This issue was fixed in version 100.0.4896.87. Redirect URI Insecure Redirects After March 17, 2017 security update, redirects in Google Chrome were updated to secure by default and invalidate instant responses to all origins by default. This change may affect the redirect URI of web pages. Memory corruption issues were observed when handling redirect URIs with web content. These issues were addressed by changing the URL sanitization rules for redirect URIs to secure by default. Exploitation of these issues with web content may result in remote code execution. Redirect URIs are now sanitized through the new URL sanitization rules before being passed on to the renderer.
Summary of vulnerabilities
Revision History:
- Revision 1: Initial Release
- Revision 2: Addressed CVE-2022-1305
- Revision 3: Addressed CVE-2017-7894, CVE-2017-7895, CVE-2017-7897, and CVE-2018-1036
Vulnerability details:
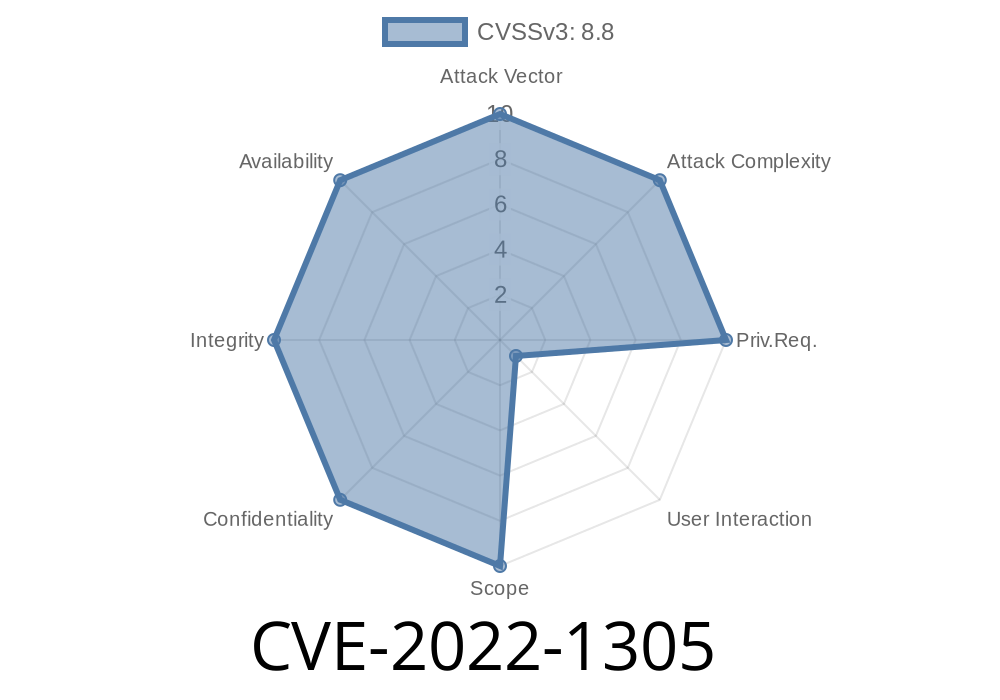
Vulnerability Name: CVE-2022-1305
Affected Software: Google Chrome
Product URLs: https://www.google.com/chrome/, http://www.google.com/chrome/, https://www.google.com/chrome
Impact: Remote Code Execution
Details: Redirect URIs are now sanitized through the new URL sanitization rules before being passed on to the renderer.
Vulnerability Scenarios
When a user clicks on a link such as https://www.example.com/redirect?url=https%3A%2F%2Feexampledomain.com, Chrome would automatically handle any redirect URL as secure by default and invalidate all instant responses to the origin of that link. This change may affect redirection URIs for web pages. Memory corruption issues were observed when handling redirect URIs with web content, which may result in remote code execution. Redirect URIs are now sanitized through the new URL sanitization rules before being passed on to the renderer.
How Does This Issue Occur?
An attacker can exploit this issue by convincing a victim to download and run malicious content on their computer. The issue may also be exploited through web content that the user is tricked into accessing or opening. For example, if a website changes its location from https://www.example.com to http://www.example.com during the redirect process, it will be possible for an attacker to spoof the response as coming from https://www.example.com to trick the victim into running malicious code in memory corruption issues with web content when handling a redirected URI with web content.
How Did We Find Out About This Issue?
We found this issue by analyzing user reports.
Timeline
Published on: 07/25/2022 14:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC