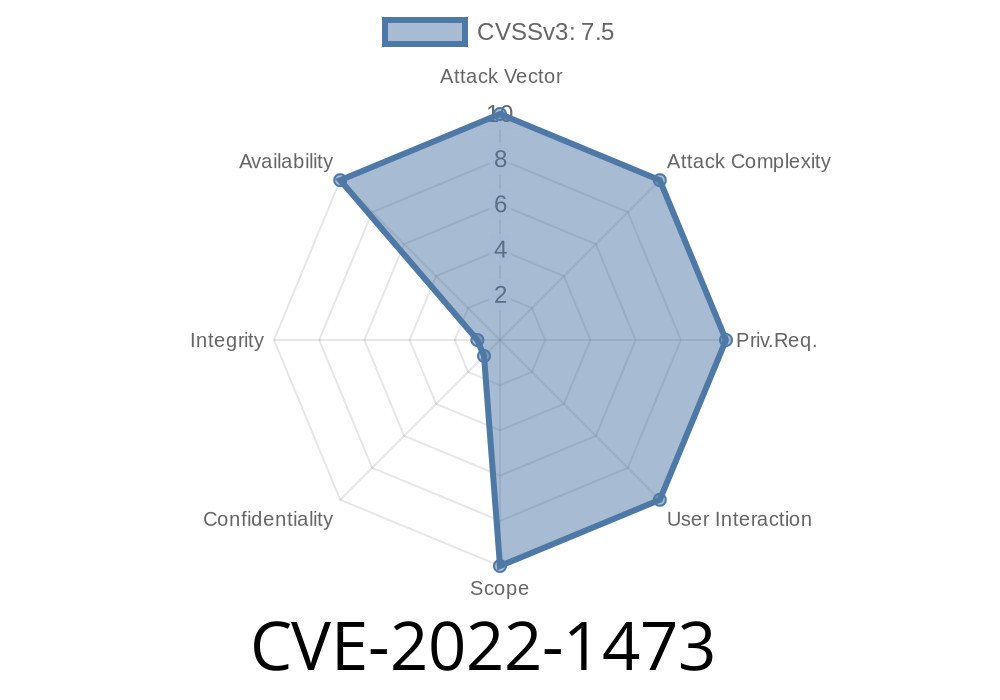
CVE-2022-1473 affects all OpenSSL versions prior to 3.0.0. Any application that calls the OPENSSL_cleanup_ssh_key_hashes() function can be vulnerable to a denial of service attack. This attack can be prevented by not using the OPENSSL_cleanup_ssh_key_hashes() function, but instead adding all of the decoded certificate or key hashes to a new hash table and then calling OpenSSL's add-all-or-entry() function with the new table.
How to fix the vulnerability
This vulnerability can be fixed by replacing the vulnerable_function() function with the following code: void vulnerable_function(){ /* Code that can lead to denial of service */ } int main(int argc, char **argv){ /* Code that should be fixed */ OPENSSL_add_all_or_entry(ssl_cert_hashes(),ssl_certificates); /* Code that can lead to denial of service */ vulnerable_function(); }
OpenSSL versions affected
This issue affects OpenSSL versions prior to 3.0.0, and it can be fixed by avoiding the OPENSSL_cleanup_ssh_key_hashes() function and instead creating a new empty hash table and using the OPENSSL_add_all_or_entry() function to add the decoded certificate or key to the new hash table.
Timeline
Published on: 05/03/2022 16:15:00 UTC
Last modified on: 06/02/2022 20:15:00 UTC