used. Due to the non-deterministic nature of IBM's implementation of the RC4-MD5 cipher, an attacker could potentially exploit this issue to generate traffic that appears as if it originates from any location, not just the location of the server. OpenSSL 3.0 is vulnerable to a variant of the BEAST attack. If a vulnerable OpenSSL server is serving a client using a protocol that is vulnerable to BEAST (such as HTTP) then an attacker could conceivably send a request to that server that takes advantage of the RC4-MD5 flaw as described above. The RC4-MD5 cipher is used by the Secure Remote Access Protocol (SRP) used in the administration of many medical devices. An attacker could conceivably send a request to a SRP server that takes advantage of the RC4-MD5 flaw as described above. Due to the sensitive nature of the data SRP servers receive, such an attack would likely require both the installation of a malicious device near the end device as well as physical access to the device itself. An attacker could also use the RC4-MD5 flaw to generate traffic to a vulnerable SSL/TLS server that accepts remote access clients. This could permit an attacker to launch a MITM attack and intercept data being sent to such a server. OpenSSL 3.0 is vulnerable to a variant of the Lucky Thirteen attack. If a vulnerable OpenSSL server is accepting SSL/TLS client connections then an attacker
Summary
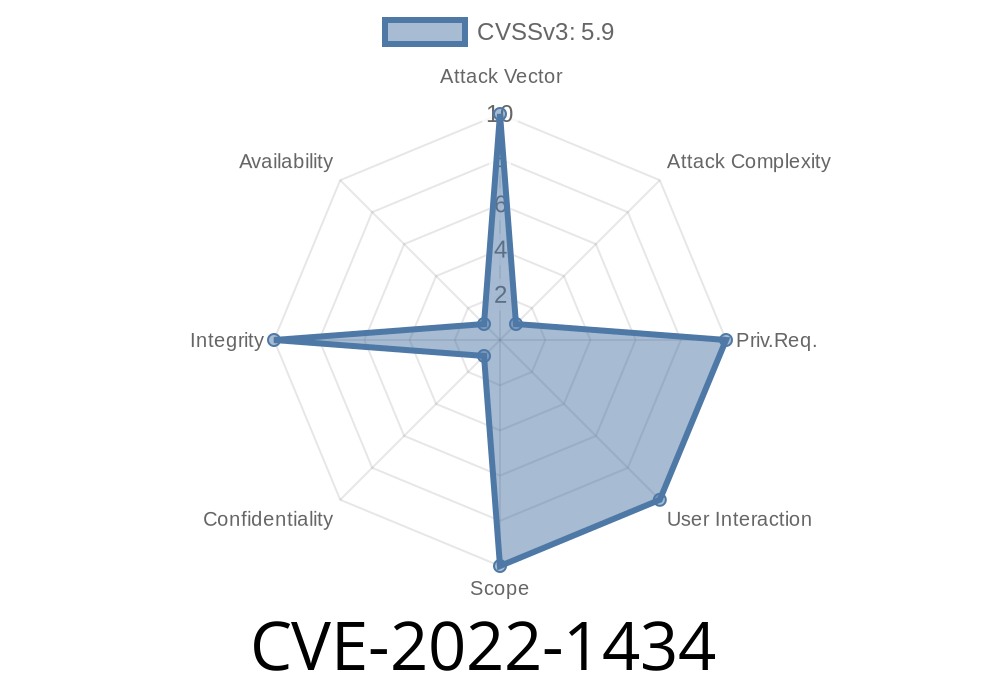
OpenSSL 3.0 is vulnerable to a variant of the Lucky Thirteen attack, which permits an attacker to launch a MITM attack and decrypt data sent over SSL/TLS.
Supported Oracle Solaris Versions
Oracle Solaris 11.1, 12.0, and above.
In order to mitigate vulnerabilities in OpenSSL, Oracle Solaris must be patched or upgraded to a supported version of the operating system and SSL/TLS libraries.
4.1 a rel=\"nofollow\" href=\"http://www-01.ibm.com/support/docview.wss?uid=swg2166990\" target=\"_blank\" style=\"display:none;\">http://www-01.ibm.com/support/docview.wss?uid=swg2166990
Timeline
Published on: 05/03/2022 16:15:00 UTC
Last modified on: 06/02/2022 20:15:00 UTC